| Key |
A string indicating the reference key for the workflow definition. The type of information contained in this field will vary depending on the WorkflowType. If the WorkflowType is Enrollment or Revocation, this field will contain the Keyfactor Command reference ID for the certificate template. If the WorkflowType is CertificateLeftCollection or CertificateEnteredCollection, this field will contain the Keyfactor Command reference ID for the certificate collection.
|
| Workflow Type |
A string indicating the type of workflow definition. The currently supported types are:
-
CertificateEnteredCollection
Initiates a workflow instance when a certificate is identified that newly meets the query criteria of a certificate collection. For example, when a certificate discovered on an SSL scan becomes part of the Weak Keys collection, an email message can be generated notifying the PKI administrators that a new certificate with a weak key has been discovered.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your collections to identify certificates that newly meet the query criteria of each certificate collection. Certificates are added to a temporary table from which workflows of this type draw. Certificates are added for all collections regardless of whether they have active workflows. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
If the task has run to create the temporary table of certificates that newly meet the query criteria of the specified certificate collection but a workflow has not yet run for the given collection—perhaps it is disabled or has not yet been created—there is a window of time (until the temporary table is cleared) during which if a workflow is created or enabled for the certificate collection, the user creating or enabling the workflow will receive a warning message indicating that the workflow will run multiple times and asking the user for confirmation to continue. The user must enter RUN followed by the number of workflow instances that will be initiated to continue.
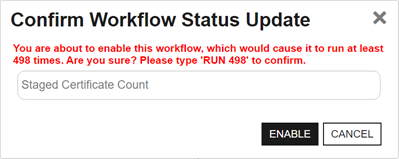
Figure 464: Warning on Save for Certificate Entered or Left Collection Workflow
-
CertificateLeftCollection
Initiates a workflow instance when a certificate is identified that no longer meet the query criteria of the specified certificate collection. For example, when a certificate in the Web Server Certificates collection disappears, a REST request can be made to open a support ticket request to investigate the removal of a web server certificate.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your collections to identify certificates that no longer meet the query criteria of each certificate collection. Certificates are added to a temporary table from which workflows of this type draw. Certificates are added for all collections regardless of whether they have active workflows. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
If the task has run to create the temporary table of certificates that no longer meet the query criteria of the specified certificate collection but a workflow has not yet run for the given collection—perhaps it is disabled or has not yet been created—there is a window of time (until the temporary table is cleared) during which if a workflow is created or enabled for the certificate collection, the user creating or enabling the workflow will receive a warning message indicating that the workflow will run multiple times and asking the user for confirmation to continue. The user must enter RUN followed by the number of workflow instances that will be initiated to continue.
-
CertificateEnteredStore
Initiates a workflow instance when a certificate has been added to or has entered a certificate store for the specified certificate store type and optional certificate store container. For example, when a certificate appears in a Java Keystore, a REST request can be made to check the support ticketing system for a change request, and the workflow can then generate an email message notifying the PKI administrators that a new certificate has appeared in an unexpected location if a change request is not found.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your certificate store types to identify certificates that have been added to or have entered a certificate store for the specified certificate store type and optional certificate store container. Certificates are added to a temporary table from which workflows of this type draw. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs. Included in the workflow information are the certificate ID, certificate store ID, and certificate store container ID. If the certificate store is not in a container, the container ID will be -1.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
-
CertificateLeftStore
Initiates a workflow instance when a certificate has been removed from or has left a certificate store for the specified certificate store type and optional certificate store container. For example, when a certificate on your F5 device disappears, a REST request can be made to open a support ticket request to investigate the removal of a certificate from the device.
The workflow is initiated by two automated tasks that Keyfactor Command runs periodically. The first runs against your certificate store types to identify certificates that have been removed from or have left a certificate store for the specified certificate store type and optional certificate store container. Certificates are added to a temporary table from which workflows of this type draw. The second reads the temporary table and generates workflow instances for any active workflows of this type. The temporary table is cleared each time the first task runs. Included in the workflow information are the certificate ID, certificate store ID, and certificate store container ID. If the certificate store is not in a container, the container ID will be -1.
Each of these tasks runs every 10 minutes by default and the schedules for them are not end-user configurable.
-
Enrollment (Including Renewals)
The workflow is initiated by enrollment for a new or renewed certificate. Steps during the workflow can be used to do things such as require manager approval for the enrollment or manipulate the subject and/or SANs for the certificate request.
