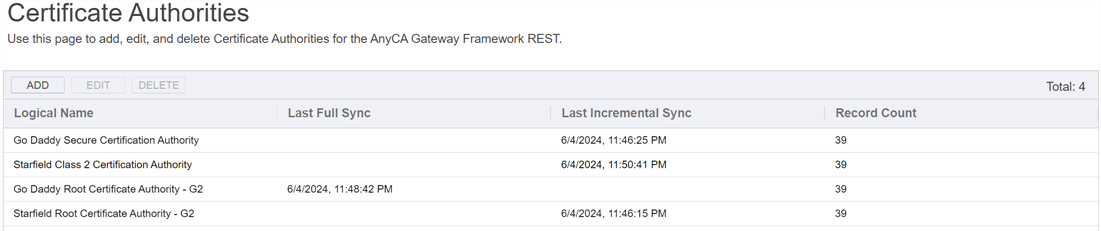
The Certificate Authorities page in the AnyCAGateway REST portal is used to add, edit or delete CAs in the AnyCA Gateway database.
Table 1148: Certificate Authorities Grid Columns
| Column | Description |
|---|---|
| Logical Name |
The logical name entered when the CA was added. |
| Last Full Sync | The date and time of the last full certificate synchronization from the third party CA. |
| Last Incremental Sync | The date and time of the last incremental certificate synchronization from the third party CA. |
| Record Count | The number of records synchronized between the gateway and the third-party CA. This could include certificates synchronized from the third-party CA, certificates enrolled through Keyfactor Command, and other records such as external validations. |
 Add or Edit a Certificate Authority
Add or Edit a Certificate Authority
- Navigate to the AnyCAGateway REST portal (see Working with the AnyCAGateway REST Portal).
- Select the Certificate Authorities tab.
- Select Add from the top menu bar, or highlight an existing CA and select Edit from the menu bar or the right click menu.
- Populate the certificate authority per the instructions for each tab below.
- Save.
For installations running under IIS, if a CA has a “+” (plus sign) in the logical name![]() The logical name of a CA is the common name given to the CA at the time it is created. For Microsoft CAs, this name can be seen at the top of the Certificate Authority MMC snap-in. It is part of the FQDN\Logical Name string that is used to refer to CAs when using command-line tools and in some Keyfactor Command configuration settings (e.g. ca2.keyexample.com\Corp Issuing CA Two)., you may encounter issues with the CA not displaying correctly in the AnyCAGateway REST portal, and you will not be able to modify or delete the CA record in the portal. To work around this:
The logical name of a CA is the common name given to the CA at the time it is created. For Microsoft CAs, this name can be seen at the top of the Certificate Authority MMC snap-in. It is part of the FQDN\Logical Name string that is used to refer to CAs when using command-line tools and in some Keyfactor Command configuration settings (e.g. ca2.keyexample.com\Corp Issuing CA Two)., you may encounter issues with the CA not displaying correctly in the AnyCAGateway REST portal, and you will not be able to modify or delete the CA record in the portal. To work around this:
- In the IIS Management Console, browse to locate the virtual application for the AnyCAGateway REST.
- Select it, and in the center panel open Request Filtering.
- In Request Filtering, select Edit Feature Settings... on the right.
- In the Edit Request Filtering Settings dialog, check the Allow double escaping box.
- In the AnyCAGateway REST portal, delete the CA record with the “+” character. For ease of ongoing management, you may wish to recreate it without a “+” character.
- In the Edit Request Filtering Settings dialog, uncheck the Allow double escaping box to disable this. You should not leave this option enabled, as it may create other issues.
The Basic Tab
-
Enter the Logical Name for the CA. This can be any name you choose. This will be used as the logical name of the CA in Keyfactor Command (see Working with the AnyCAGateway REST and Keyfactor Command).
Note: See the tip, above, about the use of the “+” character in CA logical names. -
Choose the Sync Settings intervals for full and incremental synchronizations between the gateway and the third-party CA. The synchronization between Keyfactor Command and the gateway is configured in Keyfactor Command.
Important: If you plan to use the gateway with Keyfactor Command, do not configure the synchronization to the third-party CA until you have completed configuration of the certificate profiles (see Certificate Profiles) and updated the Templates tab in the CA record with the profile to product ID mapping (see The Templates Tab). This profile to product ID information must be in place before the synchronization to the third-party CA occurs in order for the correct profiles to be mapped to the products when the certificates are stored in the gateway database. Keyfactor Command pulls from this data when synchronizing certificates into the Keyfactor Command database. If the mapping is not in place before both synchronizations take place, correct template A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. information for existing certificates will be missing from Keyfactor Command.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. information for existing certificates will be missing from Keyfactor Command. - The Ignore Failure Count defines how many synchronization failures can occur in a single synchronization before the synchronization stops trying. The default is 5.
