In most cases, if you are installing Keyfactor Command then you have at least one Microsoft or EJBCA Certificate Authority![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. (CA
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. (CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA.) in your environment. As you're planning for Keyfactor Command, you’ll need to make the following decisions and configuration checks for the CA(s) and certificate templates in your environment:
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA.) in your environment. As you're planning for Keyfactor Command, you’ll need to make the following decisions and configuration checks for the CA(s) and certificate templates in your environment:
-
Which CAs should be synchronized to the Keyfactor Command database?
Your license may not allow you to synchronize all of your CAs. Certificates belonging to offline root or policy CA chain certificates can be monitored without impacting your license.
Note: Keyfactor Command contains a constraint that prevents any two certificate authorities from having the same logical name The logical name of a CA is the common name given to the CA at the time it is created. For Microsoft CAs, this name can be seen at the top of the Certificate Authority MMC snap-in. It is part of the FQDN\Logical Name string that is used to refer to CAs when using command-line tools and in some Keyfactor Command configuration settings (e.g. ca2.keyexample.com\Corp Issuing CA Two). and host name
The logical name of a CA is the common name given to the CA at the time it is created. For Microsoft CAs, this name can be seen at the top of the Certificate Authority MMC snap-in. It is part of the FQDN\Logical Name string that is used to refer to CAs when using command-line tools and in some Keyfactor Command configuration settings (e.g. ca2.keyexample.com\Corp Issuing CA Two). and host name The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). combination. Think about the logical name and host name configuration of the CAs that will be implemented with Keyfactor Command and check for duplicates.
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername). combination. Think about the logical name and host name configuration of the CAs that will be implemented with Keyfactor Command and check for duplicates. -
If you have Microsoft CAs, what authorization method will you use to configure the CAs (see Grant the Keyfactor Command Users and Service Account(s) Permissions on the CAs)?
-
If you have EJBCA CAs, are the protocols required for Keyfactor Command connectivity enabled in the EJBCA system configuration? The following protocols must be enabled:
- REST Certificate Management
- REST End Entity Management
- REST End Entity Management V2
- REST Certificate Management V2
-
Web Service
This SOAP API
 A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. protocol is only required if you plan to disable (uncheck) the option to Create new End Entity when renewing or reissuing certificates in the Keyfactor Command certificate authority configuration (see The Basic Tab).
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. protocol is only required if you plan to disable (uncheck) the option to Create new End Entity when renewing or reissuing certificates in the Keyfactor Command certificate authority configuration (see The Basic Tab).
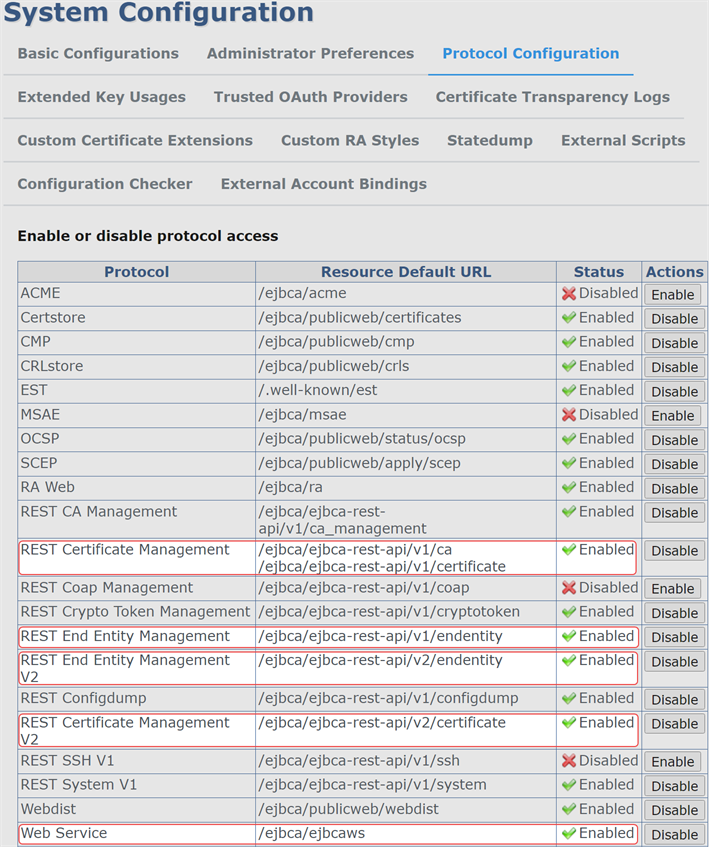
Figure 492: EJBCA Protocols for Keyfactor Command Connectivity
- If your Keyfactor Command license includes certificate enrollment
 Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA).:
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA).:Which CA(s) will be used to issue certificates based on CSRs through the Keyfactor Command Management Portal?
Which CA(s) will be used to issue PFXs through the Keyfactor Command Management Portal?
- Which certificate template
 A certificate template defines the policies and rules that a CA uses when a request for a certificate is received.(s) will be used to generate CSRs through the Keyfactor Command Management Portal? In most cases, these templates will already exist.
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received.(s) will be used to generate CSRs through the Keyfactor Command Management Portal? In most cases, these templates will already exist. Which certificate template(s) will be configured for CSR
 A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment in the Keyfactor Command Management Portal? In most cases, these templates will already exist.
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. enrollment in the Keyfactor Command Management Portal? In most cases, these templates will already exist.Which certificate template(s) will be configured for PFX
 A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. enrollment in the Keyfactor Command Management Portal? In most cases, these templates will already exist.
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. enrollment in the Keyfactor Command Management Portal? In most cases, these templates will already exist.
-
If your Keyfactor Command license includes Mac auto-enrollment, which CA(s) will be used to automatically issue certificates to Macs running the Mac auto-enrollment agent?
As part of the Keyfactor Command installation preparation, you may need to create a certificate template for this purpose.