On the Access Management tab of the Edit Logon dialog, you can map Keyfactor user accounts to Linux logon account to cause the SSH![]() The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. keys in Keyfactor Command associated with thoseKeyfactor users to be published to the authorized_keys file of the Linux user (see SSH).
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. keys in Keyfactor Command associated with thoseKeyfactor users to be published to the authorized_keys file of the Linux user (see SSH).
To map an Keyfactor Command user to a Linux logon:
- In the Management Portal, browse to SSH > Server Manager.
- On the Server Manager page, select the Logons tab.
- In the Logons grid locate the logon that you wish to publish an SSH key to by mapping an Active Directory account to it. Be sure to select the logon associated with the correct server, as the same logon name may appear for multiple servers.
- Double-click the logon, right-click the logon and choose Edit from the right-click menu, or highlight the row in the logons grid and click Edit at the top of the grid.
-
On the Access Management tab in the Users & Groups with Login Access dropdown, select a user or service account to associate the logon with. Only Keyfactor users that have keys stored in Keyfactor Command, that have been designated as server group owners, or AD users or groups that have been previously entered for association with a logon will appear in the dropdown. If desired, you may enter an Active Directory user or group name in this field. Using an Active Directory group to create Linux logon to Keyfactor user mappings will cause the keys stored in Keyfactor Command for any Active Directory users that are members of this group to be mapped to the selected Linux logon and published to the server on which the Linux logon exists. Any Active Directory users that are members of this group but who do not have keys stored in Keyfactor Command will not be mapped to the selected Linux logon. Click Add.
Tip: For keys created through the My SSH Key portal (see My SSH Key), a Keyfactor user is an Active Directory user account. For keys created through the Service Account Keys page (see Service Account Keys), a Keyfactor user is a user-generated service account name of the form servicename@hostname The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername)..
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername).. 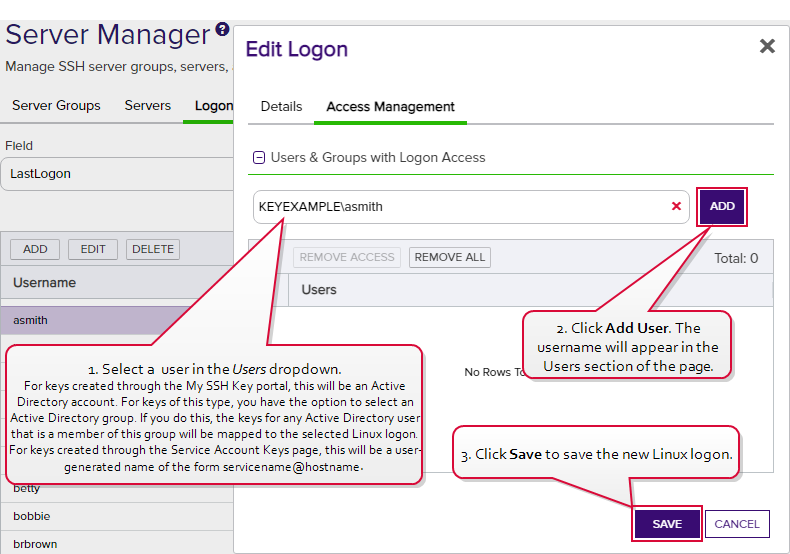
Figure 327: Edit Access for a Linux Logon
- Click Save to save the access management settings.
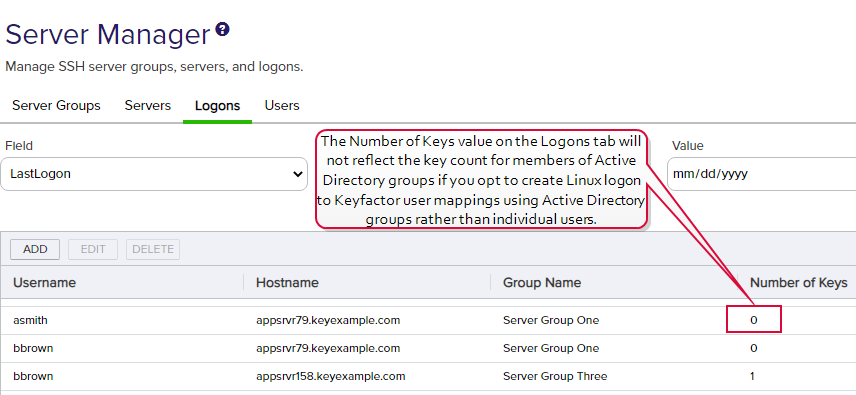
Figure 328: Creating Linux Logon to Keyfactor User Mappings Using Active Directory Groups Key Value
To delete a logon, highlight the row in the logons grid and click Delete at the top of the grid or right-click the logon in the grid and choose Delete from the right-click menu.