CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. connectors allow organizations to make connections to Keyfactor Command from certificate authorities that are remote from their instance of Keyfactor Command. Remote can mean just in an untrusted forest
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. connectors allow organizations to make connections to Keyfactor Command from certificate authorities that are remote from their instance of Keyfactor Command. Remote can mean just in an untrusted forest![]() An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. or can mean on an entirely different network. It is often used by organizations with managed instances of Keyfactor Command to connect to their on-premises CAs. The CA Connectors tab is used to manage connector record instances of the CA Connector
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. or can mean on an entirely different network. It is often used by organizations with managed instances of Keyfactor Command to connect to their on-premises CAs. The CA Connectors tab is used to manage connector record instances of the CA Connector![]() The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. Client software installed in the remote environment.
The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. Client software installed in the remote environment.
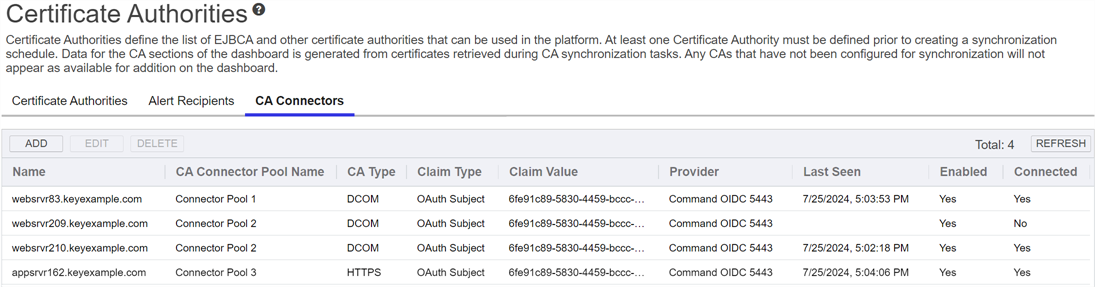
Figure 261: CA Connectors
Adding or Editing a CA Connector
Before adding a connector record on this tab, be sure that the information on the Task Queue Connection tab has been populated. This is typically populated during installation, but must be complete before proceeding.
To create a new CA connector record or modify an existing one:
- In the Management Portal, browse to Locations > Certificate Authorities.
- On the Certificate Authorities page, select the CA Connectors tab, and click Add to add a new CA connector, or select a row and click Edit from either the top or right-click menu to modify an existing one.
- In the Add/Edit New CA Connector dialog in the General section, enter a Name for the connector. This name must match the name that the CA Connector Client server will use to connect to Keyfactor Command. If you use the -Name (Windows) or --name (Linux) parameter
 A parameter or argument is a value that is passed into a function in an application. when installing the CA Connector Client, you can specify this value. If you do not specify this value, the CA Connector Client uses the results from a hostname
A parameter or argument is a value that is passed into a function in an application. when installing the CA Connector Client, you can specify this value. If you do not specify this value, the CA Connector Client uses the results from a hostname The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). lookup for the server's name. The Name field cannot be modified on an edit.
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). lookup for the server's name. The Name field cannot be modified on an edit. - Enter a CA Connector Pool Name. Pools are used to group multiple remote CA connectors together to perform tasks on the same CA or set of CAs. A pool may only contain remote CA connectors of one type—DCOM or HTTPS. The CA Connector Pool Name field cannot be modified on an edit if the pool is in use by a CA and the connector being edited is the last enabled connector in the pool.
- In the CA Type dropdown, select the correct type for your connector. DCOM is used for Microsoft CAs. HTTPS is used for EJBCA CAs. The CA Type cannot be modified on an edit if the pool is in use by a CA and the connector being edited is the last enabled connector in the pool.
-
Click to toggle the Enable CA Connector option to off, if desired. The default is on. The Enable CA Connector status cannot be modified on an edit if the pool is in use by a CA and the connector being edited is the last enabled connector in the pool.
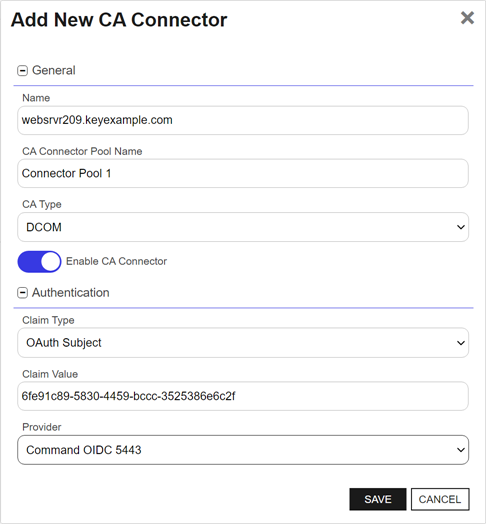
Figure 262: Add New CA Connector
-
In the Add/Edit New CA Connector dialog in the Authentication section, select a Claim Type in the dropdown. Supported options are:
- OAuth Subject—An open authorization 2.0 user claim.
- OAuth Object Id—An open authorization 2.0 claim of a type not covered by client, role or subject.
- OAuth Role—An open authorization 2.0 group claim.
- OAuth Client Id—An open authorization 2.0 client application claim.
- In the Claim Value field, enter the OAuth claim value that the CA Connector Client will use to authenticate to Keyfactor Command based on the Claim Type you selected.
-
Select the OAuth Provider from the dropdown that will provide your claim. This list is populated with your configured identity providers.
Tip: If you're using Keyfactor Identity Provider and you are using a Subject (sub) claim, you can find the value to enter in this field as follows:- In the Keyfactor Identity Provider Administration Console, browse to Clients under the correct Realm (e.g. Keyfactor) to locate the client you created for use with the CA Connector Client.
Open the client for editing, and on the Service accounts roles tab look for an informational message that says:
To manage detail and group mappings, click on the usernameFollowed by a link related to your client name. For example, if your client name is MyCAConnector, the link would be service-account-MyCAConnector. Click the link. This will open a user page.
The GUID in the ID field of the user details for the service-account-YourClientName is the sub claim. This is the value you would enter as the Claim Value field.
Deleting a CA Connector
To delete a CA connector record:
- In the Management Portal, browse to Locations > Certificate Authorities.
- On the Certificate Authorities page, select the CA Connectors tab, select a row, and click Delete from either the top or right-click menu.
- On the Confirm Operation alert, click OK to confirm or Cancel to cancel the operation.
A CA connector cannot be deleted if it is the last one in its pool with an enabled status and the pool is configured for use by at least one CA.
Was this page helpful? Provide Feedback