To select a single row in the certificate store grid, click to highlight it and then select an operation from either the top of the grid or the right-click menu. The delete, schedule inventory and assign container operations can be done on multiple certificate stores at once. To select multiple rows, click the checkbox for each row on which you would like to perform an operation. Then select an operation from the top of the grid. The selected stores must all be of the same category (e.g. PEM![]() A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. or Java) to perform the assign container operation. The right-click menu supports operations on only one store at a time.
A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. or Java) to perform the assign container operation. The right-click menu supports operations on only one store at a time.
 Adding or Modifying a Certificate Store
Adding or Modifying a Certificate Store
Before creating a certificate store in Keyfactor Command, you must approve an orchestrator![]() Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. to handle the store (see Approving or Disapproving Orchestrators).
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. to handle the store (see Approving or Disapproving Orchestrators).
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
Certificate stores can be added manually or, for some types of stores, automatically using a discover process (see Certificate Store Discovery).
To define a new certificate store location manually or edit an existing one:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, click Add to create a new store location, or click Edit from either the top or right-click menu to modify an existing one.
-
In the Certificate Stores dialog, select the type of certificate store in the Category dropdown. The values that appear here are the display names for the built-in certificate store types and any custom certificate store types you entered to match your custom extensions. Examples of Keyfactor-provided custom-built extensions on GitHub include:
-
Remote File Certificate Store Management (Java Keystores, PKCS12 files, PEM files, DER
 A DER format certificate file is a DER-encoded binary certificate. It contains a single certificate and does not support storage of private keys. It sometimes has an extension of .der but is often seen with .cer or .crt. files, IBM Key Database files)
A DER format certificate file is a DER-encoded binary certificate. It contains a single certificate and does not support storage of private keys. It sometimes has an extension of .der but is often seen with .cer or .crt. files, IBM Key Database files)
Note: This field cannot be modified on an edit.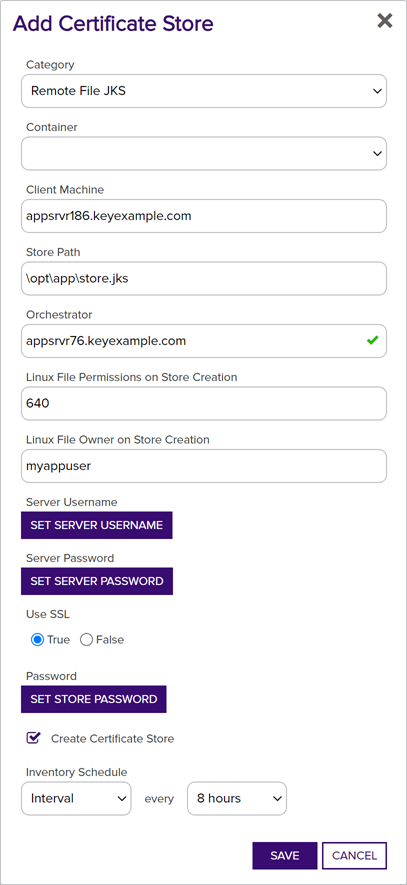
Figure 237: Add a Remote JKS Certificate Store
-
In the Container field, select a container into which to place the store for organization from your previously defined list, if desired. This field is optional. If no container matching the type of certificate store you are adding exists, no containers will be available in the dropdown (see Certificate Store Container Operations). Leave blank if you do not wish the certificate store to be associated with a specific store container.
-
The remaining fields on the dialog will vary depending on the configuration of your custom certificate store type. Common fields include:
-
Client Machine
Typically the fully qualified domain name or IP address of the target server or device on which the certificate store is located.
