SSH![]() The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. service account keys are acquired by administrators for use with applications and other non-end-user purposes. On the Service Account Keys page, an administrator can view and download existing keys issued for service accounts and generate new key pairs.
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. service account keys are acquired by administrators for use with applications and other non-end-user purposes. On the Service Account Keys page, an administrator can view and download existing keys issued for service accounts and generate new key pairs.
- Uses the Keyfactor CommandManagement Portal to create a new key pair (see Create a Service Account Key). She enters the following information in the form:
- Key Type: Ed25519
- Key Length: 256
Server Group: Server Group One
The server group to which the Linux servers belong that the public key
 In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. will be distributed to.
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. will be distributed to.Client Hostname: appsrvr75
The Linux server on which the private key
 Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. of the SSH key pair will be download. This does not need to be a server added for management in Keyfactor Command and is a field for reference only.
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. of the SSH key pair will be download. This does not need to be a server added for management in Keyfactor Command and is a field for reference only.Username: svc_greenchicken
The service account name the application uses. This does not need to match the Linux logon name the application uses. This username together with the client hostname
 The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). make the full user name for the service account key within Keyfactor Command svc_greenchicken@appsrvr75.
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). make the full user name for the service account key within Keyfactor Command svc_greenchicken@appsrvr75.Email: pkiadmins@keyexample.com
The group responsible for rotating the key when it reaches the end of its lifetime. This group will receive email alerts when the key is becoming stale.
Passphrase: A complex password used to secure the private key.
She needs to record the passphrase because this will be needed by application to access the private key.
- Comment: Green Chicken Service
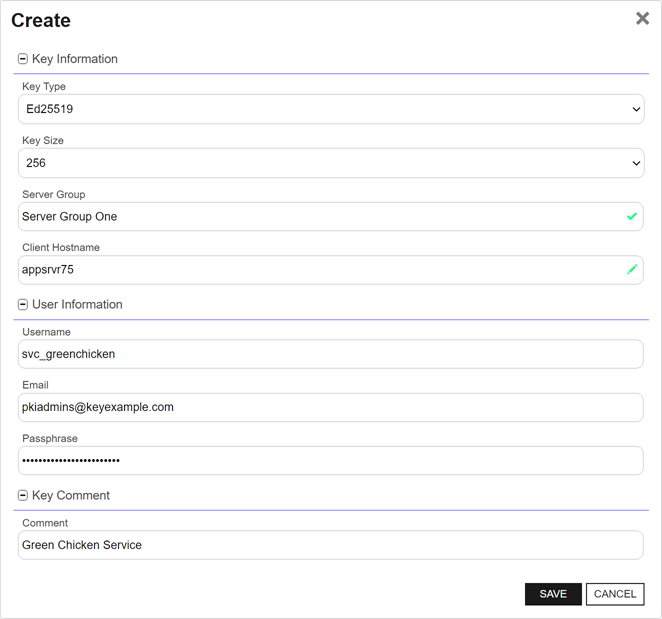
Figure 327: Acquire a New Service Account Key
- Downloads the SSH private key on the server doing the log collection
 The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports)., from which the SSH connections will be made to collect logs.
The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports)., from which the SSH connections will be made to collect logs. Uses the Management Portal to map the new public key for the full service account user name (svc_greenchicken@appsrvr75) to the Linux logons for the service on the servers from which the logs will be collected (see Edit Access to a Server Group).
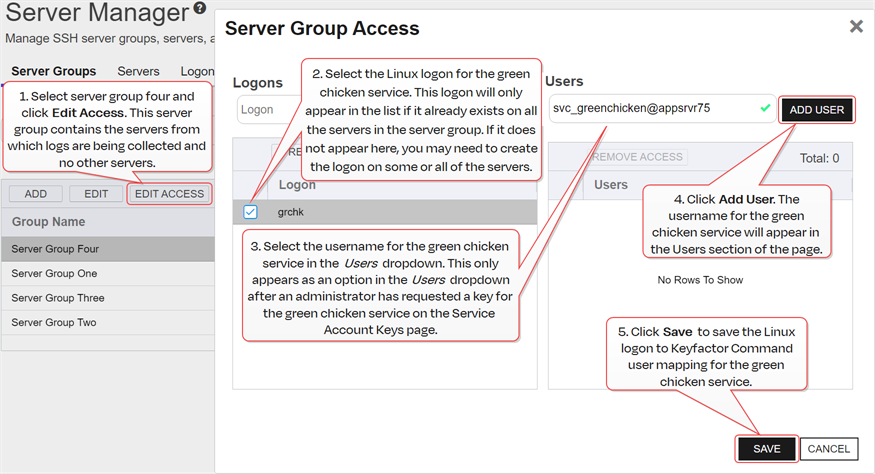
Figure 328: Map Service Account Public Key to Logon
Note: The servers that the logs will be collected from are organized into a server group so the administrator can create logons and map the service account key using the Access Management option on the Server Group page. If the servers were in different server groups or the server group contained servers which should not be updated with logons and keys for the green chicken service, the administrator would need to create the logons and mappings separately for each server using the Access Management option on the Servers page (see Edit Access to an SSH Server).- Waits for the public key to be published to the servers. The time that this takes depends on the frequency of the server group synchronization schedule (see Add or Edit a Server Group).
