Architecture
The components that make up a Keyfactor SCEP implementation include:
-
Keyfactor SCEP Server
The server runs under IIS and requires ASP.NET (4.5 or higher).
-
Certificate Authority
For issuing certificates.
-
Keyfactor Command
For managing, monitoring, and reporting on certificates.
-
Microsoft SQL Server (Optional)
If desired, challenge passwords and configuration information can be stored in a SQL database rather than the default local Jet database.
-
Microsoft Intune (Optional)
For managing delivery of certificates to devices.
-
Web Reverse Proxy (Optional)
Used if devices will be contacting the Keyfactor SCEP server from outside the enterprise firewall.
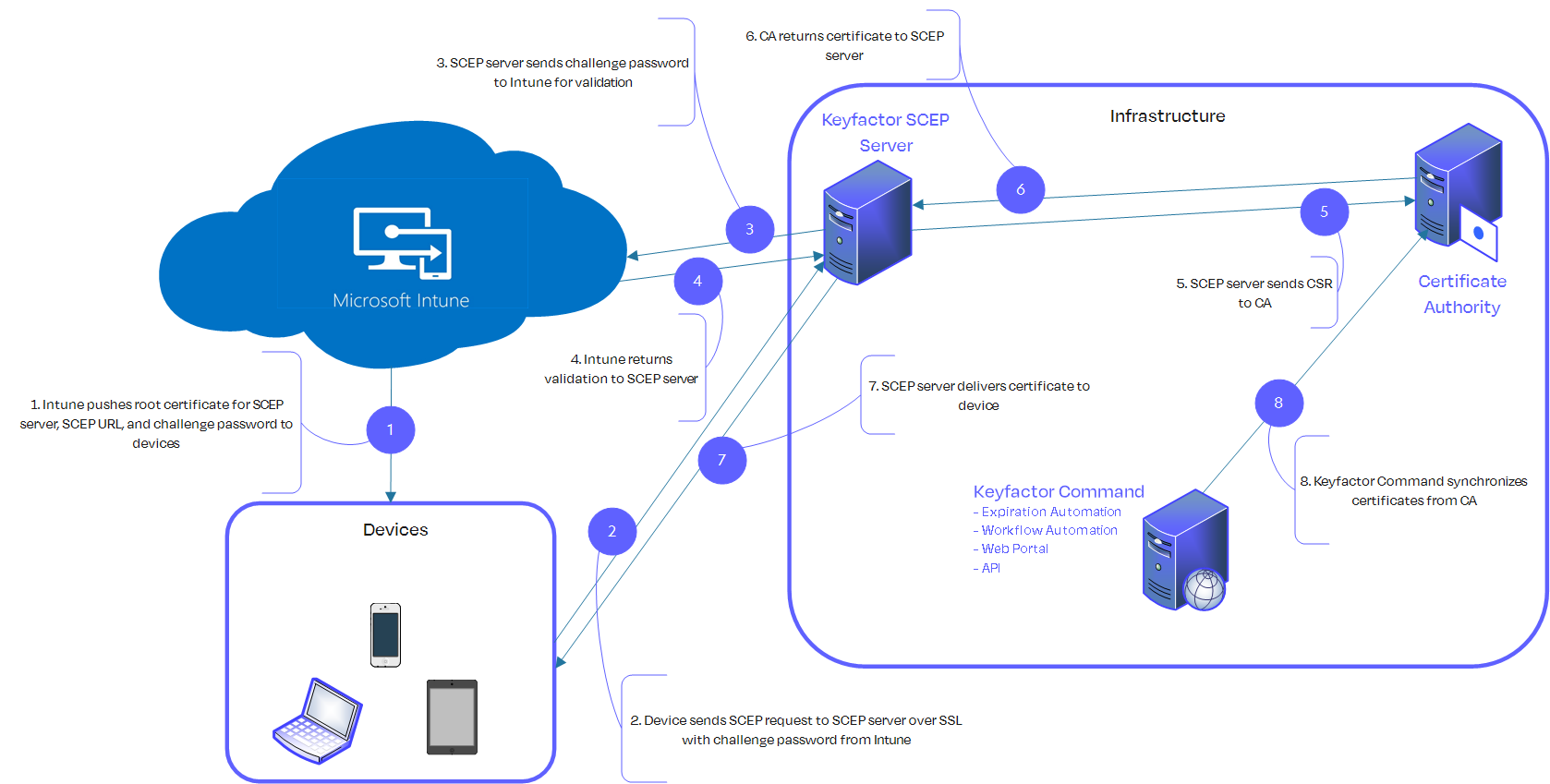
Figure 1: Certificate Request Flow with Intune
The Keyfactor SCEP server uses the ports shown in the following table.
Table 1: Keyfactor SCEP Port Usage
| Component | Protocol | Port | Direction | Purpose |
|---|---|---|---|---|
| Keyfactor SCEP Server | HTTP | 80 | Inbound | Default port for SCEP enrollment requests. |
| Keyfactor SCEP Server | HTTPS | 443 | Inbound | Secure alternative for SCEP enrollment. |
| Certificate Authority (CA) | RPC | 135 | Inbound | Required for communication with Microsoft Certificate Authorities. |
| Certificate Authority (CA) | DCOM | 49152–65535 | Inbound | Dynamic ports used for DCOM communication with CA. |
| Active Directory (AD) | LDAP | 389 | Outbound | For AD queries related to certificate templates. |
| Intune (optional) | HTTPS | 443 | Outbound | Autoenrollment |
| SQL (optional) | TCP | 1433 (or whatever port SQL is listening on) | Outbound | Store challenge passwords and configuration information. |
Was this page helpful? Provide Feedback