The cornerstones of the Keyfactor Command Management Portal are the Certificate Search and the Certificate Details pages. The Certificate Details page includes a comprehensive set of details about each certificate managed by Keyfactor Command. To access a certificate's details, double-click on a row of the certificate search grid, or highlight a row, right click and select Edit (Display for users with only Read permissions) from the action menu (see Certificate Search Page).
The following action buttons are conveniently located at the top of the Certificate Details page for users with the appropriate permissions: Revoke, Download, Renew. See Certificate Operations for more information on these actions.
 Content Tab
Content Tab
The Content tab shows the certificate attributes from the CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. (Active Directory in the case of a Microsoft CA). These fields are not editable. The list of Subject Alternative Names (SANs) and SAN
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. (Active Directory in the case of a Microsoft CA). These fields are not editable. The list of Subject Alternative Names (SANs) and SAN![]() The subject alternative name (SAN) is an extension to the X.509 specification that allows you to specify additional values when enrolling for a digital certificate. A variety of SAN formats are supported, with DNS name being the most common. count are also included on this tab. For an ECC
The subject alternative name (SAN) is an extension to the X.509 specification that allows you to specify additional values when enrolling for a digital certificate. A variety of SAN formats are supported, with DNS name being the most common. count are also included on this tab. For an ECC![]() Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller, and more efficient cryptographic keys. ECC generates keys through the properties of the elliptic curve equation instead of the traditional method of generation as the product of very large prime numbers. certificate, the elliptic curve algorithm is included on this tab.
Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller, and more efficient cryptographic keys. ECC generates keys through the properties of the elliptic curve equation instead of the traditional method of generation as the product of very large prime numbers. certificate, the elliptic curve algorithm is included on this tab.
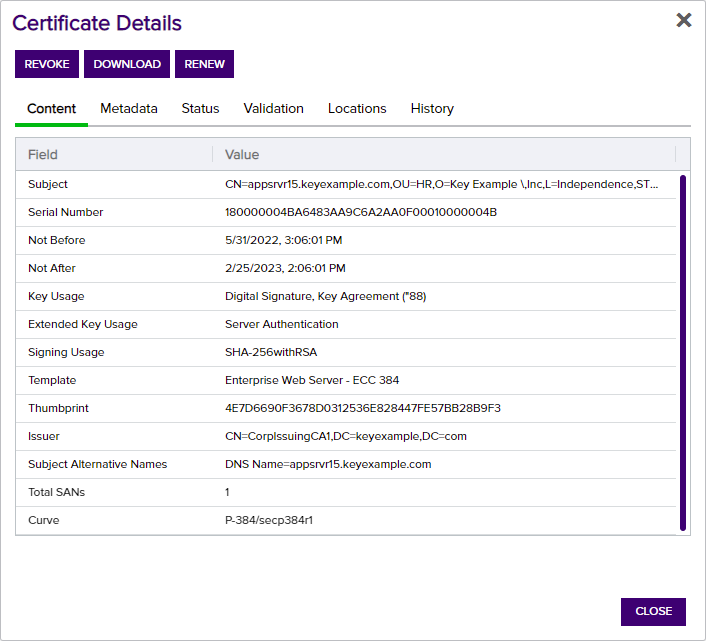
Figure 21: Certificate Details: Content Tab
 Metadata Tab
Metadata Tab
The Metadata![]() Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. tab displays all metadata fields created for your Keyfactor Command implementation and shows any data in fields that have been populated with values specific to the certificate. Depending on the metadata type, these fields appear as text boxes, radio buttons, drop-downs, date fields, table or large text fields.
Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. tab displays all metadata fields created for your Keyfactor Command implementation and shows any data in fields that have been populated with values specific to the certificate. Depending on the metadata type, these fields appear as text boxes, radio buttons, drop-downs, date fields, table or large text fields.
For users with edit permissions, on date fields a small popup calendar will appear that will allow you to select a date and will properly format it for you. You may edit values for any metadata fields to update the data at any time. You may also update multiple certificates' metadata with the same data by selecting multiple certificates from the certificates grid. Required fields will be marked with *Required next to the field label. See Certificate Metadata for information on this functionality.
