The Keyfactor Universal Orchestrator![]() The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers. supports client certificate authentication to allow you to authenticate via client certificates from individual orchestrator
The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers. supports client certificate authentication to allow you to authenticate via client certificates from individual orchestrator![]() Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. machines either directly or via a centralized proxy, such as a network load balancer, which would in turn authenticate to the Keyfactor Command server using either a username and password or client ID and secret that was stored securely on the proxy or another client certificate. The proxy approach allows orchestrator credentials to be assigned and managed outside the Active Directory forest
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. machines either directly or via a centralized proxy, such as a network load balancer, which would in turn authenticate to the Keyfactor Command server using either a username and password or client ID and secret that was stored securely on the proxy or another client certificate. The proxy approach allows orchestrator credentials to be assigned and managed outside the Active Directory forest![]() An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. in which Keyfactor Command is installed. The web proxy's job is to confirm the validity of the certificate and to provide Active Directory or an identity provider other than Active Directory credentials known to Keyfactor Command (if configured in this manner). Typically the proxy would be configured to accept all certificates issued from a given PKI
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. in which Keyfactor Command is installed. The web proxy's job is to confirm the validity of the certificate and to provide Active Directory or an identity provider other than Active Directory credentials known to Keyfactor Command (if configured in this manner). Typically the proxy would be configured to accept all certificates issued from a given PKI![]() A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. implementation—even a PKI that is unknown to the Keyfactor Command Active Directory forest—thus delegating orchestrator access control to that PKI. For more information, see:
A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. implementation—even a PKI that is unknown to the Keyfactor Command Active Directory forest—thus delegating orchestrator access control to that PKI. For more information, see:
- Appendix - Set up the Universal Orchestrator to Use Client Certificate Authentication Directly
- Appendix - Set up the Universal Orchestrator to Use Client Certificate Authentication via a Reverse Proxy: Citrix ADC
There are several situations in which using certificate authentication for the Universal Orchestrator may be helpful, including:
- Scale—To allow orchestrator numbers to scale (e.g. the IoT case) where it isn't practical to have a unique Active Directory account for each orchestrator.
- Untrusted Environments—To support environments (e.g. a “hostile” network) where policy doesn't allow the password for an Active Directory account to be stored on the orchestrator.
On Windows servers, the certificate may be referenced either as a PKCS12 file stored in the file system or may be placed either in the local machine's personal store (My), or, if you opt to run the Universal Orchestrator service as a domain service account rather than the default of Network Service, in the personal store of the Universal Orchestrator service account user. If you opt to place the certificate in the local machine store, you need to grant the service account under which the Universal Orchestrator service will run (including Network Service if you will use this option) read permissions to the private key of the certificate (see Grant the Service Account Certificate Private Key Permissions). If you opt to place the certificate in the personal store of the Universal Orchestrator service account user, it also needs to be placed in the personal store of the user running the installation for the duration of the installation to allow it to be read during initial configuration. It may be removed from the installing user's store after installation is complete.
On Linux servers, the certificate is referenced as a PKCS12 file stored in the file system.
Create a Template for Client Certificate Authentication
The certificate that the Universal Orchestrator uses for authentication needs:
- An extended key usage (EKU) of Client Authentication:
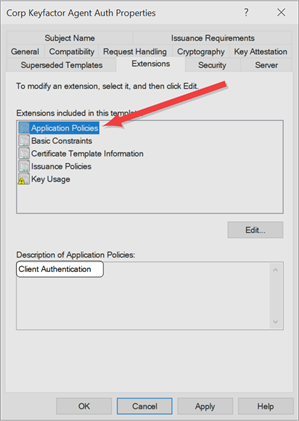
Figure 630: Microsoft Certificate Template Application Policies for Client Authentication Certificate
- A key usage that includes Digital Signature:
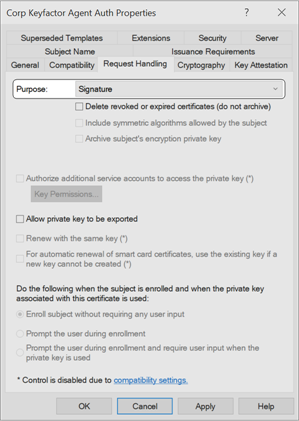
Figure 631: Microsoft Certificate Template Request Handling for Client Authentication Certificate
-
Depending on your method of implementation client certificate authentication, you may require Supply in the request for the Subject to ensure that your certificate has a value for the common name
 A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). (CN
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). (CN A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com).). The CN for your certificate appears in Keyfactor Command as the identity for your orchestrator when you use direct certificate authentication (see Appendix - Set up the Universal Orchestrator to Use Client Certificate Authentication Directly).
