Permissions on certificate stores and their containers are controlled at two levels—system-wide and on a certificate store container-by-container basis. When designing a certificate store permission scheme, you may use entirely system-wide permissions or you may use a combination of system-wide permissions and container permissions. Both system-wide and container permissions are configured through Security Roles (see Security Role Operations).
System-wide certificate store permissions are controlled with the Certificate Stores role permissions on the Global Permissions tab of the Security Role Information dialog.
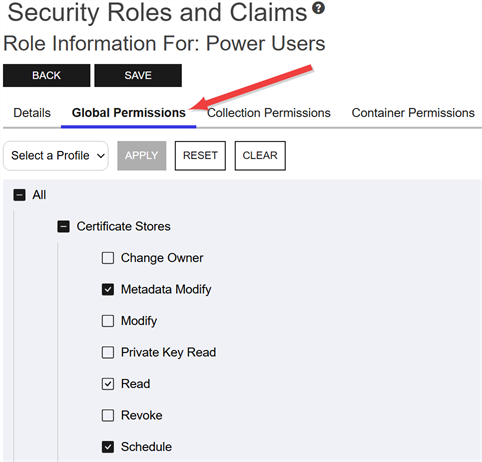
Figure 411: Certificate Stores: Global Permissions
Container-by-container permissions are set on the Container Permissions tab of the Role Information dialog for each container by name using the same set of permissions.
Any containers that do not have container-by-container permissions applied fall back to the system-wide permissions, if any system-wide permissions have been set for that role.
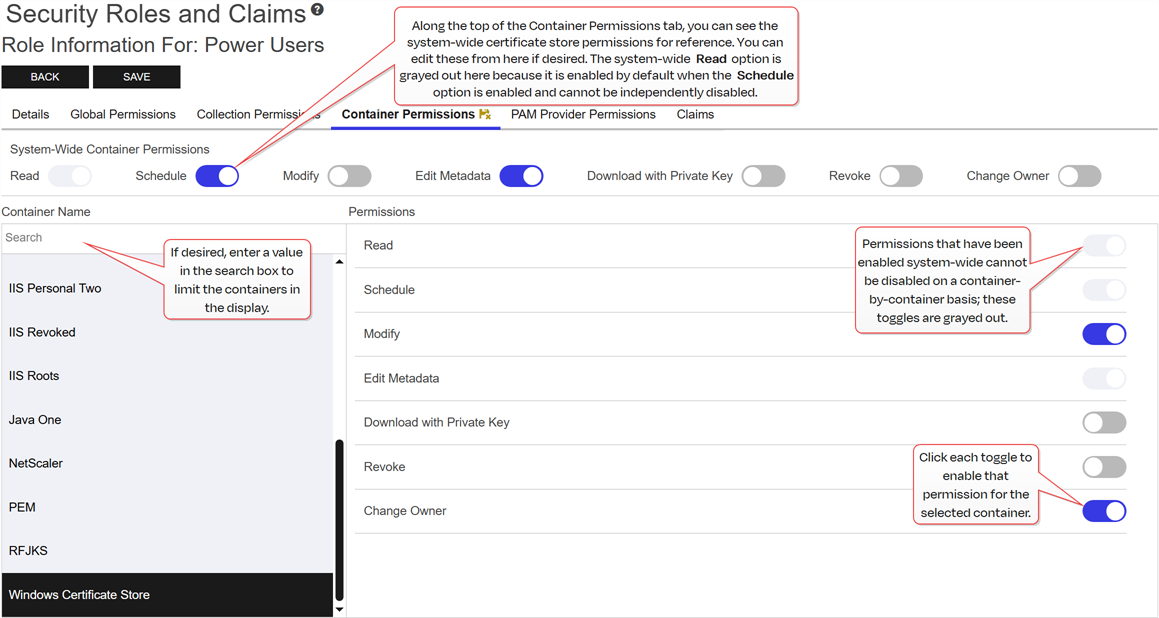
Figure 412: Certificate Store Management - Container Permissions
Container permissions work in conjunction with many other security permissions to control access to certificate store related functionality.
For more information about configuring container-level permissions, see Container Permissions Tab.
Was this page helpful? Provide Feedback