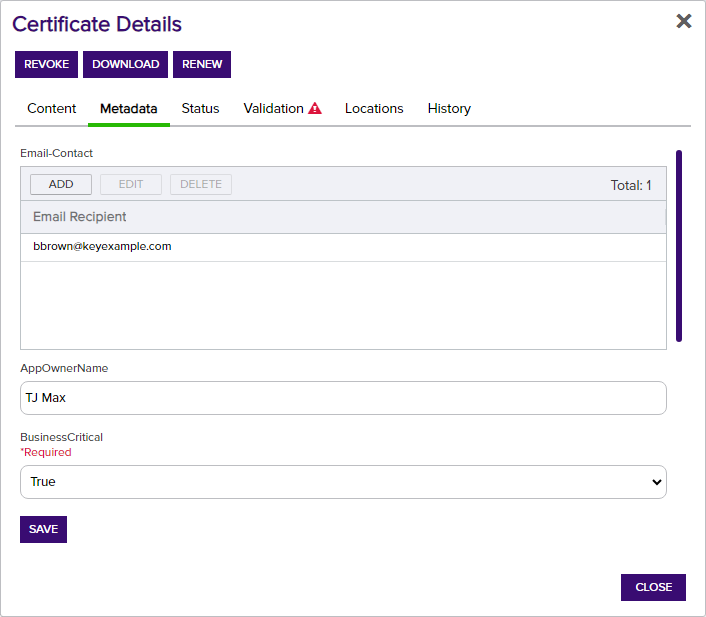
Figure 22: Certificate Details: Metadata Tab
The email metadata type will display a grid with the list of email addresses associated with the certificate(s). Grid action options of Add, Edit and Delete are included.
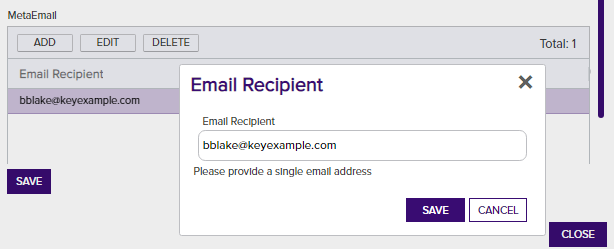
Figure 23: Email Type Metadata
 Status Tab
Status Tab
The status tab displays some additional information about the certificate (see Table 3: Status Tab Descriptions).
The fields on this tab cannot be edited.
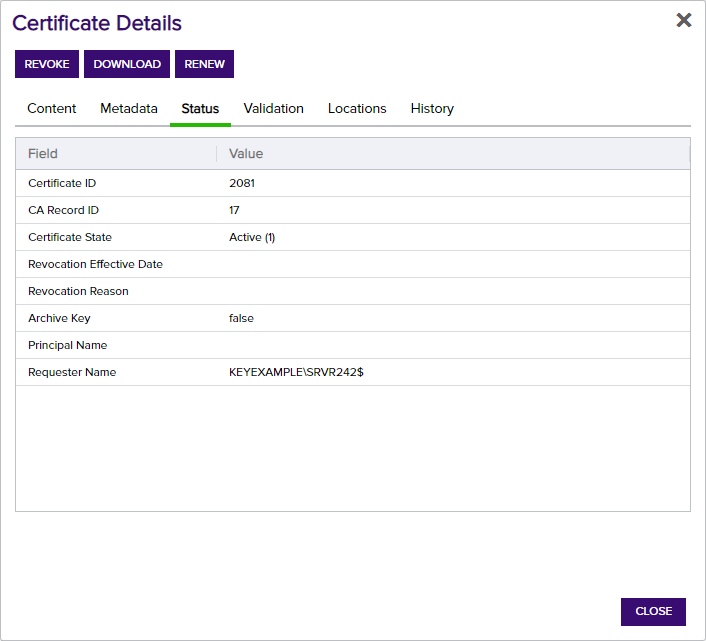
Figure 24: Certificate Details: Status Tab
Table 3: Status Tab Descriptions
| Field | Description |
|---|---|
| Certificate ID | The Keyfactor Command reference ID for the certificate, which can be useful when referring to the certificate using API methods. |
| CA Record ID | The ID of the certificate in the CA (this has replaced CARequestID). |
| Certificate State |
The state of the certificate.
