When your SSH![]() The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. servers are configured in inventory only mode doing discovery, keys discovered on the servers are considered unmanaged and are displayed on the Unmanaged Keys page.
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. servers are configured in inventory only mode doing discovery, keys discovered on the servers are considered unmanaged and are displayed on the Unmanaged Keys page.
On this page you can review the discovered keys to get a sense of what's out there. You can view the keys, key comments, fingerprint, type and length. Once you switch your servers to inventory and publish policy mode, deleting a key from the unmanaged keys page will also delete the key from the server(s) in this mode on which it is found.
As you bring your servers under management, clean up old keys, and control installation of new keys, the number of keys appearing on the unmanaged keys page should begin to diminish. Eventually, the page should be empty when all your servers have been brought under management and all old keys have been replaced with new, managed, keys.
 View an Unmanaged SSH Key
View an Unmanaged SSH Key
To view details for an unmanaged public key![]() In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key., double-click the key, right-click the key and choose View from the right-click menu, or highlight the row in the unmanaged keys grid and click View at the top of the grid.
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key., double-click the key, right-click the key and choose View from the right-click menu, or highlight the row in the unmanaged keys grid and click View at the top of the grid.
The view dialog includes two tabs:
- On the Basic tab, you can see information about the key itself, including the key length
 The key size or key length is the number of bits in a key used by a cryptographic algorithm., fingerprint, comments associated with the key, and the public key itself.
The key size or key length is the number of bits in a key used by a cryptographic algorithm., fingerprint, comments associated with the key, and the public key itself.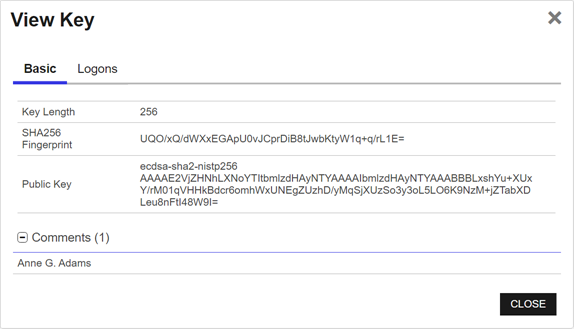
Figure 339: View Basic Tab of an Unmanaged SSH Key
- On the Logon tab, you can view Linux logon names and servers mapped to the public key.
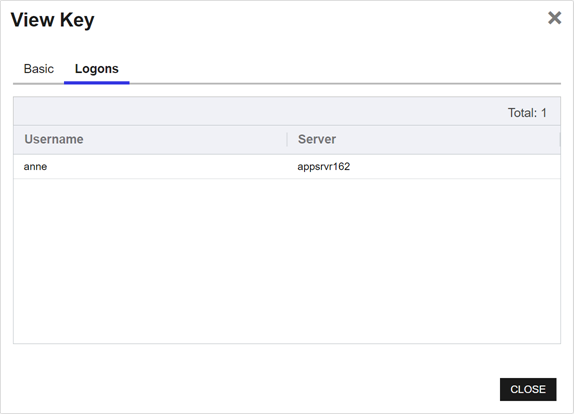
Figure 340: View Logon Tab of an Unmanaged SSH Key
 Delete an Unmanaged SSH Key
Delete an Unmanaged SSH Key
To delete an unmanaged key, highlight the row in the unmanaged keys grid and click Delete at the top of the grid or right-click the key in the grid and choose Delete from the right-click menu.
You can also find the help icon (![]() ) at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Software & Documentation Portal at the home page or the Keyfactor API Endpoint Utility.
) at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Software & Documentation Portal at the home page or the Keyfactor API Endpoint Utility.
Keyfactor provides two sets of documentation: the On-Premises Documentation Suite and the Managed Services Documentation Suite. Which documentation set is accessed is determined by the Application Settings: On-Prem Documentation setting (see Application Settings: Console Tab).