The Keyfactor Cloud Gateway provides the option to implement multiple gateways using clustering for a highly available and redundant implementation. This option relies on Microsoft Failover Clustering and a shared storage solution (such as a NAS).
Configuration of network attached storage and failover clustering is beyond the scope of this guide.
Failover clustering with shared storage must be in place before you begin installation of any of the gateway nodes.
In addition to the general preparing and implementing steps described for the gateway as a whole, the process for implementing the gateway with clustering has some specific requirements and processes. The following is a general overview of the process:
- Ready the NAS and prepare quorum and storage disks for the gateway cluster.
- Give each gateway server a NIC on the NAS network.
-
Install the Microsoft Failover Clustering role on each server that will host a gateway and create the failover cluster:
- Acquire an encryption certificate for gateway clustering, distribute it to all cluster nodes, and grant permissions on its private key
 Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. on all nodes (see Acquire and Distribute a Gateway Encryption Certificate).
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. on all nodes (see Acquire and Distribute a Gateway Encryption Certificate). - If you will be using an enrollment
 Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). agent certificate for CSR
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). agent certificate for CSR A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. validation, acquire it, distribute it to all the cluster nodes, and grant permissions on its private key on all nodes (see Configure the Enrollment Agent Certificate (Optional)).
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. validation, acquire it, distribute it to all the cluster nodes, and grant permissions on its private key on all nodes (see Configure the Enrollment Agent Certificate (Optional)). - Install the chain certificates from the managed forest
 An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. CA
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. CA A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. on all the nodes (see Acquire and Install a Chain Certificate).
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. on all the nodes (see Acquire and Install a Chain Certificate). - Install the Keyfactor Cloud Gateway on each server that will host a gateway but do not run the configuration wizard (see Installing).
- In the Microsoft Failover Cluster Manager, create a role for the main gateway service (see Create a Role for the Keyfactor Managed CA Gateway).
- In the Microsoft Failover Cluster Manager, make sure that the node where you are going to run the configuration wizard is the active node.
- Run the Keyfactor Cloud Gateway configuration wizard on the active node and complete the configuration as normal (see Installing), including the information on the Clustering tab.
- In the Microsoft Failover Cluster Manager, update the role to add a resource for the gateway sync service (see Add a Resource for the Keyfactor Managed CA Sync Service) if you're using this feature.
- You may wish to modify logging to send logs to the shared storage (see Configure Logging).
If you run into issues at any point in the process, refer to the Windows event log, which may contain more information than can be found in the Failover Cluster Manager, and the Keyfactor gateway log (see Configure Logging).
Acquire and Distribute a Gateway Encryption Certificate
The gateway uses a certificate to encrypt the username and password used to access the CA in the managed forest. This can be a certificate generated from a Microsoft CA in either your local forest or your managed forest or a certificate purchased from a certificate vendor. The certificate needs to have a key usage of key encipherment or data encipherment and use RSA![]() A widely used public-key cryptosystem, RSA is commonly used for encryption and digital signatures. It is based on the mathematical difficulty of factoring large integers. encryption. An extended key usage (EKU) of Server Authentication would be typical but not required.
A widely used public-key cryptosystem, RSA is commonly used for encryption and digital signatures. It is based on the mathematical difficulty of factoring large integers. encryption. An extended key usage (EKU) of Server Authentication would be typical but not required.
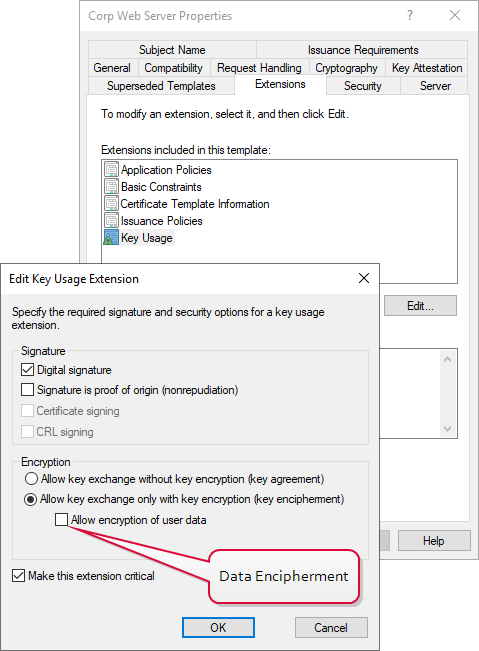
Figure 716: Gateway Encryption Certificate Should Support Key Encipherment or Data Encipherment
Keyfactor recommends using the PFX![]() A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. Enrollment function in your managed Keyfactor Command instance to enroll for the certificate and download the certificate with associated private key as a PFX file. Contact Keyfactor support if you need assistance locating an appropriate template
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. Enrollment function in your managed Keyfactor Command instance to enroll for the certificate and download the certificate with associated private key as a PFX file. Contact Keyfactor support if you need assistance locating an appropriate template![]() A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. for this.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. for this.