|
| Revocation Effective Date | If the certificate is revoked, the date it was revoked will be displayed here. |
| Revocation Reason |
If the certificate is revoked, the reason will be displayed here. This is shown as a numeric value, which will be one of:
See Revoke for more information about revoking certificates. |
| Archive Key |
If true, the certificate has a private key archived on the Microsoft CA to support CA key recovery. This flag is not an indicator for whether the certificate has a private key stored in Keyfactor Command. Tip: CA-level key recovery is supported for Microsoft CAs to allow recovery of private keys for certificates enrolled outside of Keyfactor Command. CA-level key archiving is not supported for enrollments done through Keyfactor Command. CA-level key recovery is not supported for EJBCA CAs. For enrollments done through Keyfactor Command for either Microsoft or EJBCA CAs, use Keyfactor Command private key retention (see Details Tab).
|
| Principal Name | The user principal name (UPN) contained in the subject alternative name (SAN) field of the certificate, if present (e.g. username@keyexample.com). |
| Requester Name | The name of the requester in DOMAIN\User format. |
 Validation Tab
Validation Tab
This tool will report on the certificate validity based on the criteria defining the status of an X509 chain shown in Table 4: Validation Tab Descriptions. This tab replaces the former Validate action from the certificate search grid. An alert symbol will show on the tab header if one or more tests have a result of Fail.
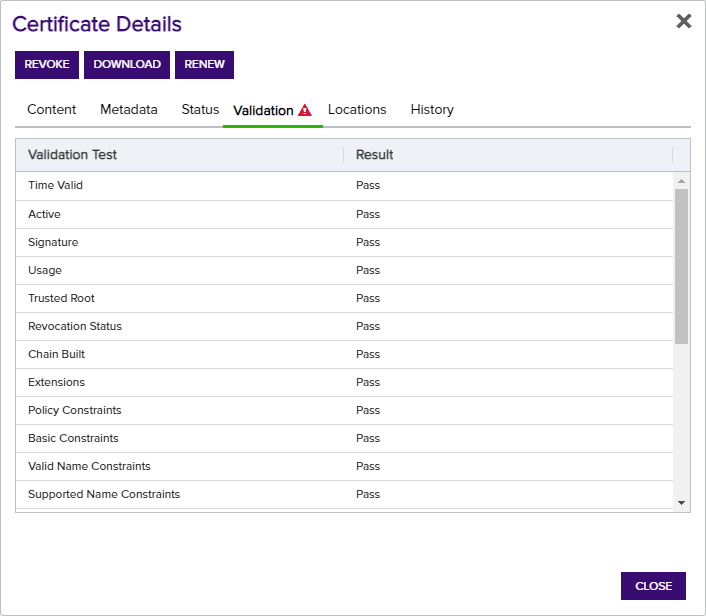
Figure 25: Certificate Details: Validation Tab
Table 4: Validation Tab Descriptions
| Validation Test | Keyfactor API Equivalent1 | Definition |
|---|---|---|
| Time Valid | NotTimeValid | A value of Pass indicates that the certificate time value is valid. A time can appear invalid (Fail) for a certificate that has expired. |
| Active | Revoked | A value of Pass indicates that the X509 certificate chain is valid for the certificate and contains no revoked certificates or errors. |
| Signature | NotSignatureValid | A value of Fail indicates that the X509 certificate chain is invalid as a result of an invalid certificate signature. |
| Usage | NotValidForUsage | A value of Fail indicates that the X509 certificate chain is invalid as a result of an invalid key usage. |
| Trusted Root | UntrustedRoot | A value of Fail indicates that the X509 certificate chain is invalid as a result of an untrusted root certificate. |
| Revocation Status | RevocationStatusUnknown | A value of Pass indicates that the revocation status can successfully be determined for the certificate. This may be the result of successful access to online certificate revocation lists (CRLs) and, if configured, authority information access (AIA) endpoints. |
| Chain Built | Cyclic | A value of Pass indicates that the certificate chain for the certificate could successfully be built. |
| Extensions | InvalidExtension | A value of Fail indicates that the X509 certificate chain is invalid as a result of an invalid extension. |
| Policy Constraints | InvalidPolicyConstraints | A value of Fail indicates that the X509 certificate chain is invalid as a result of an invalid policy constraint. |
| Basic Constraints | InvalidBasicConstraints | A value of Fail indicates that the X509 certificate chain is invalid as a result of an invalid basic constraint. |
| Valid Name Constraints | InvalidNameConstraints | A value of Fail indicates that the X509 certificate chain is invalid as a result of an invalid name constraint. |