Important: In some cases, it’s necessary to use the actual hostname The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). of the target server in the Client Machine field rather than a DNS
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). of the target server in the Client Machine field rather than a DNS The Domain Name System is a service that translates names into IP addresses. alias (either “A” or CNAME records). This is necessary when the orchestrator uses PowerShell remoting (WinRM) for some of the machine certificate store functions, which relies on Kerberos authentication. Kerberos authentication requires that the target machine has a service principal name (SPN) in the HTTP/ format assigned to the target’s machine account. This will be present by default (as part of the HOST/ format record) as long as the HTTP/ format SPN has not been manually assigned elsewhere. Using an alias gets into complexities of setting up appropriate SPNs and assuring that there are not duplicate SPNs in the environment. If you wish to manage the target server hosting Keyfactor Command, you will need to use a DNS alias for either your Keyfactor Command server or the IIS store access. Contact Keyfactor for design assistance.Note: This field cannot be modified on an edit.
The Domain Name System is a service that translates names into IP addresses. alias (either “A” or CNAME records). This is necessary when the orchestrator uses PowerShell remoting (WinRM) for some of the machine certificate store functions, which relies on Kerberos authentication. Kerberos authentication requires that the target machine has a service principal name (SPN) in the HTTP/ format assigned to the target’s machine account. This will be present by default (as part of the HOST/ format record) as long as the HTTP/ format SPN has not been manually assigned elsewhere. Using an alias gets into complexities of setting up appropriate SPNs and assuring that there are not duplicate SPNs in the environment. If you wish to manage the target server hosting Keyfactor Command, you will need to use a DNS alias for either your Keyfactor Command server or the IIS store access. Contact Keyfactor for design assistance.Note: This field cannot be modified on an edit. -
Store Path
The path to the certificate store, sometimes including the store file name, on the target server or device.
For Java keystores, for example, this would be a file system path and file name (e.g. /opt/app/mystore.jks or C:\My App\mystore.jks). Paths and filenames entered for Linux/UNIX machines are case sensitive.
For CA
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. bundles on F5 devices, this is the bundle into which you want to install the certificate (e.g. /Common/myca-bundle). The Store Path name is case sensitive for some targets and devices, so, for example, if the partition name on the F5 is Common it must be entered in the Store Path field as Common rather than common.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. bundles on F5 devices, this is the bundle into which you want to install the certificate (e.g. /Common/myca-bundle). The Store Path name is case sensitive for some targets and devices, so, for example, if the partition name on the F5 is Common it must be entered in the Store Path field as Common rather than common.For IIS bound certificate stores, this is the name of the Windows certificate store (My = Local Computer Personal store, Web Hosting = Local Computer Web Hosting store).
Check the details of the documentation for your custom-built extension to determine the data to enter here.
Note: This field cannot be modified on an edit. -
Orchestrator
The name that the Keyfactor Universal Orchestrator
 The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers. used when registering with Keyfactor Command. The orchestrator must be approved in order to appear here (see Approving or Disapproving Orchestrators).
The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers. used when registering with Keyfactor Command. The orchestrator must be approved in order to appear here (see Approving or Disapproving Orchestrators). -
Server Username
The source from which to load a user valid on the target server or device with sufficient permissions to read the store location and open the file(s) and the name of that user, if applicable. In the Server Username dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for server authentication.
Load From PAM Provider. The No Value option is typically not supported for server authentication.For F5, this as a user with Administrator permissions. Although a user with Resource Administrator permissions is sufficient when using the F5 methods that use the SOAP API
 A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command., the F5 methods that use the REST API require full Administrator permissions.
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command., the F5 methods that use the REST API require full Administrator permissions.For AWS using IAM authentication, this is the API access key for your web service.
This field only appears if your custom certificate store type indicates that it Needs Server.
-
Server Password
The source from which to load a valid password for the user used to access the server and the password for that user, if applicable. In the Server Password dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for server authentication.
Load From PAM Provider. The No Value option is typically not supported for server authentication.This field only appears if your custom certificate store type indicates that it Needs Server.
-
Use SSL
Use SSL
 TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. to communicate to the remote target or device.
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. to communicate to the remote target or device.If the remote target is an F5 device and you’re using the F5 extension, the device must trust the CA that issued the certificate used to protect the Keyfactor Command server or you must set the Ignore Server SSL Warnings application setting to True (see Application Settings: Agents Tab).
If the remote target is a Windows server and you’re using the Remote File or IIS extension, WinRM on the target must be configured to support HTTPS and have been configured with an SSL certificate (see Configure Windows Targets for Remote Management).
