Keyfactor Command uses data encryption for sensitive data—such as private keys for certificates—stored in the Keyfactor Command database (see SQL Server). This option encrypts only the data in the database deemed to be of a sensitive nature, not the entire database. By default, the data is encrypted using SQL encryption, but you have the option to add another level of security with application-level encryption. If you choose to enable this option, you will need a certificate for this purpose installed in the Personal Certificate store of the Local Computer on each Keyfactor Command server. The certificate must have a key usage of either key encipherment or data encipherment enabled. Microsoft certificate templates only allow you to configure data encipherment (“Allow encryption of user data”) as a suboption to key encipherment (“Allow key exchange only with key encryption”). You do not need to enable both. You may use the certificate acquired in the name of the Keyfactor Command web site (see Acquire a Public Key Certificate for the Keyfactor Command Server), assuming it supports the appropriate key usage, or you may enroll for a separate certificate for this purpose. The same certificate must be used on all Keyfactor Command servers and the certificate must be available in the certificate store on the machine when you run the Keyfactor Command installation. A hardware security module (HSM) may be used, if desired. To support the use of an HSM, the Windows CSP driver for the HSM must be installed on the Keyfactor Command server. Be aware that transactions accessing the encrypted data—such as enrolling for PFX![]() A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. certificates, downloading PFX certificates, running inventory, and adding certificates to certain types of certificate stores (e.g. F5, NetScaler)—will require accessing the HSM. A slow HSM will slow down these processes.
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. certificates, downloading PFX certificates, running inventory, and adding certificates to certain types of certificate stores (e.g. F5, NetScaler)—will require accessing the HSM. A slow HSM will slow down these processes.
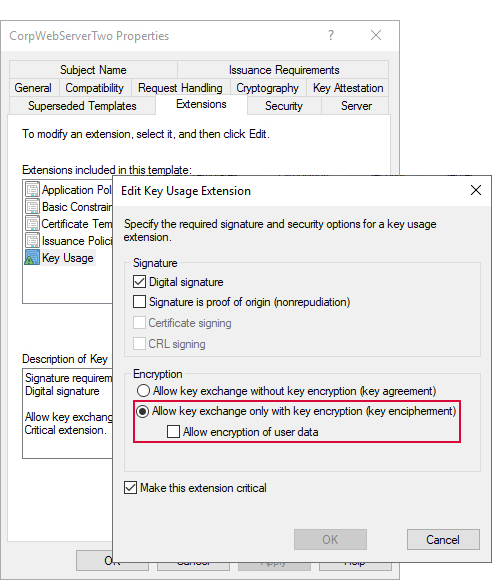
Figure 491: Certificate Template with Key Encipherment Key Usage
Cryptographic Provider
The certificate you use for application-level encryption must be issued using a key storage provider (KSP) or at least installed on the Keyfactor Command server using a KSP in order to allow Keyfactor Command to grant permissions on the certificate’s private key appropriately during installation. If Keyfactor Command is not able to access the private key of the application-level certificate, you may receive a 500.30 error trying to access the Management Portal or you may find you can access the Management Portal but not all features function and you find errors such as these in the log (which of these occurs depends on other configuration factors):
You can check the provider on your certificate with a command similar to the following issued in an administrative command prompt:
Output from this command should like similar to the following for a KSP certificate:
MY "Personal"
================ Certificate 3 ================
Serial Number: 1800000f39f4c506c41239c566000200000f39
Issuer: CN=CorpIssuingCA1, DC=Keyexample, DC=com
NotBefore: 10/27/2023 4:19 PM
NotAfter: 10/26/2025 4:19 PM
Subject: CN=keyfactor.keyexample.com
Non-root Certificate
Template: CorpWebServerv2, Corp Web Server v2
Cert Hash(sha1): 89b5099bc1f7146185331017db60373afb136edb
Key Container = te-CorpWebServerv2-8b4d6ca7-e5ec-472f-a096-8b4aa590b22b
Unique container name: 153703d13e6c7339e297f44547260e6d_00139f2c-9f21-4793-b740-bb3fe658245c
Provider = Microsoft Software Key Storage Provider
Private key is NOT exportable
Encryption test passed
CertUtil: -store command completed successfully.
Output from this command should like similar to the following for a CSP certificate (legacy CSPs vary):
MY "Personal"
================ Certificate 0 ================
Serial Number: 59000006513beacf07ce121e45000100000651
Issuer: CN=CorpIssuingCA1, DC=Keyexample, DC=com
NotBefore: 10/27/2023 4:32 PM
NotAfter: 10/26/2025 4:32 PM
Subject: CN=keyfactor.keyexample.com
Non-root Certificate
Template: CorpWebServer, Corp Web Server
Cert Hash(sha1): a3a1299d3f5d209c89573c356495547b67d92f15
Key Container = d5549bc8ea7af0f51d8b26ffbe9617b8_00139f2c-9f21-4793-b740-bb3fe658245c
Simple container name: te-CorpWebServer-c6c249ac-66d3-427e-aff0-8de81250887f
Provider = Microsoft RSA SChannel Cryptographic Provider
Private key is NOT exportable
Encryption test passed
CertUtil: -store command completed successfully.
If you have a certificate in PFX format with CSP and would like to import it as a KSP, you can use a command similar to the following:
Alternately, if you’re unable to use a certificate with a KSP, you may use a CSP and manually grant the Keyfactor Command application pool user(s) private key read permissions on the certificate (see Using SSL to Connect to SQL Server).