- Confirms that the service is able to successfully connect using secured SSH.
 Create a Service Account Key
Create a Service Account Key
To create a new service account key:
- In the Management Portal, browse to SSH > Service Account Keys.
-
On the Service Account Keys page, click Create.
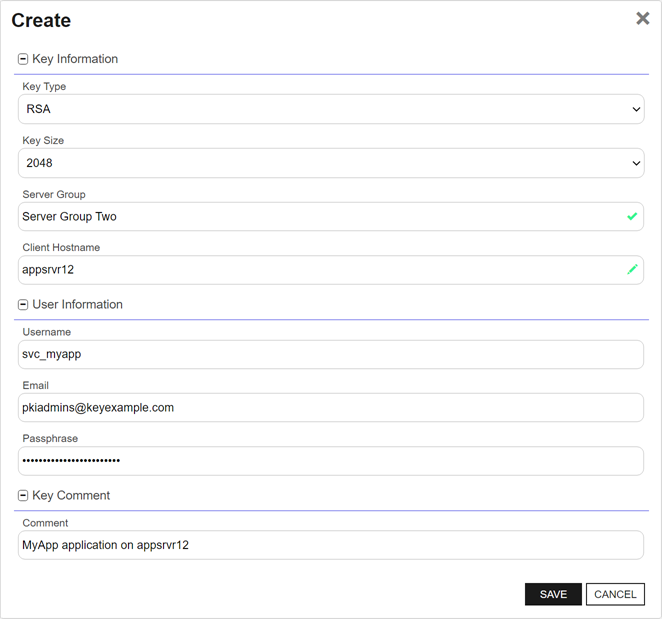
Figure 329: Add a Service Account Key
- In the Key Information section of the Create dialog, select a Key Type in the dropdown (see Key Type).
- In the Key Information section, select a Key Length in the dropdown (see Key Length). The available key lengths will vary depending upon the option select in the Key Type dropdown.
- In the Key Information section, select a Server Group in the dropdown (see SSH Server Group Operations). The server group is used to control who has access in the Management Portal to the service account key. It does not limit where the key can be published. This field is required.
- In the Key Information section, enter a Client Hostname reference for the service account key. This field is used for reference only and does not need to match an actual client hostname. It is used when building the full user name of the service account key for mapping to Linux logons for publishing to Linux servers (e.g. username@client_hostname). The naming convention is to enter the hostname of the server on which the application that will use the private key resides (e.g. appsrvr12), but you can put anything you like in this field (e.g. cheesetoast). This field is required.
- In the User Information section of the page, enter the Username of the service account that will be using the key to connect to the target server (e.g. svc_myapp). This username will be combined with the Client Hostname to build the full user name of the service account key for mapping to Linux logons (e.g. svc_myapp@appsrvr12). You will need to know this full user name when creating the mappings to publish the public key to the target servers (see Edit Access to a Server Group, Edit Access to an SSH Server, or Add or Edit Access for an SSH Logon). This field is required.
- In the User Information section of the page, enter the Email address of the administrator or group of administrators responsible for managing the key. This is the address to which key rotation alerts for this key will be directed (see Key Rotation Alerts). This field is required.
-
In the User Information section, enter a Passphrase to encrypt the downloaded copy of the private key of the key pair. The service that uses the private key will need to be able to provide it when connecting via SSH. By default, the minimum password length is 12 characters (see the SSH Key Password setting in Application Settings: SSH Tab). This field is required.
Tip: The private key downloads immediately at the conclusion of the creation process, encrypted with this passphrase. You may later download the private key again from this same page and encrypt it with a different passphrase, if desired. -
In the Key Comment section, enter a Comment to include with the key. This field is optional.
Tip: Although entry of an email address in the comment field of an SSH key is traditional, this is not a required format. The comment may contain any characters supported for string fields, including spaces and most punctuation marks. -
Click Save to save the new service account key.