This field only appears if your custom certificate store type has been configured with the Use SSL custom field. Your field name may vary depending on the configuration of your custom certificate store type.
-
Create Certificate Store
If this box is checked, a new certificate store will be created on the target with the specified configuration. This option only appears if your custom certificate store type has been configured with Create for Supported Job Types.
-
Store Password.
The source from which to load a valid password for the certificate store itself rather than the server as a whole. In the Store Password dialog, the options are
 No Value,
No Value,  Load From Keyfactor Secrets, and
Load From Keyfactor Secrets, and  Load From PAM Provider.
Load From PAM Provider. -
Type
For Java keystores using the Keyfactor Java Agent
 The Java Agent, one of Keyfactor's suite of orchestrators, is used to perform discovery of Java keystores and PEM certificate stores, to inventory discovered stores, and to push certificates out to stores as needed., select the Type from the dropdown. The available types are:
The Java Agent, one of Keyfactor's suite of orchestrators, is used to perform discovery of Java keystores and PEM certificate stores, to inventory discovered stores, and to push certificates out to stores as needed., select the Type from the dropdown. The available types are:-
Standard Java keystore.
-
PKCS12
PKCS12 type files (e.g. P12
 A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. or PFX
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. or PFX A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers.), which are discoverable with the Keyfactor Java Agent using compatibility mode introduced in Java version 1.8.
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers.), which are discoverable with the Keyfactor Java Agent using compatibility mode introduced in Java version 1.8. -
Windows-My
Windows local machine personal certificate store. This option is only supported with a custom extension based on the AnyAgent
 The AnyAgent, one of Keyfactor's suite of orchestrators, is used to allow management of certificates regardless of source or location by allowing customers to implement custom agent functionality via an API. framework. The Keyfactor Java Agent does not include functionality to manage this type of store.
The AnyAgent, one of Keyfactor's suite of orchestrators, is used to allow management of certificates regardless of source or location by allowing customers to implement custom agent functionality via an API. framework. The Keyfactor Java Agent does not include functionality to manage this type of store.
-
The dialog may present additional fields depending on the configuration of the Custom Fields for the certificate store type. Some additional fields that you may find for common Keyfactor custom-built extensions include:
-
For F5 certificates stores, in the Primary Node field, enter the fully qualified domain name of the F5 device that acts as the primary node in a highly available F5 implementation. If you're using a single F5 device, this will often be the same value you entered in the Client Machine field.
Tip: Configuration of the primary node is necessary to allow management jobs that update certificates on the F5 device to wait until the primary node is available before making their update. Inventory jobs are carried out against any available node. - For F5 certificates stores, in the Primary Node Check Retry Wait Seconds field, either accept the default value of 120 seconds or enter a new value. This value represents the number of seconds the orchestrator will wait after a pending management job cannot be completed because the primary node cannot be contacted before trying to contact the primary node again to retry the job.
- For F5 certificates stores, in the Primary Node Check Retry Maximum field, either accept the default value of 3 retry attempts or enter a new value. This value represents the number of times the orchestrator will retry a pending management job that is failing because the primary node cannot be contacted before declaring the job failed.
-
For F5 certificates stores, in the Version of F5 dropdown, select the version of F5 this server is running. The F5 REST API is supported on version 13 and up.
Tip: Select v15 for version 15 and above. -
For IIS bound and Windows certificate stores, in the WinRm Protocol field, select http to communicate between the orchestrator and the target over a non-secured WinRM channel or https to communicate over a secured channel WinRM channel. Using HTTPS for WinRM requires that the target has been configured to support HTTPS and has been configured with an SSL certificate for WinRM. For example:
-
For IIS bound and Windows certificate stores, in the WinRm Port field, accept the default of port 5986 for HTTPS, enter port 5985 for the default HTTP WinRM port, or enter an alternate port if your WinRM configuration is using an alternate port.
-
For IIS bound and Windows certificate stores, in the SPN with Port field, accept the default of false unless you’re aware that the -IncludePortwithSPN switch is required for remote PowerShell connections in your environment.