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com).). The CN for your certificate appears in Keyfactor Command as the identity for your orchestrator when you use direct certificate authentication (see Appendix - Set up the Universal Orchestrator to Use Client Certificate Authentication Directly).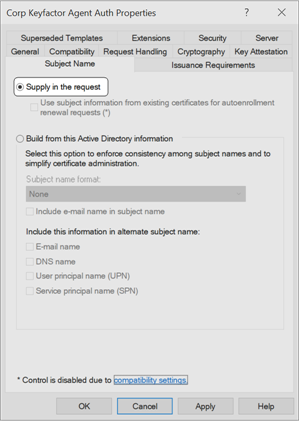
Figure 632: Microsoft: Certificate Template Subject Name for Client Authentication Certificate
Enroll for a Client Authentication Certificate
To acquire a certificate for use by the Universal Orchestrator using a Microsoft CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA., first create a template
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA., first create a template![]() A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. using the appropriate configurations as described above and make it available for enrollment on the CA from which you will request the certificate. If you plan to enroll for the certificate through Keyfactor Command, you will also need to enable the template for enrollment in Keyfactor Command. The account requesting the certificate will need enroll permissions on the CA, on the template, and, if applicable, in Keyfactor Command.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. using the appropriate configurations as described above and make it available for enrollment on the CA from which you will request the certificate. If you plan to enroll for the certificate through Keyfactor Command, you will also need to enable the template for enrollment in Keyfactor Command. The account requesting the certificate will need enroll permissions on the CA, on the template, and, if applicable, in Keyfactor Command.
You can enroll for a client authentication certificate for the orchestrator in a variety of ways. For an orchestrator on Windows, the certificate can either be installed in the local computer personal store on the Windows server on which the orchestrator is installed or provided as a PKCS#12![]() A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. file. For an orchestrator on Linux, the certificate must be provided as a PKCS#12 file. Some possible ways to do this are:
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. file. For an orchestrator on Linux, the certificate must be provided as a PKCS#12 file. Some possible ways to do this are:
-
Use Keyfactor Command to enroll for the certificate using the PFX
 A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. enrollment method and then import the PFX file on the orchestrator server. You can do this through the Keyfactor Command Management Portal or using the Keyfactor API
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. enrollment method and then import the PFX file on the orchestrator server. You can do this through the Keyfactor Command Management Portal or using the Keyfactor API An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. to submit a request (see PFX Enrollment in Keyfactor Command Using a PowerShell Script).
An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. to submit a request (see PFX Enrollment in Keyfactor Command Using a PowerShell Script). -
For an orchestrator on Windows, use IIS or the certificates MMC on the orchestrator server to generate a CSR, use the Keyfactor Command CSR enrollment method to enroll for a certificate using the CSR, and then import the certificate on the orchestrator server, marrying it with the private key generated on the server. You can do this through the Keyfactor Command Management Portal or using the Keyfactor API to submit a request.
-
For an orchestrator on Linux, use OpenSSL to generate a CSR, use the Keyfactor Command CSR enrollment method to enroll for a certificate using the CSR, and then copy the certificate to the orchestrator server, marrying it with the private key generated on the server. You can do this through the Keyfactor Command Management Portal or using the Keyfactor API to submit a request.
-
If there is an existing Universal Orchestrator on the server already running and communicating with Keyfactor Command, use the Keyfactor Command PFX enrollment method and push the certificate out to the certificate store on the orchestrator server using Keyfactor Command. You can do this through the Keyfactor Command Management Portal or using the Keyfactor API to submit a request (see PFX Enrollment and Deployment in Keyfactor Command Using a PowerShell Script).
-
For an orchestrator on Windows, use the Microsoft MMC on the Universal Orchestrator server to enroll for a certificate (see MMC Enrollment).
-
For an orchestrator on Windows, use the command-line certreq command with a request.inf file on the Universal Orchestrator server.
To enroll for a certificate using the MMC:
- On the Universal Orchestrator machine, do one of following:
- Using the GUI:
- Open an empty instance of the Microsoft Management Console (MMC).
- Choose File->Add/Remove Snap-in….
- In the Available snap-ins column, highlight Certificates and click Add.
