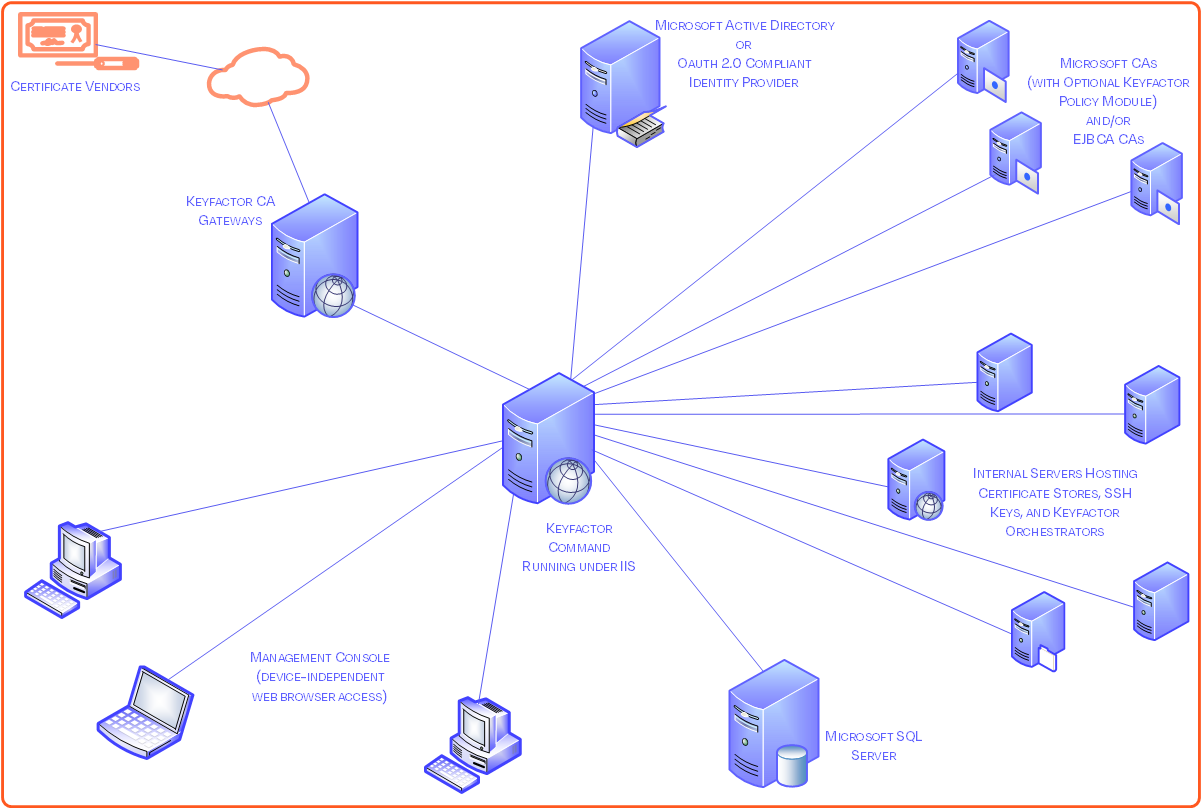
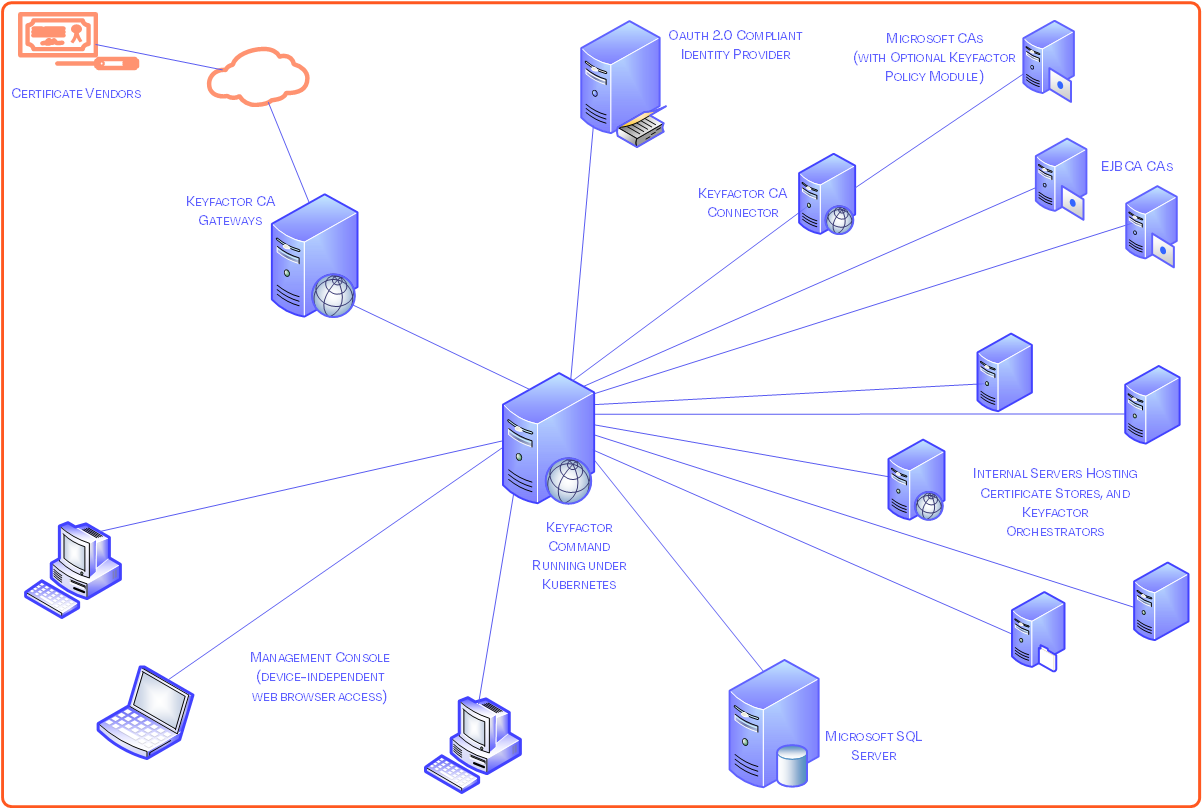
The following figures shows the physical architecture of the Keyfactor Command solution either as a Windows install running under IIS or a containerized install running under Kubernetes.
