The Certificate Signing Request![]() A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. (CSR
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. (CSR![]() A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA.) generation page provides the ability to enter a subject, SAN
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA.) generation page provides the ability to enter a subject, SAN![]() The subject alternative name (SAN) is an extension to the X.509 specification that allows you to specify additional values when enrolling for a digital certificate. A variety of SAN formats are supported, with DNS name being the most common., key size
The subject alternative name (SAN) is an extension to the X.509 specification that allows you to specify additional values when enrolling for a digital certificate. A variety of SAN formats are supported, with DNS name being the most common., key size![]() The key size or key length is the number of bits in a key used by a cryptographic algorithm., and template
The key size or key length is the number of bits in a key used by a cryptographic algorithm., and template![]() A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. information and generate a CSR based on this information. You can then use this CSR to request a certificate using the CSR enrollment
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. information and generate a CSR based on this information. You can then use this CSR to request a certificate using the CSR enrollment![]() Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). function (see CSR Enrollment) or any other enrollment method requiring a CSR.
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). function (see CSR Enrollment) or any other enrollment method requiring a CSR.
When you use the CSR generation option, the encrypted private key![]() Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. of the request is stored in the Keyfactor Command database. When you generate a certificate using that CSR, it will be married together with the private key when the certificate synchronizes into the Keyfactor Command database. The certificate enrollment with the CSR does not need to be completed in Keyfactor Command (using CSR Enrollment) in order for the private key to be married with the certificate. Certificates enrolled outside of Keyfactor Command using CSRs generated within Keyfactor Command and synchronized via the CA
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. of the request is stored in the Keyfactor Command database. When you generate a certificate using that CSR, it will be married together with the private key when the certificate synchronizes into the Keyfactor Command database. The certificate enrollment with the CSR does not need to be completed in Keyfactor Command (using CSR Enrollment) in order for the private key to be married with the certificate. Certificates enrolled outside of Keyfactor Command using CSRs generated within Keyfactor Command and synchronized via the CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. synchronization process (see Certificate Authorities) or manually imported using the Add Certificate option (see Add Certificate) will also be married with their private keys.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. synchronization process (see Certificate Authorities) or manually imported using the Add Certificate option (see Add Certificate) will also be married with their private keys.
To generate a CSR:
- In the Keyfactor Command Management Portal, browse to Enrollment > CSR Generation.
-
In the Certificate Request Details section of the page:
-
Select a Template, if desired. The templates are organized by configuration tenant
 A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. (formerly known as forest
A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. (formerly known as forest An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers.). If you have multiple configuration tenants and templates with similar names, be sure to select the template in the correct configuration tenant.Important: The template will not be included in the CSR. The template is referenced in order to retrieve key and other information to help populate the CSR. In addition, the CSR generation function supports template-level regular expressions for both subject parts and SANs. If system-wide and template-level regular expressions exists for the same field and you select a template, the template-level regular expression is applied.
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers.). If you have multiple configuration tenants and templates with similar names, be sure to select the template in the correct configuration tenant.Important: The template will not be included in the CSR. The template is referenced in order to retrieve key and other information to help populate the CSR. In addition, the CSR generation function supports template-level regular expressions for both subject parts and SANs. If system-wide and template-level regular expressions exists for the same field and you select a template, the template-level regular expression is applied.If you choose to select a template during CSR generation, you will need to choose the same template during CSR Enrollment, because the CSR file will contain elements from the template which may conflict with other template configurations.
-
Select a Key Algorithm and Key Size for your CSR. If you have selected a template, these dropdowns will be limited to the values supplied by the template. If the template supplies only one value for key algorithm and/or size, these dropdowns will be grayed out. When enrolling with the template, the key size of the request is validated against the template key size.