Once you have your certificate with associated private key in a PFX file, securely copy this PFX file to each cluster node, install it in the local machine store and grant permissions as follows:
- On each gateway node, do one of following:
Using the GUI:
Open an empty instance of the Microsoft Management Console (MMC).
Choose File->Add/Remove Snap-in….
In the Available snap-ins column, highlight Certificates and click Add.
In the Certificates snap-in popup, choose the radio button for Computer account, click Next, accept the default of Local computer, and click Finish.
Click OK to close the Add or Remove Snap-ins dialog.
Using the command line:
Open a command prompt using the “Run as administrator” option.
Within the command prompt type the following to open the certificates MMC:
certlm.msc
- Drill down to the Personal folder under Certificates for the Local Computer, right-click, and choose All Tasks->Import….
- Follow the certificate import wizard, selecting your PFX and entering the password for the PFX.
- When the import completes, locate the certificate in the Personal store (you may need to refresh), highlight it, and choose All Tasks->Manage Private Keys….
- In the Permissions for private keys dialog, click Add, add Network Service, and grant it Read but not Full control permissions. Click OK to save.
Create a Role for the Keyfactor Managed CA Gateway
The role for the main gateway service is created part way through the implementation after the gateway product is installed but before it has been configured with the configuration wizard.
To create the role:
- On the gateway server that is the active node in the failover cluster, open the Failover Cluster Manager.
- In the Failover Cluster Manager, drill down to Roles and click Configure Role... in the Actions pane.
- On the Select Role page of the High Availability Wizard, choose Generic Service and click Next.
- On the Select Service page, scroll down to locate the Keyfactor Managed CA Gateway service.
- On the Client Access Point page, give the gateway cluster a meaningful Name of not more than 15 characters (e.g., CloudGateway) and enter an available IP address that can be associated with this DNS
 The Domain Name System is a service that translates names into IP addresses. name.
The Domain Name System is a service that translates names into IP addresses. name. - On the Select Storage page, select the storage disk(s) you prepared for the gateway cluster.
-
On the Replicate Registry Settings page, click Add and in the Registry Key popup, enter the following to complete the configured registry key:
SOFTWARE\Keyfactor\Keyfactor CA Gateway\Parameters -
Accept the defaults for the remainder of the wizard and click Finish at the end to create the role.
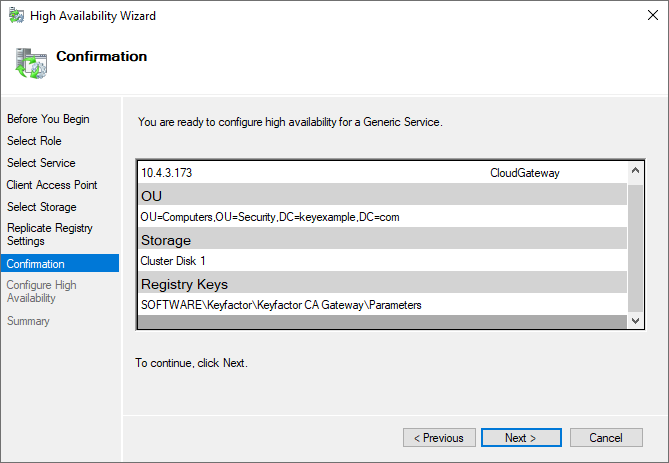
Figure 717: Configure a Cluster Role
- In the Failover Cluster Manager, confirm that the new role has started successfully and shows a status of Running.
Add a Resource for the Keyfactor Managed CA Sync Service
The resource for the sync service can be added immediately after the role is created or after configuration is complete and is only needed if you choose to configure synchronization of certificate templates or Active Directory user and group accounts from the local forest to the managed forest. Template synchronization is done to support certificate enrollment with the gateway (see Create or Identify Templates). Accounts synchronized to the managed environment can used to support access control with federated single sign-on to the Keyfactor Command instance in the managed environment (see Create or Identify Accounts for Synchronization (Optional)).
To add a resource:
- On the gateway server that is the active node in the failover cluster, open the Failover Cluster Manager.
- In the Failover Cluster Manager, drill down to Roles and select the role you created for the main gateway service (see Create a Role for the Keyfactor Managed CA Gateway).
- In the Actions pane, choose Add Resource - > Generic Service.
- On the Select Service page, scroll down to locate the Keyfactor Managed CA Sync Service and click Next.
- Accept the defaults for the remainder of the wizard and click Finish at the end to associate the sync service with the role.
- In the Failover Cluster Manager, confirm that the role has started successfully with the new service and shows a status of Running for all services.
Was this page helpful? Provide Feedback