If you plan to use the Keyfactor AnyCA Gateway REST with Keyfactor Command, once the AnyCAGateway REST configuration steps are complete, you must add the AnyCAGateway REST as a CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. and import and configure templates and create enrollment
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. and import and configure templates and create enrollment![]() Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). patterns in the Keyfactor CommandManagement Portal.
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). patterns in the Keyfactor CommandManagement Portal.
 Add the AnyCAGateway REST as a CA in Keyfactor Command
Add the AnyCAGateway REST as a CA in Keyfactor Command
- In the Keyfactor Command Management Portal, browse to Locations > Certificate Authorities.
- On the Certificate Authorities page, select the Certificate Authorities tab, and click Add.
- At the top of the dialog, choose HTTPS in the Select CA Communication Protocol dropdown.
- Complete the Certificate Authorities dialog following the guidance below and click Save and Test to save the CA. For more information about certificate authorities, see Adding or Modifying an HTTPS CA.
Certificate Authority Basic Tab
-
Logical Name—The logical name
 The logical name of a CA is the common name given to the CA at the time it is created. For Microsoft CAs, this name can be seen at the top of the Certificate Authority MMC snap-in. It is part of the FQDN\Logical Name string that is used to refer to CAs when using command-line tools and in some Keyfactor Command configuration settings (e.g. ca2.keyexample.com\Corp Issuing CA Two)., exactly as entered in AnyCAGateway REST portal (see The Basic Tab). The logical name is unique for each CA.
The logical name of a CA is the common name given to the CA at the time it is created. For Microsoft CAs, this name can be seen at the top of the Certificate Authority MMC snap-in. It is part of the FQDN\Logical Name string that is used to refer to CAs when using command-line tools and in some Keyfactor Command configuration settings (e.g. ca2.keyexample.com\Corp Issuing CA Two)., exactly as entered in AnyCAGateway REST portal (see The Basic Tab). The logical name is unique for each CA. -
Host URL— The Host URL is unique for each CA. The fully qualified domain name of the server on which the gateway is installed and the port number defined with the virtual directory followed by /EJBCA. For example:
https://keyfactor243.keyexample.com/AnyGatewayREST/ejbca. -
Configuration Tenant—Any name you want to use to identify the configuration tenant
 A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. for this CA.
A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. for this CA. -
Create new End Entity when renewing or reissuing certificates must be enabled. This is required.
-
Configure the Scan sync sections as desired. This is the sync between Keyfactor Command and AnyCAGateway REST.
Certificate Authority Advanced Tab
-
Configure the Enrollment section, ensuring Use for Enrollment is enabled to allow Keyfactor Command to use the gateway for enrollment.
Certificate Authority Authentication Methods Tab
-
Select the authentication method you configured for the AnyCAGateway REST in the Auth Method dropdown. The authentication method you select here must match the authentication method that the gateway has been configured with—you cannot configure the gateway with OAuth and then use a client authentication certificate to access it from Keyfactor Command, for example.
-
If you selected OAuth, enter the following information:
-
Client Id
The client you created in your OAuth identity provider to authenticate to the gateway and then added as a claim in the AnyCAGateway REST portal. See Claims.
-
Token URL
Set this to the URL of the token endpoint
 An endpoint is a URL that enables the API to gain access to resources on a server. for your OAuth identity provider.
An endpoint is a URL that enables the API to gain access to resources on a server. for your OAuth identity provider. -
Client Secret
The secret of the client you created in your OAuth identity provider to authenticate to the gateway. The secret may be stored as a Keyfactor secret or using PAM
 PAM (Privileged Access Management): Controls privileged access by vaulting credentials, enforcing least-privilege/just-in-time access, rotating secrets, and auditing sessions. Across Keyfactor products, PAM protects diverse sensitive operations and secrets—for example certificate stores and CA credentials—via built-in or third-party providers; external integrations are delivered as custom PAM extensions (several published on Keyfactor’s public GitHub).. For more information, see Adding or Modifying an HTTPS CA.
