The expiration renewal event handler allows you to execute a certificate renewal automatically for each expiring certificate that is found in a supported certificate store for each expiration alert when the alert task is triggered by the execution of the expiration alerts using the legacy alerting system. In order for the renewal handler to execute successfully, the user under which the request is being processed needs appropriate permissions to complete this task. Which user this is depends on your identity provider:
-
If you’re using Active Directory as an identity provider and either a DCOM or HTTPS CA
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA., the Active Directory service account under which the Keyfactor Command Service runs must have select permissions in Keyfactor Command. In addition, if you wish to test the execution of expiration alerts with renewal handlers or workflows and your Keyfactor API
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA., the Active Directory service account under which the Keyfactor Command Service runs must have select permissions in Keyfactor Command. In addition, if you wish to test the execution of expiration alerts with renewal handlers or workflows and your Keyfactor API A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. IIS application pool runs in the context of a different Active Directory service account than the Keyfactor Command Service, the Active Directory service account for the Keyfactor API IIS application pool must also be granted these permissions.
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. IIS application pool runs in the context of a different Active Directory service account than the Keyfactor Command Service, the Active Directory service account for the Keyfactor API IIS application pool must also be granted these permissions. -
If you’re using OAuth as an identity provider and either a DCOM or HTTPS CA, the permissions described here need to be granted to the client created to allow Keyfactor Command to make API requests to itself (see Identity Provider Token Credentials Section).
If you don’t plan to use the expiration renewal handler with the legacy alerting system, you can skip this step.
To configure permissions to support use of the expiration renewal handler:
- In the Keyfactor Command Management Portal, browse to System Settings Icon
 > Security Roles & Claims.
> Security Roles & Claims. - On the Security Roles and Claims page on the Claims tab, click Add to add a new security claim if one does not exist already. See above for the user(s) for which you will need claim(s).
-
In the Add Claim dialog, select an appropriate Claim Type for your identity provider type (e.g. Active Directory User). Enter the Claim Value for the user. For an Active Directory user, for example, enter the Active Directory user name of the service account under which the Keyfactor Command Service runs using DOMAIN\username format in the Claim Value. Select your Claim Provider (Active Directory or your OAuth identity provider) and enter an appropriate Description. Click Save. The new claim will be saved and the dialog will close.
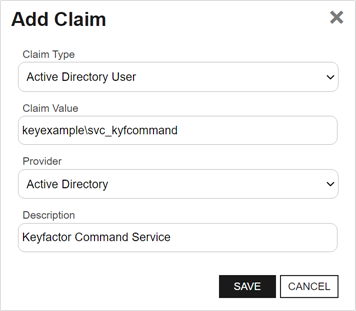
Figure 570: Configure Expiration Renewal Handler: Add New Claim for an Active Directory User
- If you’re using Active Directory as an identity provider and your Keyfactor API IIS application pool runs as a different Active Directory service account from that used for the Keyfactor Command Service, repeat steps two and three for the IIS application pool service account.
- On the Security Roles and Claims page on the Security Roles tab, click Add to create a new role to be used just to grant permissions to the service account(s) to support use of the expiration renewal handler.
- On the Details tab, give it an appropriate name and description to reflect this usage.
-
On the Global Permissions tab:
- In the Certificate Stores section, check the Read and Schedule boxes to enable them.
- In the Certificates>Enrollment section, check the Pfx box to enable it.
- In the Certificates>Collections section, check the Read box to enable it.
- In the Portal section, and uncheck the Read box to disable it, if enabled.
-
On the Claims tab, associate the claims you added for the renewal handler with the role.
- Click Save to save the role.
- Edit the CA and template
 A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. that will be used for renewal and add the renewal role to the Allowed Requester Security Roles, if you’re not using delegation for enrollment
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. that will be used for renewal and add the renewal role to the Allowed Requester Security Roles, if you’re not using delegation for enrollment Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA).. If you’re using Active Directory as an identity provider and delegation for enrollment, you will need to grant to permissions separately on the CA and template to the Active Directory service accounts.
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA).. If you’re using Active Directory as an identity provider and delegation for enrollment, you will need to grant to permissions separately on the CA and template to the Active Directory service accounts.