Configure Firewall Settings
Configure Firewall Settings
In order for the Keyfactor Remote CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. Gateway Connector
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. Gateway Connector![]() The Keyfactor Gateway Connector is installed in the customer forest to provide a connection between the on-premise CA and the Azure-hosted, Keyfactor managed Hosted Configuration Portal to provide support for synchronization, enrollment and management of certificates through the Azure-hosted instance of Keyfactor Command for the on-premise CA. It is supported on both Windows and Linux. to be able to communicate with the Keyfactor Remote CA Service server and the local Active Directory, appropriate firewall ports need to be open on the Keyfactor Remote CA Gateway Connector server and throughout the environment. These ports may already be open or may need to be opened.
The Keyfactor Gateway Connector is installed in the customer forest to provide a connection between the on-premise CA and the Azure-hosted, Keyfactor managed Hosted Configuration Portal to provide support for synchronization, enrollment and management of certificates through the Azure-hosted instance of Keyfactor Command for the on-premise CA. It is supported on both Windows and Linux. to be able to communicate with the Keyfactor Remote CA Service server and the local Active Directory, appropriate firewall ports need to be open on the Keyfactor Remote CA Gateway Connector server and throughout the environment. These ports may already be open or may need to be opened.
Table 1: Protocols the Keyfactor Remote CA Gateway Connector Uses for Communication
|
Type |
Protocols and Ports |
Source/Target |
|---|---|---|
|
Inbound |
RPC (TCP 135) |
Keyfactor Remote CA Service, for enrollment |
|
Inbound |
DCOM (Random high ports typically in the range TCP 49152 – 65535) |
Keyfactor Remote CA Service, for enrollment |
|
Outbound |
Active Directory Web Services (TCP 9389) |
Active Directory domain controllers, for template retrieval |
|
Outbound |
HTTPS (TCP 443) |
Keyfactor Remote CA Service |
On the Keyfactor Remote CA Gateway Connector server:
- Verify that the current ephemeral port range is open by opening an administrative command prompt and running the following command:
netsh interface ipv4 show dynamic protocol=tcp
The output from this command should look like this:
Protocol tcp Dynamic Port Range --------------------------------- Start Port: 49152 Number of Ports: 16384
- If the range is not open, it needs to be opened to allow RPC
 Remote procedure call (RPC) allows one program to call a function from a program located on another computer on a network without specifying network details. In the context of Keyfactor Command, RPC errors often indicate Kerberos authentication or delegation issues. communication via TCP. Keyfactor provides a PowerShell script for this purpose for use on Windows servers (see Appendix A—Firewall Rules for Windows).No rules are included in this script for HTTP/HTTPS or ADWS traffic, since outbound traffic is generally open on servers in most environments. If this is not the case in your environment, you will need to update the script or manually add a rule.
Remote procedure call (RPC) allows one program to call a function from a program located on another computer on a network without specifying network details. In the context of Keyfactor Command, RPC errors often indicate Kerberos authentication or delegation issues. communication via TCP. Keyfactor provides a PowerShell script for this purpose for use on Windows servers (see Appendix A—Firewall Rules for Windows).No rules are included in this script for HTTP/HTTPS or ADWS traffic, since outbound traffic is generally open on servers in most environments. If this is not the case in your environment, you will need to update the script or manually add a rule. - After running the firewall script to open the inbound ports, check the firewall rules to confirm that the new Keyfactor rule has been added by opening an administrative command prompt and running the following command:wf.msc
- Click Inbound Rules and verify that the new rule "Keyfactor Gateway Connector
 The Keyfactor Gateway Connector is installed in the customer forest to provide a connection between the on-premise CA and the Azure-hosted, Keyfactor managed Hosted Configuration Portal to provide support for synchronization, enrollment and management of certificates through the Azure-hosted instance of Keyfactor Command for the on-premise CA. It is supported on both Windows and Linux. RPC-IN" exists and is enabled. Verify that the existing rule: "COM+ Network Access (DCOM-In)" is enabled.
The Keyfactor Gateway Connector is installed in the customer forest to provide a connection between the on-premise CA and the Azure-hosted, Keyfactor managed Hosted Configuration Portal to provide support for synchronization, enrollment and management of certificates through the Azure-hosted instance of Keyfactor Command for the on-premise CA. It is supported on both Windows and Linux. RPC-IN" exists and is enabled. Verify that the existing rule: "COM+ Network Access (DCOM-In)" is enabled.
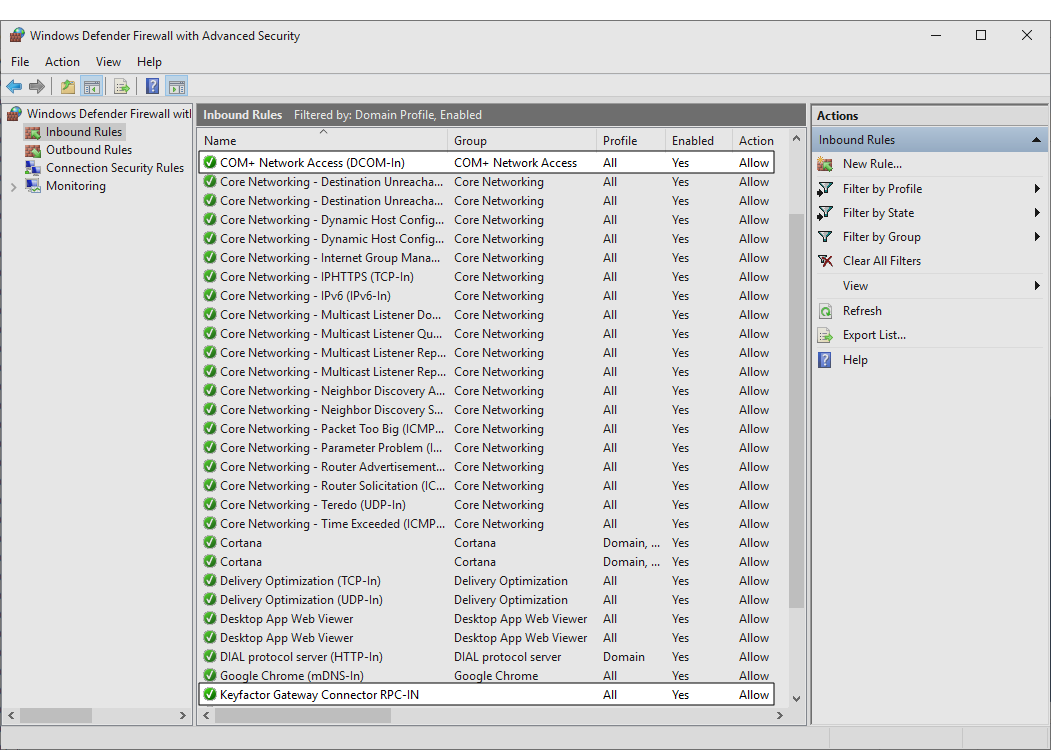
Figure 4: Firewall Rules