| Supported Name Constraints | HasNotSupportedNameConstraint | A value of Fail indicates that a name constraint for the certificate is unsupported or that the certificate has no supported name constraints. |
| Defined Name Constraints | HasNotDefinedNameConstraint | A value of Fail indicates that a name constraint for the certificate is undefined. |
| Permitted Name Constraints | HasNotPermittedNameConstraint | A value of Fail indicates that a name constraint for the certificate is impermissible. |
| Excluded Name Constraints | HasExcludedNameConstraint | A value of Fail indicates that a name constraint for the certificate has been excluded. |
| Full Chain | PartialChain | A value of Pass indicates that the certificate chain for the certificate could successfully be built up to the root certificate. |
| CTL Time Valid | CtlNotTimeValid | A value of Fail indicates that the certificate trust list (CTL) is invalid because of an invalid time value (e.g. the CTL has expired). |
| CTL Signature Valid | CtlNotSignatureValid | A value of Fail indicates that the certificate trust list (CTL) contains an invalid signature. |
| CTL Usage Valid | CtlNotValidForUsage | A value of Fail indicates that the certificate trust list (CTL) is not valid for this use. |
| Strong Signature | HasWeakSignature | A value of Pass indicates that the certificate has been signed with a secure hashing algorithm. A value of Fail can indicate that a hashing algorithm of MD2 or MD5 was used for the certificate. |
| CRL online | OfflineRevocation | A value of Pass indicates that the online certificate revocation list (CRL) the chain relies on is available. |
| Chain Policy | NoIssuanceChainPolicy | A value of Pass indicates that there is either no certificate policy by design in the certificate or that if a group policy has specified that all certificates must have a certificate policy, the certificate policy exists in the certificate. |
| No Explicit Distrust | ExplicitDistrust | A value of Pass indicates that the certificate is not explicitly distrusted. |
| Critical Extensions | HasNotSupportedCriticalExtension | A value of Pass indicates that the certificate has a critical extension that is supported or has no critical extensions. |
 Locations Tab
Locations Tab
If you have added the certificate to any certificate store location(s) a number will appear in the Count column on the corresponding Location Type row. Users with limited permissions will only see locations for types of certificate stores to which they have been granted permissions either globally or via certificate store containers (see Container Permissions). Click the count number for more details regarding this certificate's location. See Add to Certificate Store for more information. The Total Cert Store Locations appears at the end of the list. Clicking on the total will open a dialog with the list of locations with the columns: Store Path, Store Machine, Alias, IPAddress, Port, and Agent Pool which will be populated depending on the details of the individual stores.
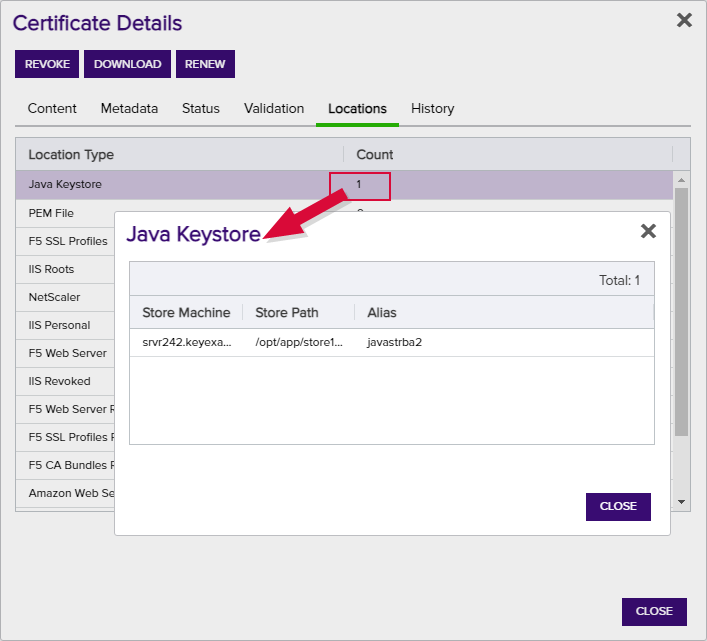
Figure 26: Location Details
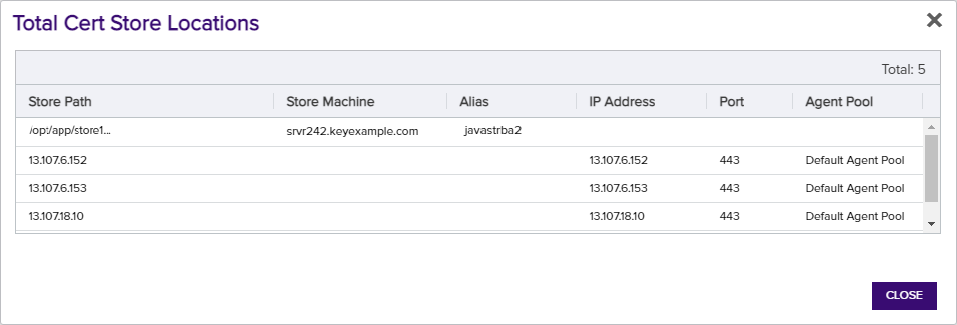
Figure 27: Total Certificate Store Location Details
 History Tab
History Tab
History about a certificate is recorded in the Keyfactor Command database for the following types of activities (see also Audit Log):
- Initial Import—A history entry is made on import via CA synchronization, SSL synchronization, certificate store synchronization or manual import.