Tip: Once the key pair is generated, an administrator needs to download the private key as an encrypted file and store it locally on the machine from which the service will make SSH connections using the private key. Additionally, an administrator needs to use Keyfactor Command to map the full user name built from the username and client hostname entered when generating the service account key pair (e.g. svc_myapp@appsrvr12) to the Linux logon account that the service account will operate as when logging in via SSH on the target server(s) where the public key needs to reside (see Edit Access to a Server Group, Edit Access to an SSH Server, or Add or Edit Access for an SSH Logon). After this is complete and the orchestrator Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. has published the public key to the target server(s), the service may connect via SSH to the target server(s) using the new private key for authentication. For more information, see SSH.
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. has published the public key to the target server(s), the service may connect via SSH to the target server(s) using the new private key for authentication. For more information, see SSH.
 Edit Service Account Key Information
Edit Service Account Key Information
Once you have generated an SSH key pair, most things about the key pair are fixed and cannot be changed. However, two pieces of key information can be changed for an existing key pair—the email address to which alerts about the key should be directed and the comment associated with the public key.
To modify the email address or key comment:
- In the Management Portal, browse to SSH > Service Account Keys.
- On the Service Account Keys page, double-click the key for the desired service account in the grid, highlight the row in the grid and click Edit at the top of the grid, or right-click the key in the grid and choose Edit from the right-click menu.
-
In the Edit Key dialog, update the Email and Comment fields as needed and click Save.
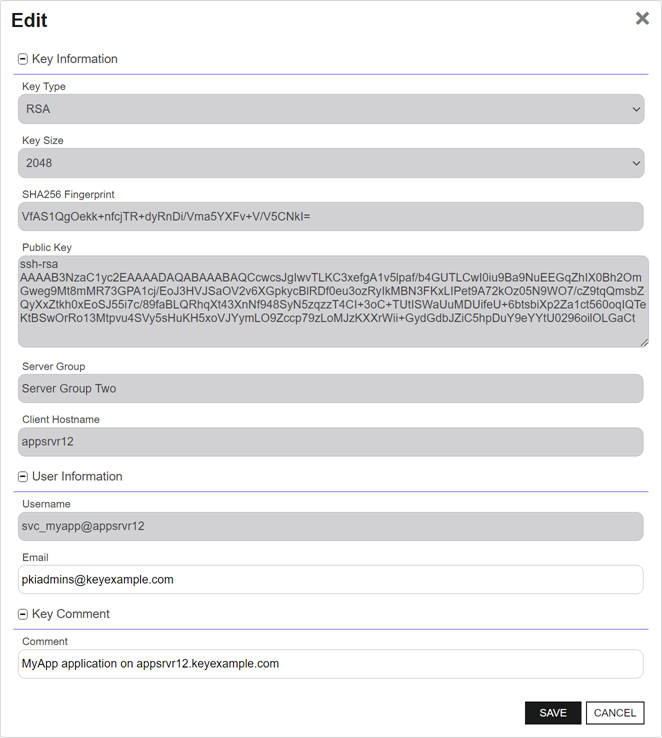
Figure 330: Edit SSH Service Account Key Information
Changes made to the key comment will be published to any mapped logons on associated servers during the next synchronization cycle.
 Rotate a Service Account Key
Rotate a Service Account Key
The rotate key option is used to replace an existing key that is approaching the end of its life or has been compromised. If key rotation alerts have been configured in the environment (see Key Rotation Alerts), the administrator responsible for managing the service account key will receive an email when the key is approaching the end if its lifetime to instruct the him or her to rotate the service account key.
The rotate dialog defaults to all the existing settings of the service account's current key. At its simplest, the administrator may choose to accept all the defaults, enter a passphrase to encrypt the downloaded private key and click save to generate the new key pair.
To rotate a service account key pair:
- In the Management Portal, browse to SSH > Service Account Keys.
-
On the Service Account Keys page, click Rotate.
