Generally, the installation of the gateway goes smoothly and the gateway will begin operating normally without any intervention. However, you can sometimes run into issues if, for example, the environment in which you are installing the gateway is especially securely locked down or if you are using more complicated features like enrollment![]() Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). agent certificates. Here we include some suggested troubleshooting steps. If you need further assistance, please contact Keyfactor support.
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). agent certificates. Here we include some suggested troubleshooting steps. If you need further assistance, please contact Keyfactor support.
 Configure Logging
Configure Logging
Start by configuring the logging at debug or trace level output and recreating the issue (see Configure Logging).
 No Logging Output
No Logging Output
If you are getting no output at all in the logs, check to be sure that the account running the gateway service(s) has permissions to write to the directory configured for logging in the NLog.config file (see Configure Logging). This account is typically Network Service. Check the Microsoft Services MMC to confirm the account under which the service is running. Try renaming the existing log to CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA._Gateway_Log_Save.txt (or similar). It's possible that the service can't write to the specific existing log file. A new log file will be created automatically.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA._Gateway_Log_Save.txt (or similar). It's possible that the service can't write to the specific existing log file. A new log file will be created automatically.
 Error: (400) Bad Request
Error: (400) Bad Request
If you are using a custom service account instead of Network Service to run the gateway service (as opposed to the sync service) and receive this error on attempting to save in the gateway configuration wizard, this may indicate that you haven’t fully configured the gateway service to run as the custom service account. Review the steps (see Start the Gateway Services) and confirm that each step has been completed. On upgrade, custom service account information is cleared and will need to be reconfigured.
 Error: Key does not exist
Error: Key does not exist
If you are using the enroll on behalf of function and enrolling on behalf of another user is failing with this error, confirm that your enrollment agent certificate is in the store from which you are trying to use it (local machine or current user). If you are using a certificate in the local machine store, confirm that you granted read permissions on the private key![]() Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. of the enrollment agent certificate to the user making the enrollment request (see Configure a Certificate for Enroll on Behalf of (Optional)).
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. of the enrollment agent certificate to the user making the enrollment request (see Configure a Certificate for Enroll on Behalf of (Optional)).
 Error: No certificate available
Error: No certificate available
If you are using the enroll on behalf of function in the Microsoft certificates snap-in and enrolling on behalf of another user is failing with this error, confirm that your enrollment agent certificate is in the local user store. Confirm that the appropriate chain certificates are installed in the local user store for the certificate. Confirm that you have installed the intermediate CA certificate into the NTAuthCertificates object in Active Directory (see Acquire and Install a Chain Certificate).
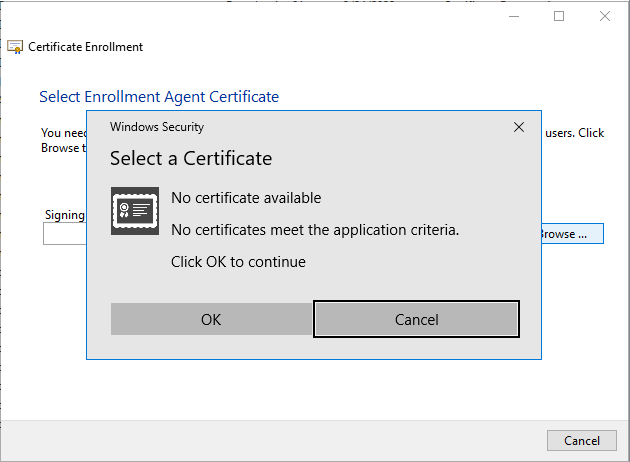
Figure 735: No Certificate Available During Enroll on Behalf of
 Log Error Contains: Error performing account synchronization: Error enumerating group
Log Error Contains: Error performing account synchronization: Error enumerating group
If you are using the account synchronization option and synchronization fails with this error, look for a subsequent error along the lines of:
If you see this, confirm that you have installed the remote server administration tools (![]() An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. running versions of Windows older than 2012 R2. This error can occur in a multi-domain environment if the account synchronization process attempts to look up membership on a group where the lookup must check outside the current domain. In this scenario, the error may be intermittent, as it only occurs when the request is sent to a domain controller older than 2012 R2 and not when the request happens to be directed to a newer domain controller. To resolve this issue, modify the Get-KeyfactorSyncGroupMembers.ps1 script file. This file is found in the scripts directory under the installed directory for the gateway. By default, this is:
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. running versions of Windows older than 2012 R2. This error can occur in a multi-domain environment if the account synchronization process attempts to look up membership on a group where the lookup must check outside the current domain. In this scenario, the error may be intermittent, as it only occurs when the request is sent to a domain controller older than 2012 R2 and not when the request happens to be directed to a newer domain controller. To resolve this issue, modify the Get-KeyfactorSyncGroupMembers.ps1 script file. This file is found in the scripts directory under the installed directory for the gateway. By default, this is:
Add the following just above the section that is commented “Look up the group”:
# Force requests to use DCs of OS version 2012 R2 or higher
$dc = ((Get-ADDomainController -DomainName $groupDomain -Discover -SiteName "Default-First-Site-Name" -MinimumDirectoryServiceVersion Windows2012R2).HostName)
Modify the “Look up the group” section as follows, commenting out the two existing $adGroup lines and adding new lines referencing $dc.Value (changes marked in red):
# Look up the group, using the search base, if provided
if($SearchBase)
{
Write-Verbose "Searching for group '$groupSAMAccountName' in domain '$groupDomain' using search base '$SearchBase' and DC $dc"
#$adGroup = Get-ADGroup -Filter "sAMAccountName -eq '$groupSAMAccountName'" -SearchBase $SearchBase -Server $groupDomain
$adGroup = Get-ADGroup -Filter "sAMAccountName -eq '$groupSAMAccountName'" -SearchBase $SearchBase -Server $dc.Value
}
else
{
Write-Verbose "Searching for group '$groupSAMAccountName' in domain '$groupDomain' using default search base and DC $dc"
#$adGroup = Get-ADGroup -Filter "sAMAccountName -eq '$groupSAMAccountName'" -Server $groupDomain
$adGroup = Get-ADGroup -Filter "sAMAccountName -eq '$groupSAMAccountName'" -Server $dc.Value
}
 Error: Remote template [template name] has private key retention enabled, but key archival is not supported.
Error: Remote template [template name] has private key retention enabled, but key archival is not supported.
If you receive this error while trying to configure templates for the gateway, this indicates that the referenced remote template![]() A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. has been configured in Keyfactor Command with the Private Key Retention option enabled, which is not supported for the gateway. Disable private key retention for the template in Keyfactor Command, refresh the templates in the configuration wizard, and try again.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. has been configured in Keyfactor Command with the Private Key Retention option enabled, which is not supported for the gateway. Disable private key retention for the template in Keyfactor Command, refresh the templates in the configuration wizard, and try again.
 Error: Local template [template name] has key archival enabled, but key archival is not supported.
Error: Local template [template name] has key archival enabled, but key archival is not supported.
If you receive this error while trying to configure templates for the gateway, this indicates that the referenced local template has been configured locally with the Archive subject's encryption private key option, which is not supported for the gateway. Remove this option for the template, refresh templates in the configuration wizard, and try again.
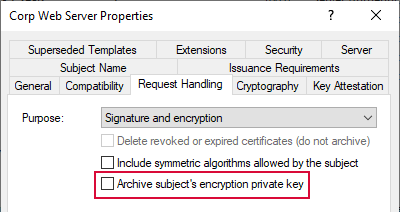
Figure 736: Archive Subject's Private Key Template Configuration
In order to configure the Keyfactor Cloud Gateway version 25.1 and higher to use a proxy please review the following steps:
-
Install/Upgrade to the desired version of the Keyfactor Cloud Gateway.
-
Close the configuration wizard of the Keyfactor Cloud Gateway.
-
Navigate to the configuration files for the Keyfactor Cloud Gateway (C:\Program Files\Keyfactor\Managed CA...).
-
Locate the three gateway configuration files and alter as described below:
-
GatewayConfig.exe.config
Paste the following line inside <configuration> section:
<system.net> <defaultProxy> <proxy proxyaddress="proxy address" bypassonlocal="true" /> </defaultProxy> </system.net>
-
CAProxy.SyncService.exe.config and CAProxyServer.exe.config
Paste the following line inside the <configuration> section directly after the <configSections> section:
<system.net> <defaultProxy> <proxy proxyaddress="proxy address" bypassonlocal="true" /> </defaultProxy> </system.net>
-
-
Restart the Keyfactor gateway service.
-
Open the Keyfactor Cloud Gateway configuration wizard and validate the connection.
Was this page helpful? Provide Feedback