September 2021
New Features
-
What problem does it solve?
Provide the ability to associate custom parameters with certificate stores and certificate store entries to associate useful information.
-
How does it work?
The certificate store type dialog now provides tabs for entry parameters, in addition to custom fields. These parameters and custom fields can be defined for input during enrollment
 Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA)., storage and management of certificate store inventory. For more information, see Entry Parameters Tab in the Keyfactor Command Reference Guide.
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA)., storage and management of certificate store inventory. For more information, see Entry Parameters Tab in the Keyfactor Command Reference Guide. -
What’s the benefit?
Flexibility: Allows for further customization around certificate stores which can be dictated by customizable data.
-
What problem does it solve?
The previous version of certificate store inventory leveraged the certificate search functionality. While this worked, it was not always well-suited for the viewing of certificate store inventory.
-
How does it work?
Clicking on the View Inventory button with a certificate store selected will now load a dialog with the inventory of the store.
-
What’s the benefit?
Ease-of-Use: Enables administrators to efficiently review certificate store inventory.
-
What problem does it solve?
The previous certificate store type parameters were defined via a comma-separated list and were not strongly typed.
-
How does it work?
A formalized list is available to define parameters explicitly, including type (String, Boolean, Multiple Choice, Secret).
-
What’s the benefit?
Flexibility: Enables more powerful definition of certificate stores and data-validity checking.
-
What problem does it solve?
The current on-boarding of certificate stores requires manual data entry of custom fields and parameters.
-
How does it work?
The Keyfactor Command orchestrator
 Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. framework provides for orchestrators to report certificate store entry parameters.
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. framework provides for orchestrators to report certificate store entry parameters. -
What’s the benefit?
Flexibility: Enables customers to more easily track new certificate stores and changes to them made out-of-band from Keyfactor Command.
The Keyfactor Command server configuration wizard now supports entry of group managed service accounts (gMSA) in the Administrative Users field on the Keyfactor Portal tab.
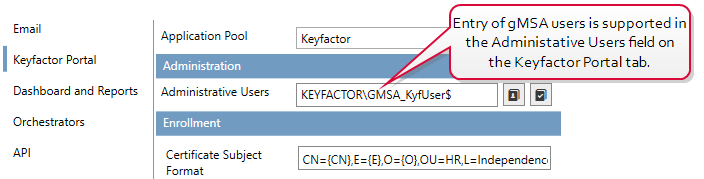
Figure 628: Entry of gMSA Users in the Administrative Users Field
Updates and Improvements
-
Job Completion
Job completion handler is now provided the certificate identifier upon renewal so that the handler can perform any related tasks.
-
API Endpoint Deprecation
The CertificateCollections/{id}/Permissions endpoint
 An endpoint is a URL that enables the API to gain access to resources on a server. due to an update slated for the Keyfactor Command v10 release and the fact that the endpoint is not updating permissions properly.
An endpoint is a URL that enables the API to gain access to resources on a server. due to an update slated for the Keyfactor Command v10 release and the fact that the endpoint is not updating permissions properly. -
Permissions Message
An incorrect error message was displayed to users without sufficient permissions to a certificate collection
 The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports)..
The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports).. -
Certificate Store Deletion
Fixed an issue in which a Certificate Store cannot be deleted if there is a job staged against it.
-
Pending Alerts
Pending alerts were being sent on certificate issuance regardless of the associated template
 A certificate template defines the policies and rules that a CA uses when a request for a certificate is received..
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received..
-
Certificate Inventory
Corrected a permissions problem in which users with only read permissions on a Certificate Store were unable to view inventory of that certificate store.
Known Issues
- CSR Enrollment
In cases where there are duplicate template names in multiple forests, CSR
 A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment can sometimes go to the wrong CA
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment can sometimes go to the wrong CA A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA.. This will be fixed in a future incremental release. Customers with environments with duplicate templates should wait to upgrade.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA.. This will be fixed in a future incremental release. Customers with environments with duplicate templates should wait to upgrade.
API Endpoint Change Log
Table 887: API Change Log
| Endpoint | Methods | Action | Notes |
|---|---|---|---|
| /CertificateStores/ {id}/ Inventory | GET | Add | |
| /Enrollment/ PFX/ Replace | POST | Fix | SuccessfulStores collection now only includes Ids of stores that were successfully processed. |
| /Enrollment/ PFX/ Deploy | POST | Update | Now allows for multiple stores of the same type with different parameters. |
| /CertStoreTypes | POST/PUT | Update | EntryParameters can now be set via these methods. |
| /CertificateStores/ Certificates/ Add | POST | Update | Now allows for multiple stores of the same type with different parameters. |
| /CertificateStores/ Certificates/ Remove | POST | Update | Now allows for multiple stores of the same type with different parameters. |
| /CertificateCollections/ {id}/ Permissions | GET | Deprecate |