Note: An enrollment workflow is considered complete when the certificate reaches a state of Active (issued), Failed (denied approval in workflow or error at the CA level), Pending, or Waiting for External Validation. The workflow does not wait for external approvals before completing.
-
Expiration
The workflow is initiated by an expiration alert. Steps during the workflow can be used to do things such as send an email notification regarding expiring certificates, run a PowerShell script to write notifications to the event log, or automate renewal of certificates.
-
Key Rotation
The workflow is initiated by an SSH key rotation alert. Steps during the workflow can be used to do things such as send an email notification regarding SSH keys that are approaching their stale date or run a PowerShell script to write notifications to the event log.
-
Revocation
The workflow is initiated by revoking a certificate. Steps during the workflow can be configured to do things such as modify the revocation comment entered when the certificate is revoked, append an additional comment, and store the resulting extended comment in a metadata field.
-
Revocation Monitoring
The workflow is initiated by a revocation monitoring alert. Steps during the workflow can be used to do things such as send an email notification regarding CRLs that are expiring or OCSP endpoints that are unreachable or run a PowerShell script to write notifications to the event log.
|
| Steps |
An array of objects indicating the steps in the workflow definition. The contents of each step will vary depending on the type of workflow and the type of step. For a newly created workflow, there will be no data in this value.  Show step details. Show step details.
| Id |
A string indicating the Keyfactor Command reference GUID of the workflow definition step. |
| Display Name |
A string indicating the display name for the step. |
| Unique Name |
A string indicating the unique name for the step. This value must be unique among the steps in the particular workflow definition. It is intended to be used as a user-friendly reference ID. |
| Extension Name |
A string indicating the type of step. The currently supported types are:
-
RESTRequest
Run a REST (API) request using Active Directory as an identity provider and Basic or Windows authentication. The REST request contents are embedded within the step. It does not call out to an external file.
-
OAuthRESTRequest
Run a REST (API) request using an identity provider other than Active Directory and Token authentication. The REST request contents are embedded within the step. It does not call out to an external file.
-
EnrollStep (Enrollment Only)
Enroll for a certificate through Keyfactor Command. The enroll step may occur at any point during the workflow, but only one enroll step may be included in a given workflow. Conditions are not supported on an enroll step. If an enroll step is not added to an Enrollment workflow, one will be included automatically at the end of the workflow. No configuration parameters are required for this step type.
-
ExpirationRenewal (Expiration Only)
Renew an expired certificate through Keyfactor Command as part of an expiration alert workflow. A separate enrollment workflow is automatically initiated to enroll for the renewed certificate, and the renewal workflow will only be considered complete and successful if that enrollment step completes successfully.
Tip: The Keyfactor Command Service (timer service) needs permissions to enroll on the CA and template used for renewal when this step is used.
-
RevokeStep (Revocation Only)
Revoke a certificate through Keyfactor Command. The revoke step may occur at any point during the workflow, but only one revoke step may be included in a given workflow. Conditions are not supported on a revoke step. If a revoke step is not added to a Revocation workflow, one will be included automatically at the end of the workflow. No configuration parameters are required for this step type.
-
RequireApproval
Require approval for a workflow step before the step can be completed. The require approval step can require approval from just one approver or multiple approvers. The workflow will be suspended at this point until the correct number of approvals from users with the correct security roles is received or until one deny is received before continuing to the next step. As part of this step, an email message is sent indicating whether the step was approved or denied—typically to the requester. This step does not include logic to send an email initiating the approval process (letting users know something needs approval). Use an Email type step for this.
Important: Workflows are not supported with CA delegation when they contain steps that require approval. For more information, see the CA configuration Authentication Method Tab.
Note: The users that you send email to initiating the approval process must be members of a security role that is allowed to submit signals (approve/deny) for the workflow in order to approve or deny the request.
-
Email
Send an email message. This is a separate email message from those typically sent as part of a Require Approval step. You might send an email message as part of an enrollment request to notify approvers that a new request needs approval. The email messages can be customized to provide detailed information about, for example, the certificate request.
