A string indicating the type of workflow definition. The currently supported types are:
-
CertificateEnteredCollection
Initiates a workflow instance when a certificate is identified that newly meets the query criteria of a certificate collection. For example, when a certificate discovered on an SSL scan becomes part of the Weak Keys collection, an email message can be generated notifying the PKI administrators that a new certificate with a weak key has been discovered.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your collections to identify certificates that newly meet the query criteria of each certificate collection. Certificates are added to a temporary table from which workflows of this type draw. Certificates are added for all collections regardless of whether they have active workflows. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
If the task has run to create the temporary table of certificates that newly meet the query criteria of the specified certificate collection but a workflow has not yet run for the given collection—perhaps it is disabled or has not yet been created—there is a window of time (until the temporary table is cleared) during which if a workflow is created or enabled for the certificate collection, the user creating or enabling the workflow will receive a warning message indicating that the workflow will run multiple times and asking the user for confirmation to continue. The user must enter RUN followed by the number of workflow instances that will be initiated to continue.
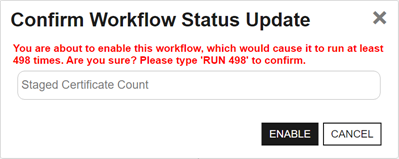
Figure 475: Warning on Save for Certificate Entered or Left Collection Workflow
-
CertificateLeftCollection
Initiates a workflow instance when a certificate is identified that no longer meet the query criteria of the specified certificate collection. For example, when a certificate in the Web Server Certificates collection disappears, a REST request can be made to open a support ticket request to investigate the removal of a web server certificate.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your collections to identify certificates that no longer meet the query criteria of each certificate collection. Certificates are added to a temporary table from which workflows of this type draw. Certificates are added for all collections regardless of whether they have active workflows. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
If the task has run to create the temporary table of certificates that no longer meet the query criteria of the specified certificate collection but a workflow has not yet run for the given collection—perhaps it is disabled or has not yet been created—there is a window of time (until the temporary table is cleared) during which if a workflow is created or enabled for the certificate collection, the user creating or enabling the workflow will receive a warning message indicating that the workflow will run multiple times and asking the user for confirmation to continue. The user must enter RUN followed by the number of workflow instances that will be initiated to continue.
-
CertificateEnteredStore
Initiates a workflow instance when a certificate has been added to or has entered a certificate store for the specified certificate store type and optional certificate store container. For example, when a certificate appears in a trusted certificate store, a REST request can be made to check the support ticketing system for a change request, and the workflow can then generate an email message notifying the PKI administrators that a new certificate has appeared in a trusted store if a change request is not found.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your certificate store types to identify certificates that have been added to or have entered a certificate store for the specified certificate store type and optional certificate store container. Certificates are added to a temporary table from which workflows of this type draw. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs. Included in the workflow information are the certificate ID, certificate store ID, and certificate store container ID. If the certificate store is not in a container, the container ID will be -1.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
-
CertificateLeftStore
Initiates a workflow instance when a certificate has been removed from or has left a certificate store for the specified certificate store type and optional certificate store container. For example, when a certificate on your F5 device disappears, a REST request can be made to open a support ticket request to investigate the removal of a certificate from the device.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your certificate store types to identify certificates that have been removed from or have left a certificate store for the specified certificate store type and optional certificate store container. Certificates are added to a temporary table from which workflows of this type draw. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs. Included in the workflow information are the certificate ID, certificate store ID, and certificate store container ID. If the certificate store is not in a container, the container ID will be -1.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
-
Enrollment (Including Renewals)
The workflow is initiated by enrollment for a new or renewed certificate. Steps during the workflow can be used to do things such as require manager approval for the enrollment or manipulate the subject and/or SANs for the certificate request.
Note: An enrollment workflow is considered complete when the certificate reaches a state of Active (issued), Failed (denied approval in workflow or error at the CA level), Pending, or Waiting for External Validation. The workflow does not wait for external approvals before completing.
-
Expiration
The workflow is initiated by an expiration alert. Steps during the workflow can be used to do things such as send an email notification regarding expiring certificates, run a PowerShell script to write notifications to the event log, or automate renewal of certificates.
-
Key Rotation
The workflow is initiated by an SSH key rotation alert. Steps during the workflow can be used to do things such as send an email notification regarding SSH keys that are approaching their stale date or run a PowerShell script to write notifications to the event log.
-
Revocation
The workflow is initiated by revoking a certificate. Steps during the workflow can be configured to do things such as modify the revocation comment entered when the certificate is revoked, append an additional comment, and store the resulting extended comment in a metadata field.
-
Revocation Monitoring
The workflow is initiated by a revocation monitoring alert. Steps during the workflow can be used to do things such as send an email notification regarding CRLs that are expiring or OCSP endpoints that are unreachable or run a PowerShell script to write notifications to the event log.
![]() A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked./Definitions method is used to retrieve the list of workflow definitions. This method returns HTTP 200 OK on a success with high level information about the workflow definitions. Use the GET /Workflow/Definitions/{definitionid} method (see GET Workflow Definitions Definition ID) to return details including the workflow steps.
A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked./Definitions method is used to retrieve the list of workflow definitions. This method returns HTTP 200 OK on a success with high level information about the workflow definitions. Use the GET /Workflow/Definitions/{definitionid} method (see GET Workflow Definitions Definition ID) to return details including the workflow steps.