- In the Certificates snap-in popup, choose the radio button for Computer account, click Next, accept the default of Local computer, and click Finish.
- Click OK to close the Add or Remove Snap-ins dialog.
- Using the command line:
- Open a command prompt using the “Run as administrator” option.
- Within the command prompt type the following to open the certificates MMC:certlm.msc
- Using the GUI:
- Drill down to the Personal folder under Certificates for the Local Computer, right-click, and choose All Tasks->Request New Certificate….
- Follow the certificate enrollment wizard, selecting the template you created for orchestrator certificate authentication and providing any required information.
To enroll for a certificate using the PFX enrollment method in Keyfactor Command, you can either do this in the Keyfactor Command Management Portal while logged in as the orchestrator service account or with a PowerShell script. In either case, the orchestrator service account will need PFX enroll permissions in Keyfactor Command. Below is a sample PowerShell script. For a Windows server, once the PFX file has been generated, import it into the local machine store on the orchestrator server.
#Set variables with the username and password for the orchestrator service account
$apiUsername = 'KEYEXAMPLE\APIUser'
$apiPassword = 'MySecureAPIAccountPassword'
$pair = "$($apiUsername):$($apiPassword)"
# Base-64 encode the service account credentials
$encodedCreds = [System.Convert]::ToBase64String([System.Text.Encoding]::ASCII.GetBytes($pair))
$UTCTime = (Get-Date).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ssZ")
$keyfactorServer = 'keyfactor.keyexample.com' # FQDN of the Keyfactor Command server
$caName = 'corpca01.keyexample.com\CorpIssuing01' # CA to use for the enrollment
$templateName = 'KeyfactorOrchestratorAuth' # Template to use for the enrollment
$certSubject = 'CN=orchname.keyexample.com' # Using a template that is configured to build from AD will cause this subject to be replaced
$pfxPassword = 'MySecurePFXPassword' # Password for the resulting PFX file
$outputFile = 'C:\stuff\OrchCertAuth.pfx' # Path and file name for the PFX file to be generated
$basicAuthValue = "Basic $encodedCreds"
$headers = @{
"Authorization"=$basicAuthValue
"Accept"="application/json"
"x-keyfactor-requested-with"="APIClient"
"x-certificateformat"="PFX"
}
$body = @{
"Password" = "$pfxPassword"
"Subject" = "$certSubject"
"IncludeChain" = "true"
"CertificateAuthority" = "$caName"
"Timestamp" = "$UTCTime"
"Template" = "$templateName"
}
# Output response as a PFX file
$response = Invoke-WebRequest -Uri "https://$keyfactorServer/KeyfactorAPI/Enrollment/PFX" -Method:Post -Headers $headers -ContentType "application/json" `
-Body ($body|ConvertTo-Json) -ErrorAction:Stop -TimeoutSec 60
$ResponseContent = $response.Content | ConvertFrom-Json
$bytes = [Convert]::FromBase64String($ResponseContent.CertificateInformation.Pkcs12Blob)
[IO.File]::WriteAllBytes($outputFile, $bytes)To enroll for a certificate using the PFX enrollment method in Keyfactor Command and deploy it to the orchestrator server using Keyfactor Command, you can either do this in the Keyfactor Command Management Portal while logged in as the orchestrator service account or with a PowerShell script. In either case, the orchestrator service account will need PFX enroll permissions and certificate store management permissions in Keyfactor Command. Below is a sample PowerShell script. This solution is only an option if your orchestrator is already up and running and successfully authenticating to Keyfactor Command using standard authentication (or previously configured certificate authentication).