-
PowerShell
Run PowerShell commands within the confines of the workflow to populate variables with information to pass back to the workflow. The PowerShell script contents are embedded within the step. This step does not call out to an external script stored in the database. This provides a high level of security by greatly limiting the number of standard PowerShell cmdlets that can be executed by the workflow step. A small number of PowerShell cmdlets have been white listed to allow them to be included in workflow steps of this type, including:
-
ConvertFrom-Csv
-
ConvertFrom-Json
-
ConvertFrom-Markdown
-
ConvertFrom-SddlString
-
ConvertFrom-StringData
-
ConvertTo-Csv
-
ConvertTo-Html
-
ConvertTo-Json
-
ConvertTo-Xml
- ForEach-Object
-
Get-Command
- Where-Object
Important: This step uses PowerShell 7 to run. Some cmdlets that run in earlier versions of PowerShell are not compatible with PowerShell 7.
-
EnrollmentAgent (Enrollment Only)
On an enrollment (either CSR or PFX), create a resigned CSR to prepare an updated enrollment request for delivery to a Microsoft CA after a previous step in the workflow has been used to update either the SANs in the initial request, subject (DN) in the initial request or both. This step must be placed later in the workflow than the step(s) to modify the SANs and/or subject. The SANs and subject may be modified with either of the PowerShell step types or a custom step type. The step creates a new CSR using the same public key as the original CSR using the updated SAN and/or subject values. It signs the new CSR with the certificate provided in the step's configuration.
For this type of step you will need an enrollment agent certificate available as a PKCS#12 (.PFX) file with included private key to import into Keyfactor Command. This can be a user certificate or a computer certificate (e.g. generated from a copy of the Enrollment Agent template or the Enrollment Agent (Computer) template) and must have a Certificate Request Agent EKU. Note that the built-in Enrollment Agent and Enrollment Agent (Computer) templates do not allow private keys to be exported by default. You will need a template that allows private key export or will need to manually override private key export to create a certificate with an exportable private key in order to create a PKCS#12 (.PFX) file.
Important: This step applies to Microsoft CAs only. If this step is added to workflow for requests directed to an EJBCA CA, it will fail on enrollment. Note that EJBCA supports submission of updated SAN or subject details as part of standard functionality.
-
CustomPowerShell
Run a PowerShell script that has been imported into the Keyfactor Command database. All scripts in the database that have been configured with the workflow category will be available for use. See Extensions Scripts for adding scripts to the database.
Important: This step uses PowerShell 7 to run. Some cmdlets that run in earlier versions of PowerShell are not compatible with PowerShell 7.
-
SubjectFormatter
(Enrollment Only)
On an enrollment done through the Keyfactor Windows Enrollment Gateway using a client-side template configured with the Build from this Active Directory information option on the template, this workflow step handles formatting the incoming subject, SANs, and/or SID in the certificate request appropriately such that the enrollment will complete successfully with the target CA and Keyfactor Command template, which is not configured to build from AD. Any Keyfactor Windows Enrollment Gateway using a client-side template configured with the subject as Build from this Active Directory information must be configured with a workflow step of this type on the Keyfactor Command template that has been mapped in the gateway to that template in order to complete an enrollment through the gateway. There are no configuration parameters for the step.
Important: The template in Keyfactor Command that is mapped to the client-side template configured to build the subject from Active Directory also needs to be configured with three enrollment fields to support handling the incoming subject, SANs, and/or SID. For more information about configuring this, see the Keyfactor Windows Enrollment Gateway Installation and Configuration Guide.
-
NOOPStep
An entry or exit step in which no operation occurs. Steps of this type indicate the start and end of the workflow.
Tip: For steps that send email messages, the SMTP settings and sender information come from the standard Keyfactor Command SMTP configuration (see SMTP) and are not configured individually in the workflow steps.
|
| Enabled |
A Boolean indicating whether the step is enabled to run (true) or not (false). |
| Configuration Parameters |
An object containing the configuration parameters for the workflow definition step. These will vary depending on the type of workflow and the type of step (see ExtensionName). Show  CustomPowerShell, CustomPowerShell,  Email, Email,  EnrollmentAgent, EnrollmentAgent,  ExpirationRenewal, ExpirationRenewal,  OAuthRestRequest, OAuthRestRequest,  PowerShell, PowerShell,  RequireApproval, or RequireApproval, or  RestRequest parameter details. RestRequest parameter details.
Note: There are no ConfigurationParameters for steps of type SubjectFormatter, EnrollStep, RevokeStep, or NOOPStep.
| Script Parameters |
An object defining any parameters to be used in the PowerShell script. |
| Script Name |
A string containing the Keyfactor Command reference name of PowerShell script as stored in the Keyfactor Command database (see Extensions Scripts).