-
For Java keystores, PEM stores, and PKCS12 stores on Linux targets when creating a new certificate store (see Create Certificate Store) using the Remote File extension, in the Linux File Permissions on Store Creation field, set the file permissions that should be granted to the new certificate store given in numeric format (e.g. 644). The default is 600.
-
For Java keystores, PEM stores, and PKCS12 stores on Linux targets when creating a new certificate store (see Create Certificate Store) using the Remote File extension, in the Linux File Owner on Store Creation field, set the file ownership that should be granted to the new certificate store given as a Linux username. The default is the user configured to authenticate to the server (see Server Username).
- For PEM stores, in the Separate Private Key File Location field, enter the full path to the private key
 Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. on the machine, including the file name. Paths and filenames entered for Linux/UNIX machines are case sensitive.
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. on the machine, including the file name. Paths and filenames entered for Linux/UNIX machines are case sensitive. - For PEM stores using the Remote File extension, in the Trust Store field, a value of True indicates the target store is a trust store and as such should only contain public keys. If a store is marked as a trust store and a job is run that attempts to add a private key for a certificate to the store, an error will occur indicating a problem. A value of False indicates the store can contain a single certificate with private key and chain. The default is False.
- For PEM stores using the Remote File extension, in the Store Includes Chain field, a value of True causes the full chain for the certificate to be delivered to the store. A value of False indicates that only the certificate and private key should be delivered to the store. The certificates are always placed in the store in the order of : End Entity, Issuing CA, Root CA. The default is False. The field is ignored if Trust Store is True.
- For PEM stores using the Remote File extension, in the Is RSA Private Key field, a value of True indicates the private key for the certificate store is a PKCS#1 RSA formatted key (it will be headed with a line that reads “BEGIN RSA PRIVATE KEY”). A value of False indicates the private key for the certificate store is either an encrypted or non-encrypted PKCS#8 formatted key (it will be headed with a line that reads either “BEGIN PRIVATE KEY” or “BEGIN ENCRYPTED PRIVATE KEY”). If set to True, the Store Password must be set to No Value. The default is False. The field is ignored if Trust Store is True.
-
- In the Inventory Schedule fields, select an inventory schedule for the store, if desired. You can choose to run the inventory Daily, on an Interval, Immediately, Exactly Once, or set inventorying to Off.
- If you select Daily, you can set the time of day when the inventory should begin every day.
- If you select Interval, you can select a scan frequency of anywhere from every 1 minute to every 12 hours.
- If you select Immediate, the inventory will run within a few minutes of saving the record and will run only once. After this, the inventory schedule will be cleared.
- If you select Exactly Once, you can select a date and time at which to run the inventory job. After the job has run, the inventory schedule will be cleared.
- Select Off to disable the inventory job.
If you are using Certificate Store Containers (see Certificate Store Containers) to manage your stores and their schedules you do not need to set an inventory schedule here.
- Click Save to save the new or edited certificate store location.
 Deleting a Certificate Store
Deleting a Certificate Store
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
To delete a certificate store:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row(s) in the certificate store grid of the store(s) to delete and click Delete at the top of the grid or right-click the store location in the grid and choose Delete from the right-click menu. The right-click menu supports operations on only one store at a time.
- On the Confirm Operation alert, click OK to confirm or Cancel to cancel the operation.
 Viewing a Certificate Store
Viewing a Certificate Store
Users without modify permissions to certificate stores will see a View option instead of an Edit option on the Certificate Stores page to allow them to see a read-only view of the certificate store configuration details.
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
To view the details of a certificate store:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row in the certificate store grid of the store for which to view certificate store details and click View at the top of the grid or right-click the store location in the grid and choose View from the right-click menu.
The fields are the same as those described for adding or editing a certificate store (see Adding or Modifying a Certificate Store), but none of the fields are editable when using the View option.
