For some features of the Management Portal to function correctly when using Kerberos authentication (e.g. delegation of CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. functions, alerting using the event logging event handler and a DNS
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. functions, alerting using the event logging event handler and a DNS![]() The Domain Name System is a service that translates names into IP addresses. alias or alternate target machine), it may be necessary to disable loopback checking on the Keyfactor Command server.
The Domain Name System is a service that translates names into IP addresses. alias or alternate target machine), it may be necessary to disable loopback checking on the Keyfactor Command server.
To disable loopback checking for selected FQDNs:
-
On the Keyfactor Command server, open the registry editor and browse to:
HKEY_LOCAL_MACHINE\ SYSTEM\ CurrentControlSet\ Services\ LanmanServer\ Parameters -
Right-click the Parameters registry key and choose New > DWORD (32-bit) Value. Name the new DWORD value DisableStrictNameChecking. Set the DisableStrictNameChecking value to 1.
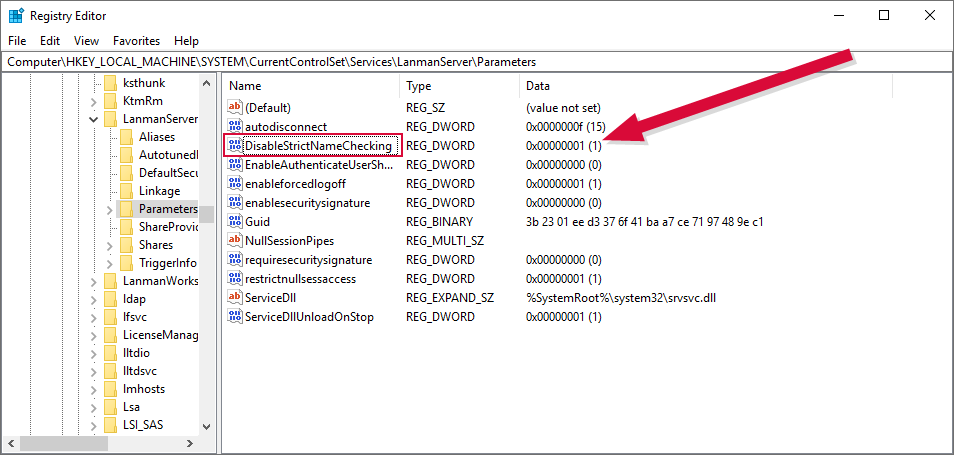
Figure 456: Disable Loopback Checking: DisableStrictNameChecking
-
In the registry editor browse to:
HKEY_LOCAL_MACHINE\ SYSTEM\ CurrentControlSet\ Control\ Lsa\ MSV1_0 -
Right-click the MSV1_0 registry key and choose New > Multi-String Value. Name the new value BackConnectionHostNames. Edit the BackConnectionHostNames value and enter each fully qualified domain name—actual name or DNS alias—for a server that needs this feature on a separate line. For example, for full DNS alias support with CA delegation functions, you need to enter the DNS alias of the Keyfactor Command server. For event logging to a machine other than the Keyfactor Command server, you need to enter the name of that server.
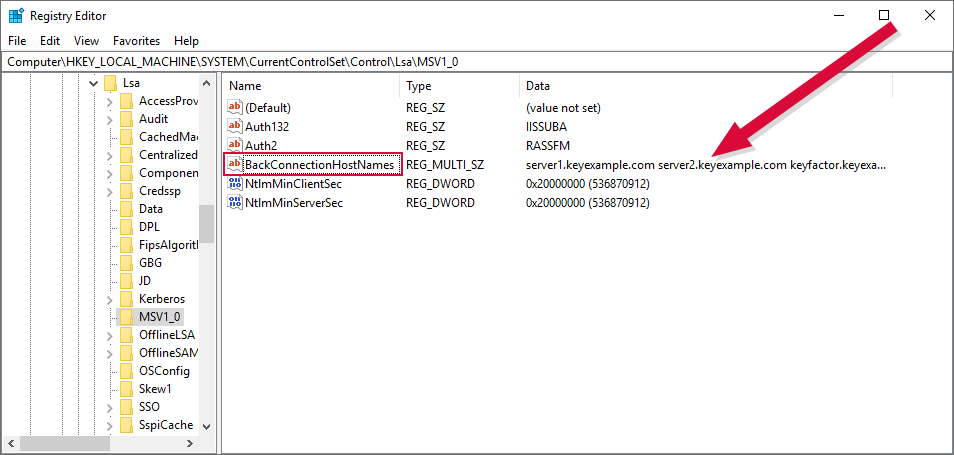
Figure 457: Disable Loopback Checking: BackConnectionHostNames
- After completing the registry configuration you must reboot the Keyfactor Command server before the changes will take effect.