Figure 504: Keyfactor Command Physical Architecture Diagrams: Windows Server Install Under IIS vs Containerized Install Under Kubernetes
For simplicity, the servers in the above figure are shown as single physical instances. In practice, on Windows these servers may be virtual machines and may be load balanced or clustered to meet availability or performance requirements. Under Kubernetes, the installation is made up of multiple containers and may be spread across a Kubernetes cluster made up of multiple nodes.
The diagram includes some optional components—including the Keyfactor vendor gateways and Keyfactor orchestrators—which are not covered in this guide. For more information about these components, see the
-
Keyfactor Command Servers
-
Keyfactor Command Server—This server hosts the Keyfactor Command Management Portal, the Keyfactor Command Services roles, the Keyfactor API
 An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. role, the Orchestrator
An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. role, the Orchestrator Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. API role, the CA
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. API role, the CA A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. Connector API role, and the Logi Analytics Platform for report generation.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. Connector API role, and the Logi Analytics Platform for report generation. -
Keyfactor CA Connector
 The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. Client—The CA Connector Client may be used to connect to either EJBCA CAs or Microsoft CAs from Keyfactor Command implementations under either Windows or Kubernetes, but because no direct DCOM communication can be done from the containers in the Kubernetes cluster to Microsoft CAs, it is required when installing Keyfactor Command under Kubernetes to communicate with Microsoft CAs. The CA Connector Client may be installed on the Microsoft CA.
The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. Client—The CA Connector Client may be used to connect to either EJBCA CAs or Microsoft CAs from Keyfactor Command implementations under either Windows or Kubernetes, but because no direct DCOM communication can be done from the containers in the Kubernetes cluster to Microsoft CAs, it is required when installing Keyfactor Command under Kubernetes to communicate with Microsoft CAs. The CA Connector Client may be installed on the Microsoft CA.
-
-
Enterprise-Shared Servers:
-
Microsoft SQL Server—Keyfactor Command supports Microsoft SQL Server 2017, 2019 and 2022 all with TLS
 TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. encryption enabled for its primary database. While a dedicated SQL deployment is certainly an option, many organizations maintain a well-established SQL server farm to support multiple applications within the organization; if preferred, Keyfactor Command can easily make use of such a service. Keyfactor does not recommend locating the Keyfactor Command roles on the SQL server in a production deployment.
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. encryption enabled for its primary database. While a dedicated SQL deployment is certainly an option, many organizations maintain a well-established SQL server farm to support multiple applications within the organization; if preferred, Keyfactor Command can easily make use of such a service. Keyfactor does not recommend locating the Keyfactor Command roles on the SQL server in a production deployment.
-
Web Reverse Proxy—If Internet-based access is required, the Keyfactor Command services can be published through a variety of reverse proxy products such as F5, SiteMinder, or Citrix NetScaler.
-
Network-based Hardware Security Module (HSM not pictured)—In certain configurations, Keyfactor Command requires the use of Enrollment
 Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). Agent (EA) and/or Key Recovery Agent (KRA) certificates. To provide additional security over these certificates’ private keys, Keyfactor strongly recommends the use of a Hardware Security Module (HSM) such as the Thales NetHSM if these features will be used.
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). Agent (EA) and/or Key Recovery Agent (KRA) certificates. To provide additional security over these certificates’ private keys, Keyfactor strongly recommends the use of a Hardware Security Module (HSM) such as the Thales NetHSM if these features will be used. -
Microsoft and/or EJBCA CAs—Keyfactor Command supports both Microsoft and EJBCA CAs. When Keyfactor Command is installed under Kubernetes, an instance of the Keyfactor CA Connector Client is required to communicate with Microsoft CAs.
-
Was this page helpful? Provide Feedback