PAM (Privileged Access Management): Controls privileged access by vaulting credentials, enforcing least-privilege/just-in-time access, rotating secrets, and auditing sessions. Across Keyfactor products, PAM protects diverse sensitive operations and secrets—for example certificate stores and CA credentials—via built-in or third-party providers; external integrations are delivered as custom PAM extensions (several published on Keyfactor’s public GitHub).. For more information, see Adding or Modifying an HTTPS CA. -
Scope
One or more scopes that should be included in token requests delivered to your OAuth identity provider.
Important: If you configure the Disable Bearer Token Scope Requirement option to false (no), you must either configure the client you’re using to connect from Keyfactor Command to the gateway to always include the scope keyfactor-anyca-gateway in the token or you must configure the keyfactor-anyca-gateway scope on the authentication methods tab when configuring the CA record in Keyfactor Command. Your OAuth identity provider needs to be configured to recognize keyfactor-anyca-gateway as a scope. -
Audience
Specify an audience value to be included in token requests delivered to your OAuth identity provider.
-
-
If you selected Client Certificate, click Select Authentication Certificate. Upload—in PKCS#12
 A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. format—either the superadmin certificate or the certificate you created in the AnyCAGateway REST portal as a user account for the Keyfactor Command user (see Claims) and enter the password.Tip: Using a dedicated user certificate is preferable to using the superadmin certificate, as Keyfactor Command only needs user access to the AnyCAGateway REST.
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. format—either the superadmin certificate or the certificate you created in the AnyCAGateway REST portal as a user account for the Keyfactor Command user (see Claims) and enter the password.Tip: Using a dedicated user certificate is preferable to using the superadmin certificate, as Keyfactor Command only needs user access to the AnyCAGateway REST.
 Import Templates
Import Templates
Once the AnyCAGateway REST CA has been added to Keyfactor Command, you must import the gateway certificate profiles into Keyfactor Command as certificates templates.
- On the Templates page, click Import, and select the configuration tenant from the drop down, defined when you added the CA.
- Once the templates have been imported, configure each one to work with Keyfactor Command as required (see Edit).
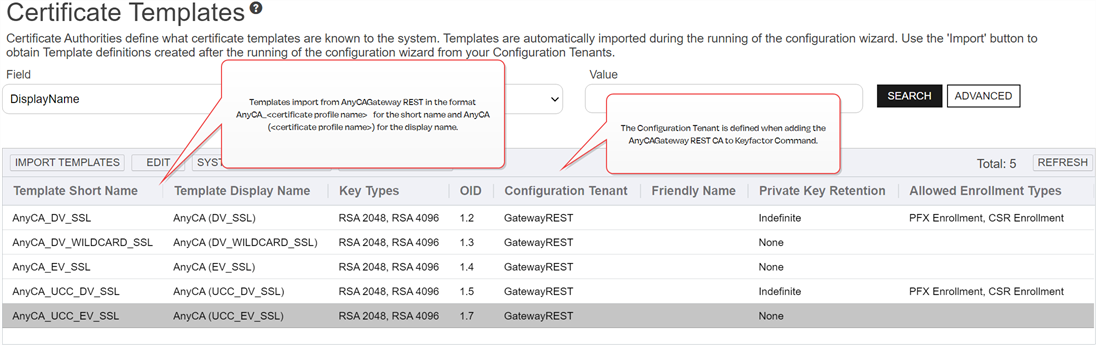
Figure 812: Keyfactor Command Management Portal - Certificate Templates Grid
 Add Enrollment Patterns
Add Enrollment Patterns
Once the certificate profiles have been imported into Keyfactor Command as templates, you must create enrollment patterns to use to enroll with the CA.
- In the Keyfactor Command Management Portal, browse to Locations > Enrollment Patterns.
- On the enrollment patterns grid, click Add to open the dialog to create an enrollment patterns for any templates you will use for enrollment (see Adding or Modifying an Enrollment Pattern).
- Settings on the Basic Information tab: Select at least one of the Allowed Enrollment Types to support enrollment.
- Disable Use AD Permissions and select at least one security role in Associated Roles.
- Save.
Was this page helpful? Provide Feedback