-
The AnyGateway
 The Keyfactor AnyGateway is a generic third party CA gateway framework that allows existing CA gateways and custom CA connections to share the same overall product framework. REST supports the option to age out certificates with the Certificate Pruning setting. The default on this setting is Disabled. To enable certificate pruning, select either FromIssuance or FromExpiration from the dropdown. If Certificate Pruning is enabled, Age Out Days is required and this must be an integer greater than or equal to 0. Age Out Scan can be left as off, or a schedule can be set up—schedule options are Interval, Daily, Weekly or Monthly. If certificate pruning is set to Disabled, no pruning occurs.Note: If certificate pruning is set to FromIssuance or FromExpiration and the Age Out Scan is set to Off, certificates that meet the age-out criteria will be skipped during a synchronization. If there is a schedule configured for the scan, a job will be created to prune the certificates from the database based on the FromIssuance/FromExpiration and Age-Out Days settings. If the value is FromIssuance, the skip/pruning job will skip/remove certificate records whose issuance dates are older than the current date/time minus a number of days equal to Age Out Days. If the certificate record does not include an issuance date (e.g., a pending request), then it is ignored. If certificate pruning is set to FromExpiration, the same logic is applied to certificates according to their expiration date.
The Keyfactor AnyGateway is a generic third party CA gateway framework that allows existing CA gateways and custom CA connections to share the same overall product framework. REST supports the option to age out certificates with the Certificate Pruning setting. The default on this setting is Disabled. To enable certificate pruning, select either FromIssuance or FromExpiration from the dropdown. If Certificate Pruning is enabled, Age Out Days is required and this must be an integer greater than or equal to 0. Age Out Scan can be left as off, or a schedule can be set up—schedule options are Interval, Daily, Weekly or Monthly. If certificate pruning is set to Disabled, no pruning occurs.Note: If certificate pruning is set to FromIssuance or FromExpiration and the Age Out Scan is set to Off, certificates that meet the age-out criteria will be skipped during a synchronization. If there is a schedule configured for the scan, a job will be created to prune the certificates from the database based on the FromIssuance/FromExpiration and Age-Out Days settings. If the value is FromIssuance, the skip/pruning job will skip/remove certificate records whose issuance dates are older than the current date/time minus a number of days equal to Age Out Days. If the certificate record does not include an issuance date (e.g., a pending request), then it is ignored. If certificate pruning is set to FromExpiration, the same logic is applied to certificates according to their expiration date.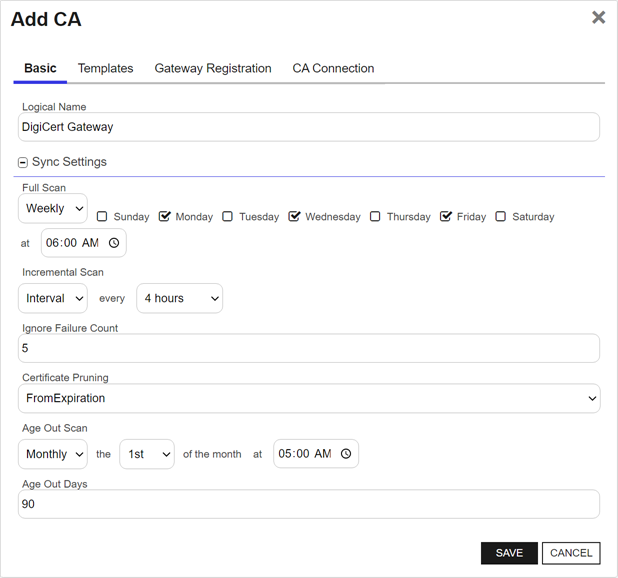
Figure 800: AnyCA Gateway Add CA: Basic Tab
The Templates Tab
-
Ensure you have created your certificate profiles before adding new templates (see Certificate Profiles).
-
Select the Certificate Profile from the drop down of those that have been configured on the Certificate Profiles page. Only Certificate Profiles not in use are shown.
-
Select the Product ID from the drop down to map to the selected certificate profile.
Note: The drop down has been pre-populated by the third-party CA integration DLL so the list will be specific to the particular CA provider.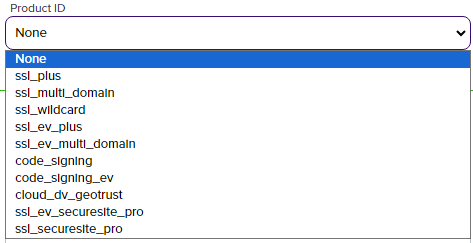
Figure 801: DigiCert Example of Populated Product ID
-
The Parameters are specific to the third party CA integration. The instructions provided with your integration artifact will include guidance as to how to populate any parameters that may be required/available.