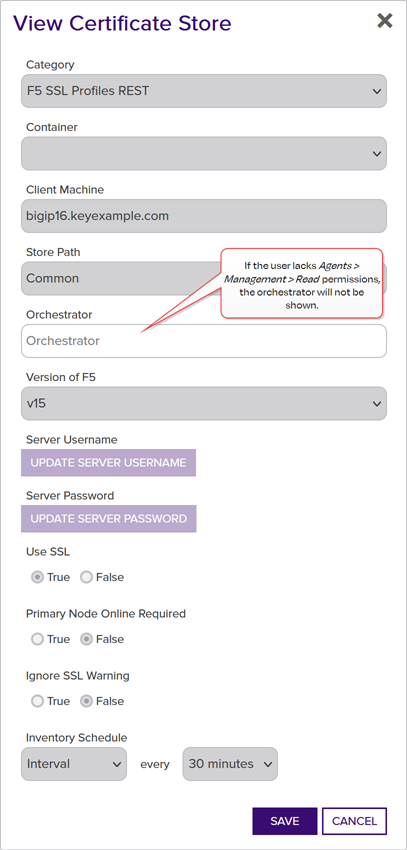
Figure 239: View Details for a Certificate Store
 Certificate Store Reenrollment
Certificate Store Reenrollment
The Reenrollment option is available for select built-in and custom-built extensions provided by Keyfactor on GitHub or can be included in your fully custom extension. Examples of built-in and Keyfactor custom-built extensions that support reenrollment include:
-
Akamai Certificate Provisioning System (CPS) on GitHub for use with the Keyfactor Universal Orchestrator
-
IIS Certificate Store Manager on GitHub for use with the Keyfactor Universal Orchestrator
-
PEM and Java certificate stores managed by the Keyfactor Java Agent.
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
In addition, either the user scheduling the reenrollment job or the user configured to provide authentication to the CA (see Authorization Methods Tab) must have enrollment![]() Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). permissions configured on the CA and template
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). permissions configured on the CA and template![]() A certificate template defines the policies and rules that a CA uses when a request for a certificate is received..
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received..
To begin a reenrollment:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row in the certificate store grid of the store to reenroll and click Reenrollment at the top of the grid or right-click the store location in the grid and choose Reenrollment from the right-click menu.
- On the Reenrollment dialog, enter a Subject Name for the new certificate using X.500 format and populate any additional fields as required by the certificate store type (on the Entry Parameters tab; see Adding or Editing a Certificate Store Type).
-
If desired, select a Certificate Authority to direct the enrollment request to and/or Template for the request. In the Template dropdown, only templates that are available for enrollment from the selected certificate authority
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. will appear.Note: If you don't select a template or CA for reenrollment, the values configured for the Template For Submitted CSRs and/or Certificate Authority For Submitted CSRs application setting(s) (see Application Settings: Agents Tab) will be used.Tip: If an expected template does not appear in the Template dropdown, confirm that it is available for enrollment from the selected CA, has been configured for CSR
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. will appear.Note: If you don't select a template or CA for reenrollment, the values configured for the Template For Submitted CSRs and/or Certificate Authority For Submitted CSRs application setting(s) (see Application Settings: Agents Tab) will be used.Tip: If an expected template does not appear in the Template dropdown, confirm that it is available for enrollment from the selected CA, has been configured for CSR A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment in Keyfactor Command, and has appropriate enrollment permissions at the Keyfactor Command, CA and template level for the user making the reenrollment request or relevant service account depending on the authorization method for enrollment (see Grant the Keyfactor Command Users and Service Account(s) Permissions on the CAs in the Keyfactor Command Server Installation Guide).
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment in Keyfactor Command, and has appropriate enrollment permissions at the Keyfactor Command, CA and template level for the user making the reenrollment request or relevant service account depending on the authorization method for enrollment (see Grant the Keyfactor Command Users and Service Account(s) Permissions on the CAs in the Keyfactor Command Server Installation Guide). - Click Done to submit the request.
The reenrollment job will be scheduled to run immediately. Visit the Orchestrator Jobs page to check on the progress of the job (see Orchestrator Job Status).
