During installation, three claims are created to provide initial access to the AnyCAGateway REST portal. The client authentication certificate or OAuth credentials specified for the SuperAdmin parameter![]() A parameter or argument is a value that is passed into a function in an application. in the installation command are used to generate an admin, user and operator claim for the portal (see -SuperAdminValue). To accommodate different users, you can create additional claims using separate authentication certificates or OAuth credentials.
A parameter or argument is a value that is passed into a function in an application. in the installation command are used to generate an admin, user and operator claim for the portal (see -SuperAdminValue). To accommodate different users, you can create additional claims using separate authentication certificates or OAuth credentials.
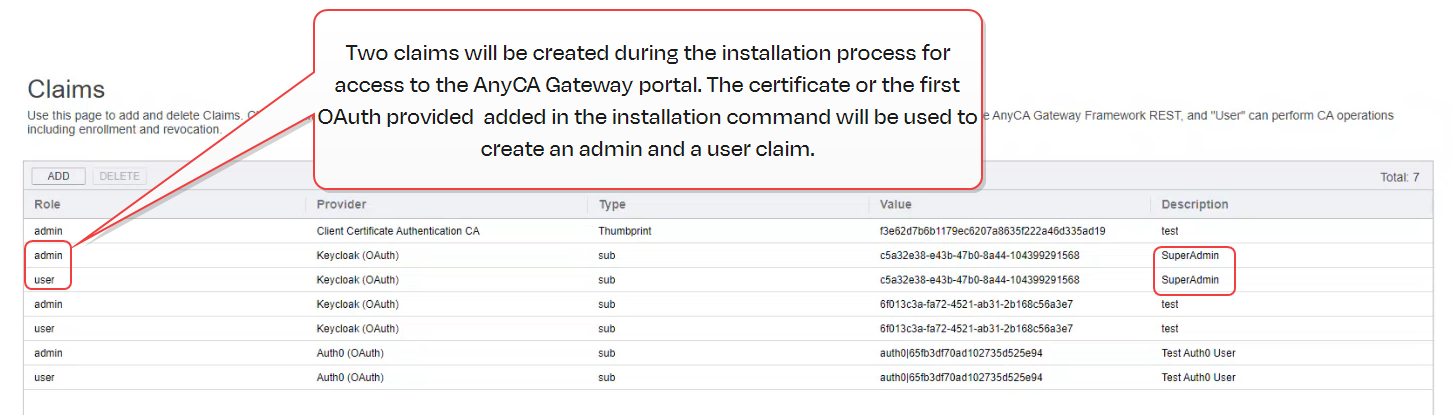
Figure 807: Claims Tab with OAuth Authentication
Roles
There are three roles available for assigning security on the AnyCAGateway REST portal.
-
Admin Role
Allows authorization to the gateway configuration API
 An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. as well as CA operations. Use this role for managers needing to make configuration changes through the AnyCAGateway REST portal.
An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. as well as CA operations. Use this role for managers needing to make configuration changes through the AnyCAGateway REST portal. -
User Role
Allows authorization to the CA operations API, which allows access to all of the operations of the AnyCAGateway REST, but no configuration access. Use this role for services and users needing access for enrollment, revocation, and synchronization. Users with only this role have no access to the AnyCAGateway REST portal.
-
Operator Role
Allows authorization to the AnyCAGateway REST portal, view or modify CAs, view or modify certificate profiles.
Claims
 View a Claim
View a Claim
To view an existing claim:
- Navigate to the AnyCAGateway REST portal.
- Select the Claims Tab.
- Double-click an existing claim to open the Claim Details.
- Click Close.
 Create a New Claim
Create a New Claim
To create a new claim:
- Navigate to the AnyCAGateway REST portal.
- Select the Claims Tab.
- Select Add from the menu bar.
- Select the Role for the claim from the drop down (Admin or User). See Roles.
-
Select the Provider for the claim.
The dropdown will be populated based on your installed IdP providers, either through the install script, the upgrade process, or through additional IdPs added via the API.
-
Client Certificate Authentication CA (Client Cert Auth) is the provider created by the AnyCA Gateway for client certificate authentication claims.
-
Auth0 is available to chose for the claim provider if an Auth0 IdP has been added.
-
Keycloak is an example of an installed Generic OAuth provider.
Tip: The provider name is defined as either Client Certificate Auth or the -IdentityProviderName parameter provided to the PowerShell install script.
-
- Enter a Description for the new claim. This might be the user, service account, or group name.
- Select how you want to identify the claim by choosing the claim Type. If you’re using client certificate authentication, you’ll be offered the choices of Thumbprint or Serial Number from the dropdown. If you’re using OAuth token authentication, this will be a text field in which you might enter sub or aud.
- Enter the security Value of the certificate or OAuth identity you want to use for this claim based on your selection for Type.
- Click Save.
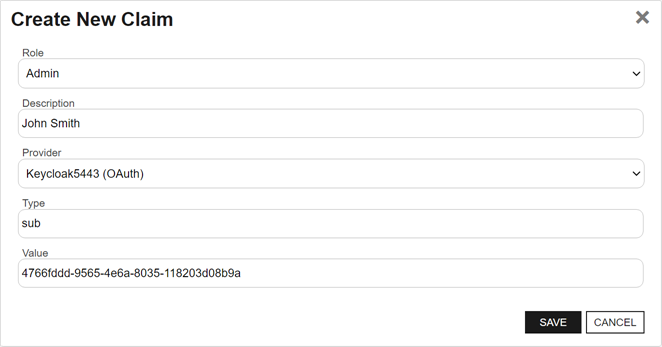
Figure 808: Add an OAuth Claim
 Delete a Claim
Delete a Claim
- Navigate to the AnyCAGateway REST portal.
- Select the Claims Tab.
-
Highlight an existing claim and select Delete from the menu bar or the right click menu.
Note: The SuperAdmin claim is required and cannot be deleted. - Click OK.
Was this page helpful? Provide Feedback