 Show how to add or edit template parameter details.
Show how to add or edit template parameter details. -
Save the template.
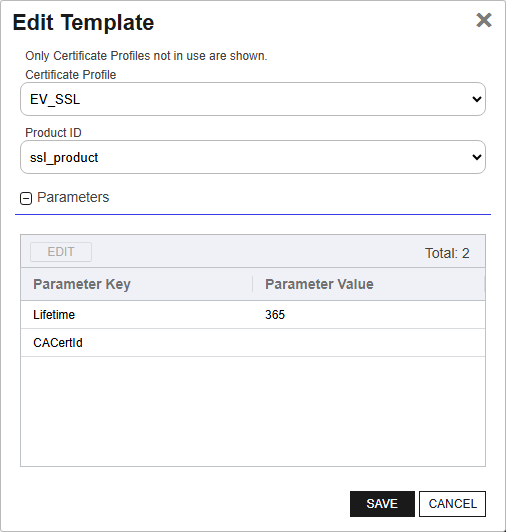
Figure 802: AnyCA Gateway Edit CA: Template Tab GoDaddy Example
-
Highlight the row, or click the check box, of the template you wish to delete.
Important: You will not receive a warning message. Deletion will be immediate. -
Click Delete.
The Gateway Registration Tab
On the Gateway Registration tab you configure the root or issuing CA certificate for the third-party CA that you identified during preparation (see Third-Party CA Certificate(s)). Ideally, the issuing CA certificate should be used. If you have more than one issuing CA certificate associated with certificates issued by your third-party CA, you will need to create separate CA records for each.
-
In the Certificate Type dropdown, select the certificate location, and fill in the details as required by the type selected.
-
The File Path option requires entry of the file path. The path provided must be relative to the install directory. For example:
.\configuration\ca-cert.pemIf the certificate is outside of the install directory an error will display when AnyCAGateway REST attempts to verify the certificate. You can View certificate by clicking the View Certificate button. Click Save to save the certificate.
-
The File Upload option displays an upload button which will open a file explorer window when clicked. Supported extensions are .der and .pem. Find and select the certificate you want to use. The dialog will populate with the certificate details. Click Save to save the certificate.
-
The Certificate Store option requires Store Name (e.g., CA for the intermediate certificate store), Store Location (e.g., LocalMachine), and Thumbprint. This is a reference to the store on the AnyCAGateway REST server. You can View certificate by clicking the View Certificate button. Click Saveto save the certificate.
Important: AnyCAGateway REST will analyze the certificate and add it to the configuration if the information is verified to be valid. -
The CA Connection Tab
-
The CA Connection tab requires different information for each third-party or custom gateway that integrates with the AnyCA Gateway. The properties required and values accepted are defined by the integration and configured here from the integration artifact. Complete as per the instructions provided by the third-party integration.
Note: For each additional CA added to the AnyCA Gateway implementation, you must have unique CA connection information from your third-party CA.Important: Any security sensitive information will be masked in the portal.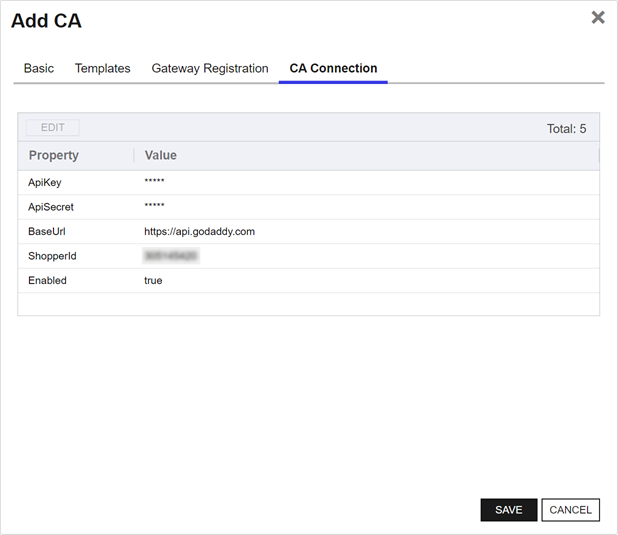
Figure 803: AnyCA Gateway Add CA: CA Connection Tab GoDaddy Example
- Click Save to save the CA
 Delete a Certificate Authority
Delete a Certificate Authority
- Navigate to the AnyCAGateway REST portal.
- Select the Certificate Authorities Tab.
- Highlight an existing CA and select Delete from the menu bar or the right click menu.
- Click OK.
Was this page helpful? Provide Feedback