A sample PowerShell script (CustomPowershellExample.ps1) is provided in the \ExtensionLibrary\net6.0\Workflow directory on the Keyfactor Command server under the install directory. By default, this is:
C:\Program Files\Keyfactor\Keyfactor Platform \ExtensionLibrary\net6.0\Workflow
|
Tip: Tokens (a.k.a. substitutable special text) may be used in the script parameter value field. Tokens use a variable in the workflow definition that is replaced by data from the certificate request, certificate, or certificate metadata at processing time. For example, you can take the revocation comment entered when the revocation request is approved—$(cmnt)—and append additional data to it using PowerShell.
| Subject |
A string indicating the subject line for the email message that will be delivered when the workflow definition step is executed.
|
| Message |
A string indicating the email message that will be delivered when the workflow definition step is executed. The email message is made up of regular text and tokens. If desired, you can format the message body using HTML. For example, for an enrollment pending request notification:
Copy
"Hello, \n\nA certificate using the $(template) template was requested by $(requester:displayname) from $(CA) on $(subdate). The certificate details include: \n\n<table> \n<tr><th>Certificate Details</th><th>Metadata</th></tr> \n<tr><td>CN: $(request:cn)</td><td>App Owner First Name: $(metadata:AppOwnerFirstName)</td></tr> \n<tr><td>DN: $(request:dn)</td><td>App Owner Last Name: $(metadata:AppOwnerLastName)</td></tr> \n<tr><td>SANs: $(sans)</td><td>App Owner Email Address: $(metadata:AppOwnerEmailAddress)</td></tr> \n<tr><td> </td><td>Business Critical: $(metadata:BusinessCritical)</td></tr> \n\nPlease review this request and issue the certificate as appropriate by going here: \n\n$(reviewlink) \n\nThanks! \n\nYour Certificate Management Tool\n"
See Table 13: Tokens for Workflow Definitions for a complete list of available tokens.
Note: The $(requester:displayname) substitutable special text token is only supported in environments using Active Directory as an identity provider.
|
| Recipients |
An array of strings containing the recipients for the workflow definition email. Each email message can have multiple recipients. You can use specific email addresses and/or use tokens to replace an email address variable with actual email addresses at processing time. Available email tokens include:
-
$(requester:mail)
The certificate requester, based on a lookup in Active Directory of the email address associated with the requester on the certificate.
Note: The $(requester:mail) substitutable special text token is only supported in environments using Active Directory as an identity provider.
-
Your custom email-based metadata field, which would be specified similarly to $(metadata:AppOwnerEmailAddress).
|
Tip: Tokens (a.k.a. substitutable special text) may be used in the subject line, message and email recipient fields. Tokens use a variable in the workflow definition that is replaced by data from the certificate request, certificate, or certificate metadata at processing time. For example, you can select $(requester) in the workflow definition for an enrollment request and the email message will contain the specific certificate requester name instead of the variable $(requester).
| Enrollment Agent Cert |
A string containing the base-64-encoded representation of the enrollment agent certificate with private key (in PKCS#12 format) that will be used to sign the CSR. This can be either a user certificate or a computer certificate and must have a Certificate Request Agent EKU.
|
| Enrollment Agent Cert Password |
An object indicating the password information used to secure the private key of the enrollment agent certificate.
Supported methods to store secret information are:
-
Store the secret information in the Keyfactor secrets table.
A Keyfactor secret is a user-defined username or password that is encrypted and stored securely in the Keyfactor Command database.
-
Load the secret information from a PAM provider.
See Privileged Access Management (PAM) for more information.
Due to its sensitive nature, this value is not returned in responses.
|
| CA |
An integer indicating the Keyfactor Command reference ID of the certificate authority to use when requesting a new certificate on running expiration workflows with a renewal step. The template must be available from the selected certificate authority. |
| Template |
An integer indicating the Keyfactor Command reference ID of the template to use when requesting a new certificate on running expiration workflows with a renewal step. |
| Headers |
An object containing the header information for the request. The key is the name of the specific request header (for Keyfactor API request headers, see Table 97: Common Request Headers and the specific documentation for each endpoint) and the value is the value that should be set for that header. For a Keyfactor API request, this might look like:
Copy
"Headers": {
"x-keyfactor-requested-with": [
"APIClient"
],
"x-keyfactor-api-version": [
"2"
]
}
Tip: For a Keyfactor API request, version 1 is assumed if no version is specified. Content type and authorization headers do not need to be specified, since those are addressed elsewhere in the configuration.
|
| Data Bucket Property |
A string containing the variable that the response from the request will be returned in, if any. You can then reference this parameter from subsequent steps in the workflow.