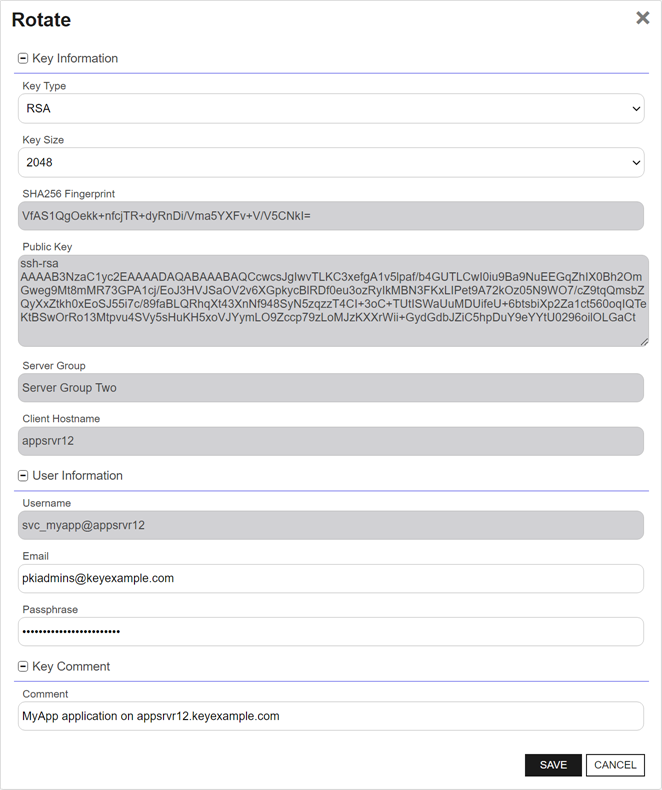
Figure 331: Rotate an SSH Key Pair
- In the Key Information section of the Rotate dialog, modify the existing Key Type in the dropdown, if desired (see Key Type).
- In the Key Information section, modify the existing Key Length in the dropdown, if desired (see Key Length). The available key lengths will vary depending upon the option select in the Key Type dropdown.
- In the User Information section, modify the existing Email address, if desired. This address is used for key rotation alerts (see Key Rotation Alerts). This field is required.
- In the User Information section, enter a Passphrase to encrypt the downloaded copy of the private key of the key pair. You will need to provide this passphrase again when you use the private key to connect via SSH. By default, the minimum password length is 12 characters (see the SSH Key Password setting in Application Settings: SSH Tab). This field is required.
-
In the Key Comment section, modify the existing Comment to include with the key, if desired. This field is optional.
Tip: Although entry of an email address in the comment field of an SSH key is traditional, this is not a required format. The comment may can contain any characters supported for string fields, including spaces and most punctuation marks. - Click Save to create the new key pair.
 Delete a Service Account Key
Delete a Service Account Key
To delete a service account key, highlight the row in the service account keys grid and click Delete at the top of the grid or right-click the key in the grid and choose Delete from the right-click menu.
 Download a Service Account Key
Download a Service Account Key
After generating a key pair, you need to download the private key on the machine from which you will be making SSH connections. Although the private key is encrypted, for best security practice it should not be moved around from machine to machine.
The key downloads in the proprietary OpenSSH private key format, encrypted by a user-defined password.
Only the private key can be downloaded with the download option, though the public key is displayed in the edit dialog and may be copied and pasted to a file, if desired.
To download the private key:
- In the Management Portal, browse to SSH > Service Account Keys.
-
On the Service Account Keys page, locate the key for the desired service account and click Download.
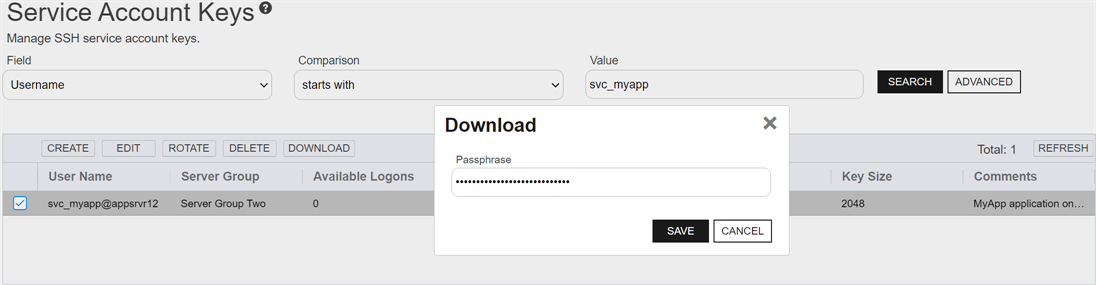
Figure 332: Download a Service Account Private Key
- In the Download dialog, enter a passphrase that will be used to encrypt the private key. By default, the minimum password length is 12 characters (see the SSH Key Password setting in Application Settings: SSH Tab). This field is required.
-
Click Download to save the file to the local machine.
By default, the file has the following name:
SSH-Key-Service-Account.identity
You can also find the help icon (![]() ) at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Software & Documentation Portal at the home page or the Keyfactor API Endpoint Utility.
) at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Software & Documentation Portal at the home page or the Keyfactor API Endpoint Utility.
Keyfactor provides two sets of documentation: the On-Premises Documentation Suite and the Managed Services Documentation Suite. Which documentation set is accessed is determined by the Application Settings: On-Prem Documentation setting (see Application Settings: Console Tab).