Keyfactor Command uses the Logi Analytics Platform to provide a number of built-in reports based on certificate data in the Keyfactor Command database. These reports are available for viewing through the Management Portal, if you configured that option during the installation and configuration process (see Dashboard and Reports Tab in the Keyfactor Command Server Installation Guide). The reports can also be configured to save to a network path or deliver via email periodically, if desired.
As of Keyfactor Command version 10, Logi has been upgraded to v14 SP2 and a new Logi license is included in the application.
Once a report has been generated, you may be able to export it to either PDF, Excel, or CSV. The export file types available for each standard report are shown in Table 5: Chart of Available Exports per Standard Report.
Table 5: Chart of Available Exports per Standard Report
| PDF and Excel | Excel and CSV | PDF, Excel and CSV |
|---|---|---|
| Certificate Count by Template | Certificates Found at TLS/SSL Endpoints | Certificate Count Grouped by Single Metadata Fields |
| Certificate Count by User per Template | Certificates in Collection | |
| Certificate by Key Strength | Expiration Report by Days | |
| Certificates by Revoker | Full Certificate Extract | |
| Certificates by Type and Java Keystores | Revoked Certificates in Certificate Stores | |
| Certificate Issuance Trends with Metadata | SSH Keys with Root Logon Access | |
| Expiration Report | SSH Trusted Public Keys with No Known Private Key | |
| Issued Certificates Per Certificate Authority | SSH Key Usage Report | |
| Monthly Executive Report | ||
| PKI Status for Collection | ||
| Statistical Report | ||
| SSH Keys by Age |
 Report Drill-down
Report Drill-down
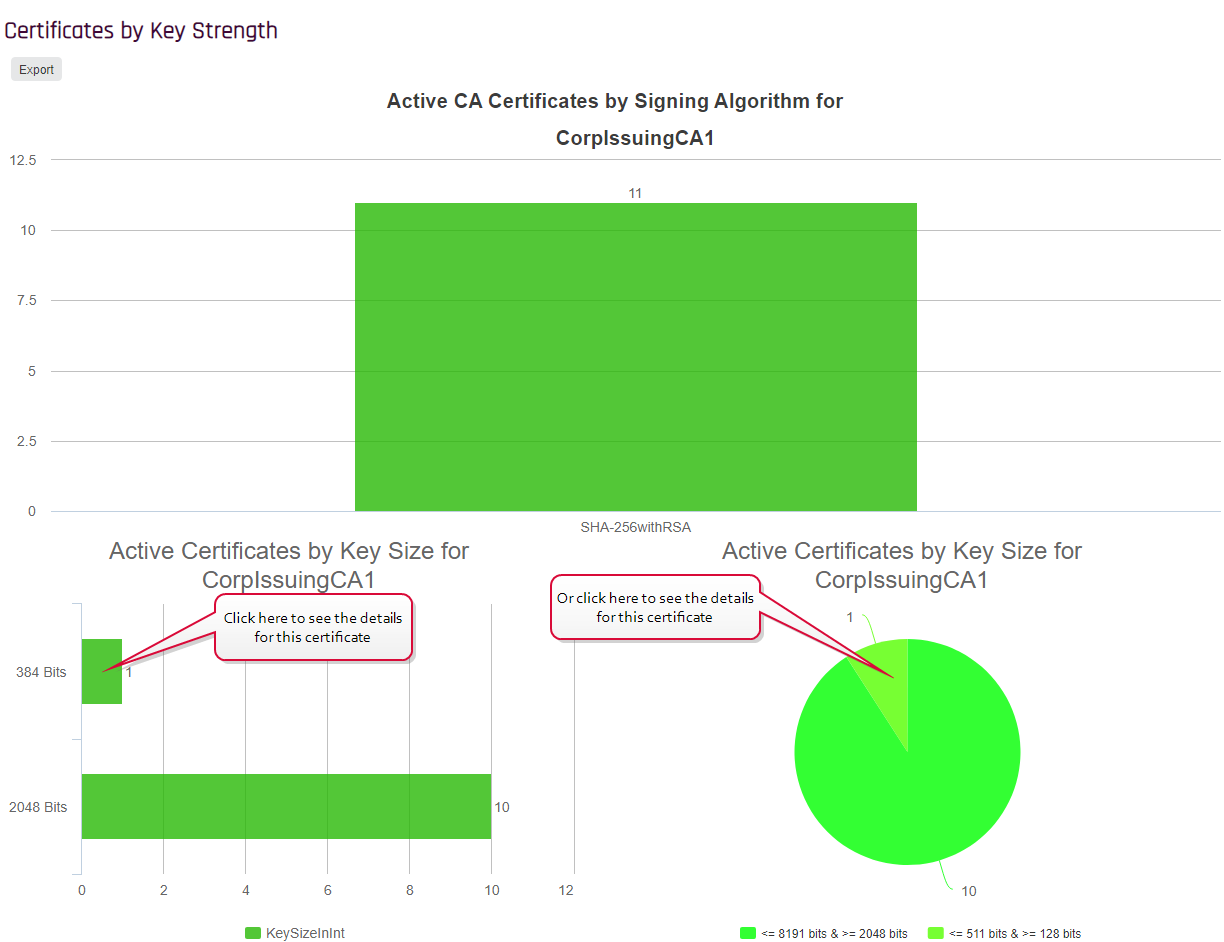
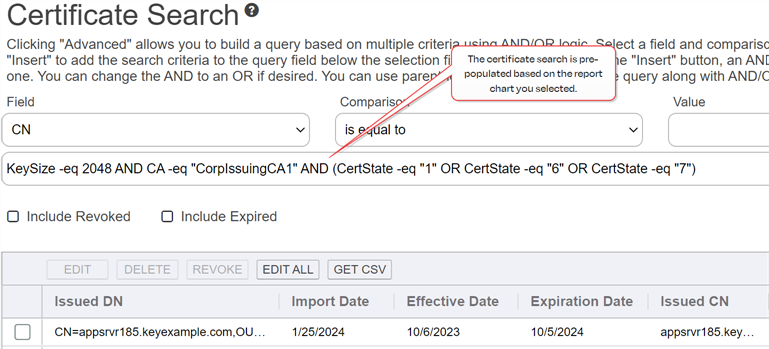
Most reports now have drill-down capability. Clicking on a chart or graph segment in a report will open the corresponding query grid in a new browser window or tab populated with the query as defined by the selected graph segment. For example, for the Certificates by Key Strength report, clicking on a bar or pie will take you to the Certificate Search page pre-populated with the query that corresponds to that bar or pie.
 List of Built-In Reports
List of Built-In Reports
The following reports are available as part of the standard Keyfactor Command installation. Those marked with a (*) have been configured to Show in Navigator by default, so they appear on the Management Portal top menu under Reports. The Report Manager page shows all the available reports.
- Certificate Count by Template
 A certificate template defines the policies and rules that a CA uses when a request for a certificate is received.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. - Certificate Count by User per Template
- Certificate Count Grouped by Single Metadata
 Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. Field
Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. Field - Certificate Issuance Trends with Metadata
- Certificates by Key Strength
- Certificates by Revoker
- Certificates by Type and Java Keystores
- Certificates Found at TLS
 TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers./SSL
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers./SSL TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. Endpoints
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. Endpoints - Certificates in Collection (*)
- Expiration Report (*)
- Expiration Report by days (*)
- Full Certificate Extract (*)
- Issued Certificates per Certificate Authority
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. - Monthly Executive Report
- PKI
 A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. Status for Collection (*)
A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. Status for Collection (*) - Revoked Certificates in Certificate Stores
- SSH
 The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. Key Usage Report
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. Key Usage Report - SSH Keys by Age
- SSH Keys with Root Logon Access
- SSH Trusted Public Keys with No Known Private Keys
- Statistical Report (*)