Tip: The response is stored as a serialized JObject. To make use of only a portion of the response data in your subsequent step, use JSON path syntax. For example, say you returned the data from a GET /Agents request in a variable called MyResponse and you wanted to reference the ClientMachine name for the orchestrator in a subsequent email message. To limit the data to the first result and only the ClientMachine name, in the email message you would enter the following: $(MyResponse.[0].ClientMachine)
|
| Verb |
A string indicating the HTTP verb for the type of request to perform. Supported values are:
-
DELETE
-
GET
-
HEAD
-
OPTIONS
-
POST
-
PUT
-
TRACE
|
| client_id |
A string indicating the ID of the identity provider client that should be used to authenticate the session (see Authenticating to the Keyfactor API).
|
| client_ secret |
An object indicating the secret of the identity provider client that should be used to authenticate the session (see Authenticating to the Keyfactor API).
Supported methods to store secret information are:
-
Store the secret information in the Keyfactor secrets table.
A Keyfactor secret is a user-defined username or password that is encrypted and stored securely in the Keyfactor Command database.
-
Load the secret information from a PAM provider.
See Privileged Access Management (PAM) for more information.
Due to its sensitive nature, this value is not returned in responses.
|
| Token Endpoint |
A string container the URL of the token endpoint for your identity provider. For example:
Copy
https://my-keyidp-server.keyexample.com/realms/Keyfactor/protocol/openid-connect/token
For Keyfactor Identity Provider, this is included among the information that can be found on the OpenID Endpoint Configuration page, a link to which can be found on the Realm Settings page (see Configuring Keyfactor Identity Provider and Collecting Data for the Keyfactor Command Installation).
|
| Scope |
One or more scopes that are submitted with the token request, if desired. Multiple scopes should be separated by spaces.
This value is not used for Keyfactor Identity Provider.
|
| Audience |
An audience value that is submitted with the token request, if desired.
This value is not used for Keyfactor Identity Provider.
|
| URL |
A string containing the URL for the request, including tokens, if desired. For a Keyfactor API request, this might look like:
Copy
https://keyfactor.keyexample.com/KeyfactorAPI/Certificates?pq.queryString=CN%20-contains%20%22appsrvr14%22%20AND%20CertStorePath%20-ne%20NULL
Or, with tokens:
Copy
https://keyfactor.keyexample.com/KeyfactorAPI/Certificates/$(certid)
Note: To prevent REST requests from being made to inappropriate locations by malicious users, configure a system environment variable of KEYFACTOR_BLOCKED_OUTBOUND_IPS on your Keyfactor Command server pointing to the IP address or range of addresses in CIDR format that you wish to block. Both IPv4 and IPv6 addresses are supported. More than one address or range may be specified in a comma-delimited list. For example: 192.168.12.0/24,192.168.14.22/24 When a REST request is made where the URL is either configured to a blocked IP address or resolves via DNS to a blocked IP address, the REST request will fail.
|
| Content Type |
A string indicating the content type for the request. Supported values are:
|
| Request Content |
A string containing the body of the REST request, if needed. For a Keyfactor API request, this will vary depending on the request and might look like (for a PUT /Certificates/Metadata request):
Copy
{
"Id": "$(certid)",
"Metadata":{
"RevocationComment": "$(cmnt)"
}
}
Note: This example assumes you have a metadata field called RevocationComment.
|
Tip: Tokens (a.k.a. substitutable special text) may be used in the URL and request content fields. Tokens use a variable in the workflow definition that is replaced by data from the certificate request, certificate, or certificate metadata at processing time. For example, you can take the revocation comment entered when the revocation request is approved—$(cmnt)—and insert it into a custom metadata field in the certificate by doing a PUT /Certificates/Metadata request for the $(id).