#Set variables with the username and password for the orchestrator service account
$apiUsername = 'KEYEXAMPLE\APIUser'
$apiPassword = 'MySecureAPIAccountPassword'
$pair = "$($apiUsername):$($apiPassword)"
# Base-64 encode the service account credentials
$encodedCreds = [System.Convert]::ToBase64String([System.Text.Encoding]::ASCII.GetBytes($pair))
$UTCTime = (Get-Date).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ssZ")
$keyfactorServer = 'keyfactor.keyexample.com' # FQDN of the Keyfactor Command server
$storeName = 'websrvr38.keyexample.com' # FQDN of the orchestrator server as defined as a certificate store in Keyfactor Command
$caName = 'corpca01.keyexample.com\CorpIssuing01' # CA to use for the enrollment
$templateName = 'KeyfactorOrchestratorAuth' # Template to use for the enrollment
$certSubject = 'CN=orchname.keyexample.com' # Using a template that is configured to build from AD will cause this subject to be replaced
$basicAuthValue = "Basic $encodedCreds"
$enrollHeaders = @{
"Authorization"=$basicAuthValue
"Accept"="application/json"
"x-keyfactor-requested-with"="APIClient
"x-certificateformat"="Store"
}
$deployHeaders = @{
"Authorization"=$basicAuthValue
"Accept"="application/json"
"x-keyfactor-requested-with"="APIClient"
}
$enrollBody = @{
"Subject" = "$certSubject"
"IncludeChain" = "true"
"CertificateAuthority" = "$caName"
"Timestamp" = "$UTCTime"
"Template" = "$templateName"
}
# Enroll for a certificate using the PFX enrollment method and retrieve the certificate ID from the response (as part of the content)
$enrollResponse = Invoke-WebRequest -Uri "https://$keyfactorServer/KeyfactorAPI/Enrollment/PFX" -Method:Post -Headers $enrollHeaders -ContentType "application/json" `
-Body ($enrollBody|ConvertTo-Json) -ErrorAction:Stop -TimeoutSec 60
$enrollContent = $enrollResponse.Content | ConvertFrom-Json
# Get the store GUID for the certificate store specified by the client machine name in the query string with the storeName variable
$storeInfo = Invoke-WebRequest -Uri "https://$keyfactorServer/KeyfactorAPI/CertificateStores?certificateStoreQuery.queryString=ClientMachine%20-eq%20%22$storeName%22" `
-Method:Get -Headers $deployHeaders -ContentType "application/json" -ErrorAction:Stop -TimeoutSec 60
$storeContent = $storeInfo.Content | ConvertFrom-Json
$storeGUID = $storeContent.Id
$deployBody = @{
"StoreIds" = @( "$storeGUID" )
"StoreTypes" = @(
@{
"StoreTypeId" = 6 # Store type 6 is IIS personal
"Overwrite" = "false"
}
)
"CertificateId" = $enrollContent.CertificateInformation.KeyfactorId
}
# Deploy certificate to certificate store
Invoke-WebRequest -Uri "https://$keyfactorServer/KeyfactorAPI/Enrollment/PFX/Deploy" -Method:Post -Headers $deployHeaders -ContentType "application/json" `
-Body ($deployBody|ConvertTo-Json) -ErrorAction:Stop -TimeoutSec 60Grant the Service Account Certificate Private Key Permissions
Whichever method you decide to use to acquire the client authentication certificate for a Windows orchestrator, if you’ve installed the certificate in the local machine store on the server, you will need to grant the Universal Orchestrator service account—the account that the orchestrator service is running as on the server—permissions to read the private key of that certificate.
To grant private key permissions on the certificate using the MMC:
- On the Universal Orchestrator machine, do one of following:
- Using the GUI:
- Open an empty instance of the Microsoft Management Console (MMC).
- Choose File->Add/Remove Snap-in….
- In the Available snap-ins column, highlight Certificates and click Add.
- In the Certificates snap-in popup, choose the radio button for Computer account, click Next, accept the default of Local computer, and click Finish.
- Click OK to close the Add or Remove Snap-ins dialog.
- Using the command line:
- Open a command prompt using the “Run as administrator” option.
- Within the command prompt type the following to open the certificates MMC:certlm.msc
- Using the GUI:
- Drill down to the Personal folder under Certificates for the Local Computer to locate the certificate.
- Highlight the certificate and choose All Tasks->Manage Private Keys….
- In the Permissions for private keys dialog, click Add, add the service account under which the Universal Orchestrator is running (created as per Create Service Accounts for the Universal Orchestrator), and grant that service account Read but not Full control permissions. Click OK to save.
Confirm that the orchestrator server trusts the root and issuing certificates for the SSL
 TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate on the Keyfactor Command server and the client authentication certificate you are trying to use (see Configure Certificate Root Trust for the Universal Orchestrator).
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate on the Keyfactor Command server and the client authentication certificate you are trying to use (see Configure Certificate Root Trust for the Universal Orchestrator).Confirm that the orchestrator server has access to the CRLs for both the SSL certificate on the Keyfactor Command server and the client authentication certificate you are trying to use and that these CRLs are valid.
Confirm that you have granted the service account under which the orchestrator service runs private key permissions on the client authentication certificate.
Was this page helpful? Provide Feedback