Note: The supported key algorithms for a certificate template are determined based on global template policy, individual template policy, and the template's supported algorithm.When configuring template-level policies for key information, only key sizes that are valid for the algorithm will be available, according to the global template policy, the template policy, and the supported key sizes. For PFX
 A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. and CSR generation, you will be offered the option to select the Key Algorithm and Key Size for the enrollment in dropdowns if the selected template with applied policy settings supports more than one of these. If, after applying Keyfactor Command policy to the returned template there is only one value for key algorithm and size, these dropdowns will be grayed out. If for some reason an algorithm comes back as supported, but no key sizes are available, that algorithm should not appear. When selecting an ECC
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. and CSR generation, you will be offered the option to select the Key Algorithm and Key Size for the enrollment in dropdowns if the selected template with applied policy settings supports more than one of these. If, after applying Keyfactor Command policy to the returned template there is only one value for key algorithm and size, these dropdowns will be grayed out. If for some reason an algorithm comes back as supported, but no key sizes are available, that algorithm should not appear. When selecting an ECC Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller, and more efficient cryptographic keys. ECC generates keys through the properties of the elliptic curve equation instead of the traditional method of generation as the product of very large prime numbers. key size, the curve for that key size will be displayed.
Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller, and more efficient cryptographic keys. ECC generates keys through the properties of the elliptic curve equation instead of the traditional method of generation as the product of very large prime numbers. key size, the curve for that key size will be displayed.
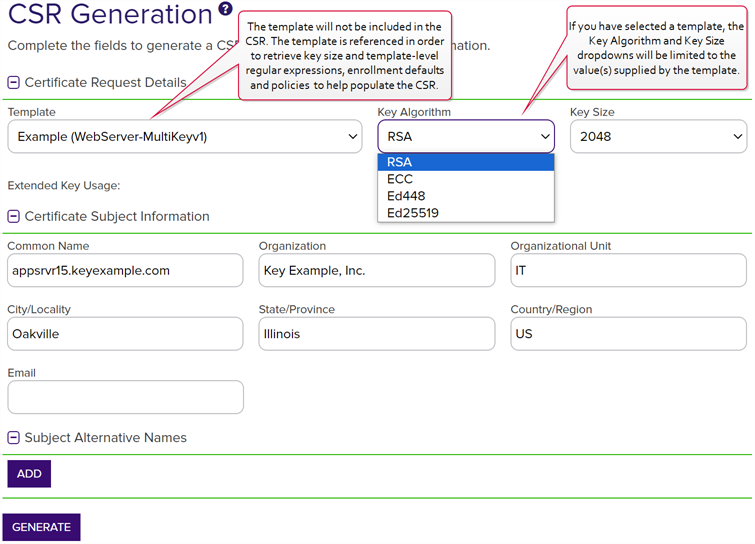
Figure 100: CSR Generation
-
-
In the Certificate Subject Information section of the page, enter appropriate subject information for your CSR.
Note: Some subject fields may be automatically populated by system-wide or template-level enrollment defaults. You may override the system-populated data, if desired. Any system-wide or template-level regular expressions will be used to validate the data entered in the subject fields. System-wide or template-level policies will affect the request. For more information, see Certificate Template Operations. Subject data may also be overridden after an enrollment request is submitted either as part of a workflow A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked. (see Update Certificate Request Subject\SANs for Microsoft CAs) or using the Subject Format application setting (see Application Settings: Enrollment Tab).
A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked. (see Update Certificate Request Subject\SANs for Microsoft CAs) or using the Subject Format application setting (see Application Settings: Enrollment Tab). -
In the Subject Alternative Names section of the page, click Add and select from the dropdown to enter one or more SANs for your CSR. Use the Remove action button to remove an existing SAN.
Important: If the template you selected has the RFC 2818 compliance setting enabled, the DNS The Domain Name System is a service that translates names into IP addresses. name will be automatically populated with the Common Name
The Domain Name System is a service that translates names into IP addresses. name will be automatically populated with the Common Name A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). (CN
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). (CN A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com).) and will be set to read only.Note: If the CSR generated has multiple SANs, they will not be overridden by the template default settings, nor the RFC 2818 compliance settings.
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com).) and will be set to read only.Note: If the CSR generated has multiple SANs, they will not be overridden by the template default settings, nor the RFC 2818 compliance settings.The SAN field supports:
- DNS name
- P version 4 address
- IP version 6 address
- User Prinicpal Name

Figure 101: CSR Generation SAN Options
-
At the bottom of the page, click the Generate button. You will see a success message. If any template-level or system-wide regexes have been applied to any fields on the CSR and failed you will receive a notice at the top of the CSR generation page indicating the error as defined on the template (whether template or system-wide settings prevail).
Figure 102: CSR Generation Success
- Save or open your CSR once it has been successfully generated.