Keyfactor Command supports using a template![]() A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. SQL connection string that can be created to fit the needs of the overall deployment. This template will be used as a starting point and will not be overwritten by the configuration wizard. For instance, you can set the timeout setting in one place, and once the configuration wizard is run, this is reflected in all places where a connection string is used. The template can be changed at any time to update the connection strings.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. SQL connection string that can be created to fit the needs of the overall deployment. This template will be used as a starting point and will not be overwritten by the configuration wizard. For instance, you can set the timeout setting in one place, and once the configuration wizard is run, this is reflected in all places where a connection string is used. The template can be changed at any time to update the connection strings.
To create a customized connection string, after installing the Keyfactor Command software but before running the configuration wizard, modify both the EFModels and SqlDirect connection strings in the SqlConnectionStrings.json file found in theConfiguration folder under your installation directory. By default, this is:
The settings that can be modified are described in the following Microsoft article:
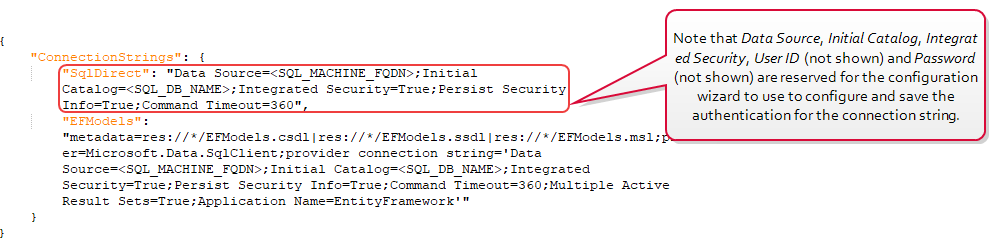
Figure 488: Default SQL Connection Strings
Disable Encryption
If you prefer to connect to your SQL server over a non-encrypted channel (and thus avoid configuring an SSL![]() TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate for your SQL server), you can use the Encrypt keyword in the connection strings with a value of False.
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate for your SQL server), you can use the Encrypt keyword in the connection strings with a value of False.
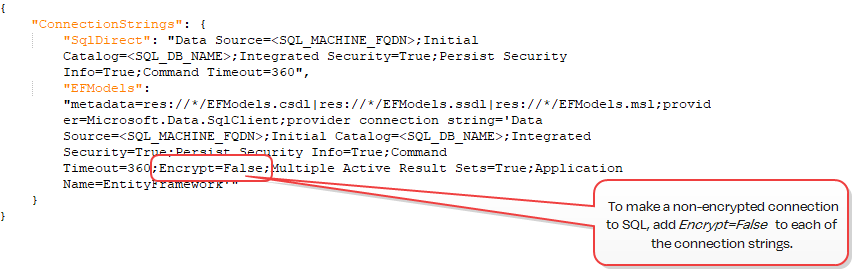
Figure 489: SQL Connection Strings with Encrypt Channel Disabled
Use a SQL Server Listening on Multiple IP Addresses
If you’re using a SQL server cluster that’s configured to listen for incoming connections on more than one IP address to support redundancy or access from multiple networks/subnets, you can use the MultiSubnetFailover keyword in the connection strings with a value of True.
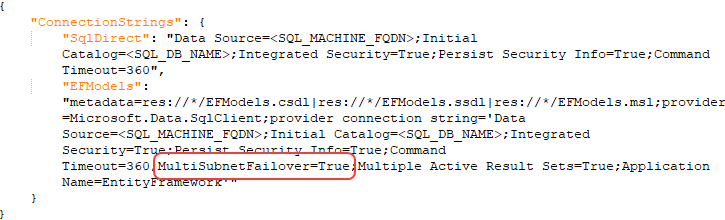
Figure 490: SQL Connection Strings with MultiSubnetFailover Option Enabled