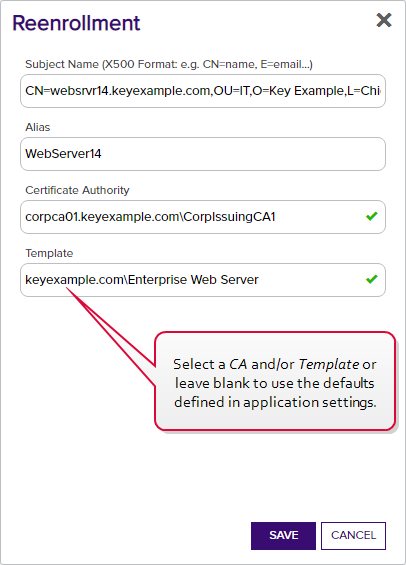
Figure 240: Enter a Information for Reenrollment
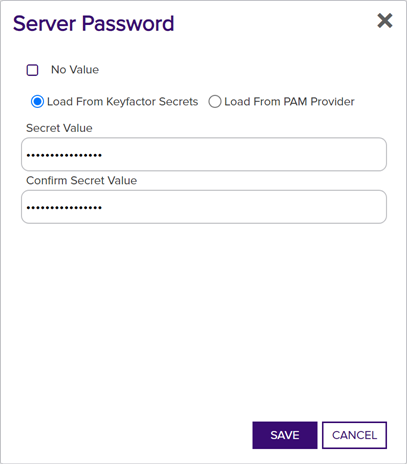
 Setting a New Password on a Certificate Store
Setting a New Password on a Certificate Store
The option to reset the password on a certificate store updates the data for the certificate store as stored in the Keyfactor Command database but does not make any modifications to the certificate store itself. This option is available from the right-click menu only.
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
To reset the password for a certificate store:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row in the certificate store grid of the store to update and choose Set New Password from the right-click menu.
- Enter and confirm the new password and click Save.
 Assigning a Certificate Store to a Container
Assigning a Certificate Store to a Container
Before assigning a certificate store to a container, you need to create the container (see Certificate Store Containers). If you select multiple certificate stores to assign to a container at once, they must all be stores of the same type (e.g. PEM).
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
To assign a certificate store to a container:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row(s) in the certificate store grid of the store(s) to be assigned to the container and click Assign Container at the top of the grid or right-click the store location in the grid and choose Assign Container from the right-click menu. The right-click menu supports operations on only one store at a time.
- Select a certificate store container in the Container Name field and click Save.
 Viewing Inventory for a Certificate Store
Viewing Inventory for a Certificate Store
Once at least one inventory job has been completed for a given certificate store, you can view the certificates imported from the store.
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
To view the inventoried certificates for a store:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row in the certificate store grid of the store for which to view inventory and click View Inventory at the top of the grid or right-click the store location in the grid and choose View Inventory from the right-click menu.
On the left of the inventory viewing dialog you can select a certificate from the store to view. On the right of the dialog you can see details about that certificate, including the metadata![]() Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. associated with the certificate. In the Certificate Selection area of the screen, you can select between the chain certificates for the selected certificate and the end entity certificate, for certificates stored with a chain.
Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. associated with the certificate. In the Certificate Selection area of the screen, you can select between the chain certificates for the selected certificate and the end entity certificate, for certificates stored with a chain.
At the bottom of the inventory viewing dialog, click Query Certificate, after selecting the certificate to view, to open a new browser tab to the certificate search page with the search criteria specifying only the certificate you selected. The Revoked and Expired check boxes will automatically be included if either condition is true for that certificate.