| Script Parameters |
An object defining any parameters to be used in the PowerShell script. The key is the name of a custom parameter defined by you and the value is the initial value that should be set for that parameter before the PowerShell is executed, if any. Tokens are supported in the value. |
| Script Content |
A string containing the PowerShell commands to execute. This should be the actual contents of the PowerShell script (the PowerShell commands and supporting components), not a path and filename to an external file.
|
Tip: Tokens (a.k.a. substitutable special text) may be used in the script parameter value field. Tokens use a variable in the workflow definition that is replaced by data from the certificate request, certificate, or certificate metadata at processing time. For example, you can take the revocation comment entered when the revocation request is approved—$(cmnt)—and append additional data to it using PowerShell.
| Minimum Approvals |
In integer indicating the minimum number of users who must approve the request to allow the request to complete. |
| Denial Email Subject |
A string indicating the subject line for the email message that will be delivered if the request is denied.
|
| Denial Email Message |
A string indicating the email message that will be delivered if the request is denied. The email message is made up of regular text and tokens. If desired, you can format the message body using HTML.
See Table 13: Tokens for Workflow Definitions for a complete list of available tokens.
|
| Denial Email Recipients |
An array of strings containing the recipients for the denial email. Each email message can have multiple recipients. You can use specific email addresses and/or use tokens to replace an email address variable with actual email addresses at processing time. Available email tokens include:
-
$(requester:mail)
The certificate requester, based on a lookup in Active Directory of the email address associated with the requester on the certificate.
Note: The $(requester:mail) substitutable special text token is only supported in environments using Active Directory as an identity provider.
-
Your custom email-based metadata field, which would be specified similarly to $(metadata:AppOwnerEmailAddress).
|
| Approval Email Subject |
A string indicating the subject line for the email message that will be delivered if the request is approved.
|
| Approval Email Message |
A string indicating the email message that will be delivered if the request is approved. The email message is made up of regular text and tokens. If desired, you can format the message body using HTML.
See Table 13: Tokens for Workflow Definitions for a complete list of available tokens.
|
| Approval Email Recipients |
An array of strings containing the recipients for the approval email. Each email message can have multiple recipients. You can use specific email addresses and/or use tokens to replace an email address variable with actual email addresses at processing time. Available email tokens include:
-
$(requester:mail)
The certificate requester, based on a lookup in Active Directory of the email address associated with the requester on the certificate.
Note: The $(requester:mail) substitutable special text token is only supported in environments using Active Directory as an identity provider.
-
Your custom email-based metadata field, which would be specified similarly to $(metadata:AppOwnerEmailAddress).
|
Tip: Tokens (a.k.a. substitutable special text) may be used in the subject line, message and email recipient fields. Tokens use a variable in the workflow definition that is replaced by data from the certificate request, certificate, or certificate metadata at processing time. For example, you can select $(requester) in the workflow definition for an enrollment request and the email message will contain the specific certificate requester name instead of the variable $(requester).
| Headers |
An object containing the header information for the request. The key is the name of the specific request header (for Keyfactor API request headers, see Table 97: Common Request Headers and the specific documentation for each endpoint) and the value is the value that should be set for that header. For a Keyfactor API request, this might look like:
Copy
"Headers": {
"x-keyfactor-requested-with": [
"APIClient"
],
"x-keyfactor-api-version": [
"2"
]
}
Tip: For a Keyfactor API request, version 1 is assumed if no version is specified. Content type and authorization headers do not need to be specified, since those are addressed elsewhere in the configuration.
|
| Data Bucket Property |
A string containing the variable that the response from the request will be returned in, if any. You can then reference this parameter from subsequent steps in the workflow.
Tip: The response is stored as a serialized JObject. To make use of only a portion of the response data in your subsequent step, use JSON path syntax. For example, say you returned the data from a GET /Agents request in a variable called MyResponse and you wanted to reference the ClientMachine name for the orchestrator in a subsequent email message. To limit the data to the first result and only the ClientMachine name, in the email message you would enter the following: $(MyResponse.[0].ClientMachine)
|
| Verb |
A string indicating the HTTP verb for the type of request to perform. Supported values are:
-
DELETE
-
GET
-
HEAD
-
OPTIONS
-
POST
-
PUT
-
TRACE
|
| Use Basic Auth |
A Boolean indicating whether Basic authentication should be used for the request (True) or not (False).
If UseBasicAuth is False, Windows authentication in the context of the Keyfactor Command application pool user will be used (see Create Service Accounts for Keyfactor Command).
|
| Basic Username |
An object indicating the username information to use for authentication if UseBasicAuth is True.