- Certificate Enrollment
 Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA).—A history entry is made when a PFX
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA).—A history entry is made when a PFX A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. or CSR
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. or CSR A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment is completed through the Keyfactor Command Management Portal. The source of the request (PFX or CSR) is indicated.
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment is completed through the Keyfactor Command Management Portal. The source of the request (PFX or CSR) is indicated. - Revocation—A history entry is made each time a certificate is revoked, so if a certificate is revoked multiple times, there will be multiple history entries.
- Key Recovery—A history entry is made each time the key for a certificate is recovered, so if the key for a given certificate is recovered multiple times, there will be multiple history entries. This type of record is generated when the private key
 Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. for a certificate is downloaded from the Keyfactor Command database or when a private key is recovered from a CA using the CA's key recovery mechanism.
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. for a certificate is downloaded from the Keyfactor Command database or when a private key is recovered from a CA using the CA's key recovery mechanism. - Certificate Store Additions and Removals—A history entry is made each time a certificate is added to a certificate store or removed from a certificate store. These entries reference the specific certificate store type and whether the operation was an addition or removal—Add ([store type]) and Remove ([store type])—and include details in the certificate history comments.
- Certificate Renewals—A history entry is made each time a certificate is renewed or reissued. The certificate renewal history record appears on both the old certificate (renewed from) and the new renewed certificate.
- Certificate Store Inventory Discoveries—A history entry is made each time an inventory of a certificate store notices that a certificate that was in a certificate store no longer is or that a new certificate has appeared in the certificate store. These entries are referenced as Certificate Appeared ([store type]) and Certificate Disappeared ([store type]) with details in the certificate history comments.
- SSL Endpoint
 An endpoint is a URL that enables the API to gain access to resources on a server. Inventory Discoveries—A history entry is made each time an inventory of an SSL endpoint notices that a certificate that was at an endpoint no longer is or that a new certificate has appeared at an endpoint during a monitoring task. These entries are referenced as Certificate Appeared (SSL Sync) and Certificate Disappeared (SSL Sync) with details in the certificate history comments.
An endpoint is a URL that enables the API to gain access to resources on a server. Inventory Discoveries—A history entry is made each time an inventory of an SSL endpoint notices that a certificate that was at an endpoint no longer is or that a new certificate has appeared at an endpoint during a monitoring task. These entries are referenced as Certificate Appeared (SSL Sync) and Certificate Disappeared (SSL Sync) with details in the certificate history comments. - Metadata Updated—A history entry is made each time a metadata field is updated for the certificate. The changed data will be recorded in the Comment field.

Figure 28: Certificate Operation: Certificate History Tab
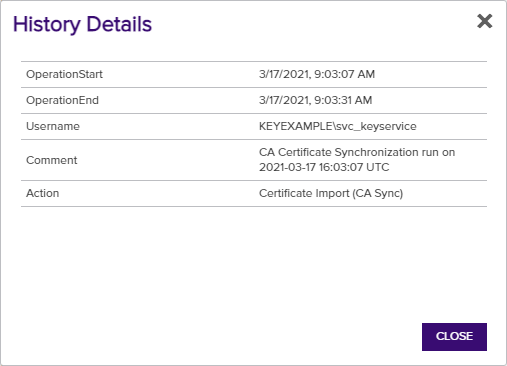
Figure 29: Certificate Operation: Certificate History Detail