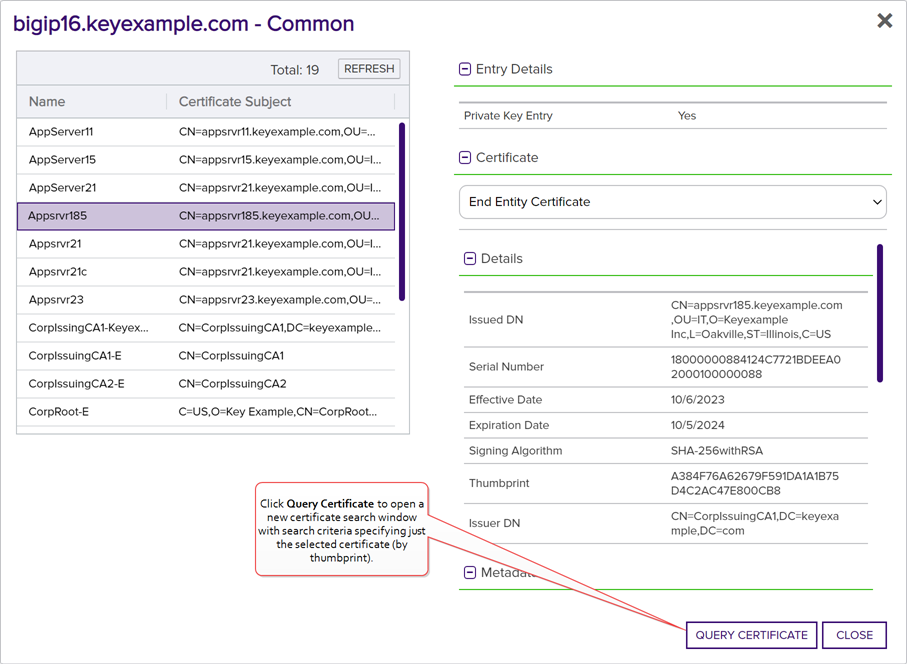
Figure 241: View Inventoried Certificates for a Certificate Store
 Scheduling Inventory for a Certificate Store
Scheduling Inventory for a Certificate Store
Scheduling inventory for a certificate store allows Keyfactor Command to inspect the certificates inside a given store and add them to the Keyfactor Command database.
Permissions for certificate stores can be set at either the global or certificate store container level. See Container Permissions for more information about global vs container permissions.
To schedule inventory:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row(s) in the certificate store grid of the store(s) for which you want to schedule inventory and click Schedule Inventory at the top of the grid, or choose Schedule Inventory from the right-click menu. The right-click menu supports operations on only one store at a time.
- In the Certificate Store Inventory Schedule dialog, select a schedule for the store(s). You can choose to run the inventory Daily, on an Interval, Immediately, Exactly Once, or set inventorying to Off.
- If you select Daily, you can set the time of day when the inventory should begin every day.
- If you select Interval, you can select a scan frequency of anywhere from every 1 minute to every 12 hours.
- If you select Immediate, the inventory will run within a few minutes of saving the record and will run only once. After this, the inventory schedule will be cleared.
- If you select Exactly Once, you can select a date and time at which to run the inventory job. After the job has run, the inventory schedule will be cleared.
- Select Off to disable the inventory job.
You have the option to not schedule inventory on a store-by-store basis and instead create containers and set inventory schedules that will apply to all the stores added to each container. See Certificate Store Containers for information on creating containers.
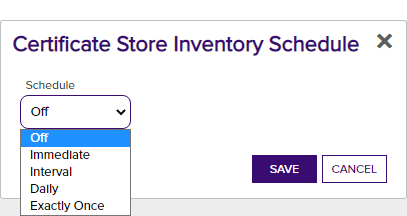
Figure 242: Schedule Inventory for a Certificate Store Location
 Querying Certificates for a Certificate Store
Querying Certificates for a Certificate Store
The Query Certificate Store option allows you to open a new browser tab with an instance of the Management Portal open to the certificate search page pre-populated with search criteria to locate the certificates found in that certificate store.
Permissions for certificates and certificate stores can be set at either the global or certificate collection![]() The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports). and certificate store container level. You can use a mixture with, for example, global certificate permissions and container-level certificate store permissions. See Certificate Collection Permissions and Container Permissions for more information about global vs collection and container permissions.
The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports). and certificate store container level. You can use a mixture with, for example, global certificate permissions and container-level certificate store permissions. See Certificate Collection Permissions and Container Permissions for more information about global vs collection and container permissions.
To use the query certificate store option:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Certificate Stores tab (the default when you first visit the page).
- On the Certificate Stores tab, highlight the row in the certificate store grid of the store for which you want to query certificates and click Query Certificate Store at the top of the grid, or choose Query Certificate Store from the right-click menu.