Supported methods to store secret information are:
-
Store the secret information in the Keyfactor secrets table.
A Keyfactor secret is a user-defined username or password that is encrypted and stored securely in the Keyfactor Command database.
-
Load the secret information from a PAM provider.
See Privileged Access Management (PAM) for more information.
Due to its sensitive nature, this value is not returned in responses.
|
| Basic Password |
An object indicating the password information to use for authentication if UseBasicAuth is True. The syntax is the same as for BasicUsername.
Due to its sensitive nature, this value is not returned in responses.
|
| URL |
A string containing the URL for the request, including tokens, if desired. For a Keyfactor API request, this might look like:
Copy
https://keyfactor.keyexample.com/KeyfactorAPI/Certificates?pq.queryString=CN%20-contains%20%22appsrvr14%22%20AND%20CertStorePath%20-ne%20NULL
Or, with tokens:
Copy
https://keyfactor.keyexample.com/KeyfactorAPI/Certificates/$(certid)
Note: To prevent REST requests from being made to inappropriate locations by malicious users, configure a system environment variable of KEYFACTOR_BLOCKED_OUTBOUND_IPS on your Keyfactor Command server pointing to the IP address or range of addresses in CIDR format that you wish to block. Both IPv4 and IPv6 addresses are supported. More than one address or range may be specified in a comma-delimited list. For example: 192.168.12.0/24,192.168.14.22/24 When a REST request is made where the URL is either configured to a blocked IP address or resolves via DNS to a blocked IP address, the REST request will fail.
|
| Content Type |
A string indicating the content type for the request. Supported values are:
|
| Request Content |
A string containing the body of the REST request, if needed. For a Keyfactor API request, this will vary depending on the request and might look like (for a PUT /Certificates/Metadata request):
Copy
{
"Id": "$(certid)",
"Metadata":{
"RevocationComment": "$(cmnt)"
}
}
Note: This example assumes you have a metadata field called RevocationComment.
|
Tip: Tokens (a.k.a. substitutable special text) may be used in the URL and request content fields. Tokens use a variable in the workflow definition that is replaced by data from the certificate request, certificate, or certificate metadata at processing time. For example, you can take the revocation comment entered when the revocation request is approved—$(cmnt)—and insert it into a custom metadata field in the certificate by doing a PUT /Certificates/Metadata request for the $(id).
|
| Signals |
An array of objects containing data used at the point in the workflow step where the workflow needs to continue based on user input. These will vary depending on the type of workflow and the type of step (see ExtensionName).  Show RequireApproval signal details. Show RequireApproval signal details.
| RoleIds |
An array of integers indicating the security roles whose members are allowed to approve the request.
|
| Signal Name |
A string indicating the name of the signal. This value will vary depending on the workflow step. For the built-in Require Approval step, the SignalName is ApprovalStatus.
|
Important: If all the security roles configured for a workflow step are deleted from Keyfactor Command, no users will be able to submit signals for workflow instances initiated with that workflow definition. To remedy this, update the workflow definition with one or more current security roles, re-publish it, and then restart any outstanding workflow instances.
|
| Conditions |
An object containing conditions indicating whether the step should run (true) or not (false). Conditions may either have a static value of True or False or a token that will have a value of True or False at the time the step is run. More than one condition may be added. If multiple conditions are used in the same step, all conditions must have a value of True at the time the step is evaluated to be run in order for the step to run. If any single condition evaluates to False, the step will not run.  Show condition details. Show condition details.
| Id |
A string indicating the Keyfactor Command reference GUID of the condition.
|
| Value |
A string indicating the value of the condition. This should be one of true, false, or a token that will be set to either true or false in an earlier step in the workflow (see Adding, Copying or Modifying a Workflow Definition for an example).
|
|
| Outputs |
An object indicating the next step in the workflow.  Show output details. Show output details.
| continue |
A string indicating the UniqueName of the next workflow step in the chain. This value will be null for the final step in the chain.
|
|
|
![]() A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked./Definitions/{definitionid} method is used to update the name and description for the workflow definition with the specified GUID. This method returns HTTP 200 OK on a success with details about the updated workflow definition.
A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked./Definitions/{definitionid} method is used to update the name and description for the workflow definition with the specified GUID. This method returns HTTP 200 OK on a success with details about the updated workflow definition.