Some packages that may be of special interest to long-term users of Keyfactor Command are:
-
Remote File Certificate Store Management (Java Keystores, PKCS12 files, PEM
 A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. files, DER
A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. files, DER A DER format certificate file is a DER-encoded binary certificate. It contains a single certificate and does not support storage of private keys. It sometimes has an extension of .der but is often seen with .cer or .crt. files, IBM Key Database files)
A DER format certificate file is a DER-encoded binary certificate. It contains a single certificate and does not support storage of private keys. It sometimes has an extension of .der but is often seen with .cer or .crt. files, IBM Key Database files)
To find a package on GitHub:
-
Visit one of the links above to find your desired package, and click either Github Repository or View source on GitHub to go to the package page on GitHub.
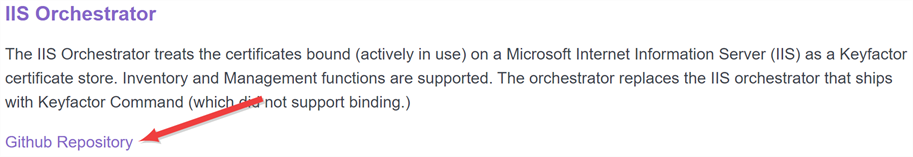
Figure 574: View Packages as Part of a List
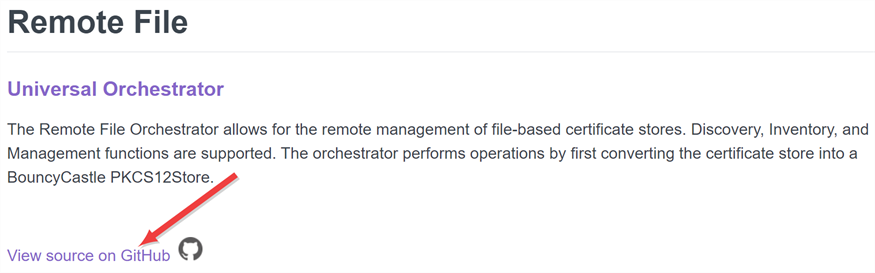
Figure 575: View Packages on Individual Pages
-
On the GitHub page, on the right-hand side, click the link for the Latest version.
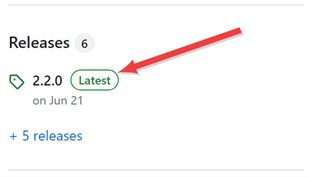
Figure 576: Find the Latest Version of the Package
-
On the GitHub version page in the Assets section, click the package name to download the zip file.
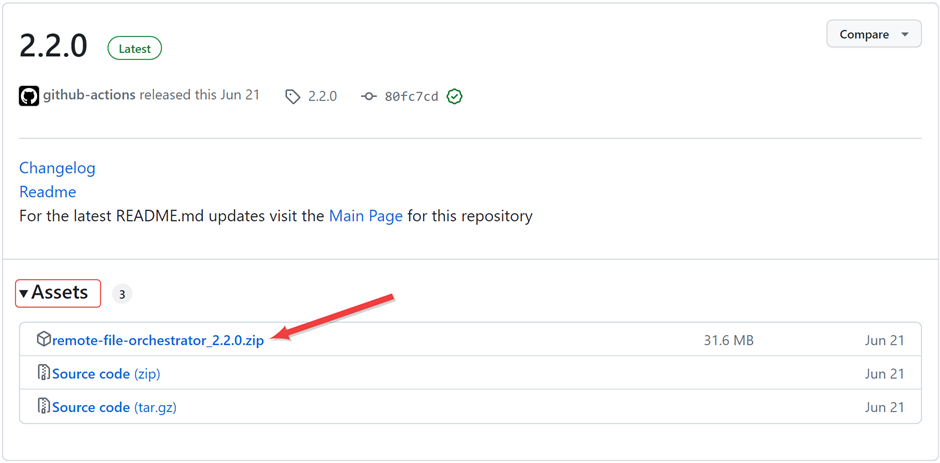
Figure 577: Download the Package Zip File
- On the main extension GitHub page, review the documentation for the specific extension. Here you will find supported platforms, prerequisites, and extension-specific installation and configuration instructions. The below instructions only cover where to place the extension files on the orchestrator and building custom manifest.json files (changes to which aren’t needed for extensions from GitHub unless you are customizing something), but not the details for creation of custom certificate store types for the extension or any other customization specific to a given extension.
Custom-built extensions can also be generated by end users using the Universal Orchestrator NuGet package. Custom-built extensions for certificate store jobs and custom jobs are both installed in the same way.
Once you have your custom-built extension ready, install it as follows:
- In the Keyfactor Command Management Portal or using the Keyfactor API
 A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command., add a certificate store type or custom job type for your custom-built extension, if applicable. See Adding or Editing a Certificate Store Type or POST Custom Job Types
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command., add a certificate store type or custom job type for your custom-built extension, if applicable. See Adding or Editing a Certificate Store Type or POST Custom Job Types -
On the Universal Orchestrator server, locate the extensions directory within the install directory. By default, this is:
Windows: C:\Program Files\Keyfactor\Keyfactor Orchestrator\extensionsLinux: /opt/keyfactor/orchestrator/extensions - Under the extensions directory, create a new directory with an appropriate name for your custom-built extension (e.g. MyExtension). This name is for reference only and does not need to match any names used elsewhere.
- Place the DLL(s) created for your custom-built extension along with any other supporting files needed for the extension in the new directory.
- In the directory for your custom-built extension, create a file called manifest.json if one has not been provided with the extension. The manifest.json file must be placed in the same directory as the DLL(s) for your extension.
-
Using a text editor, edit the manifest.json file if needed and configure it appropriately for your application.
Tip: This step is generally not needed for extensions downloaded from GitHub unless you have opted to make customizations or not use the suggested short name when creating the certificate store type.Some things to keep in mind are:
-
The opening and closing lines of the file must match lines 1-3 and 8-10 here:
Copy{
"extensions": {
"Keyfactor.Orchestrators.Extensions.IOrchestratorJobExtension": {
"Custom.MyJob": {
"assemblypath": "Keyfactor.Orchestrators.MyJob.dll",
"TypeFullName": "Keyfactor.Orchestrators.MyJob.MyJobExtension"
}
}
}
} -
Each customized section of the file starts with either a custom job reference (e.g. Custom.MyJob) or a certificate store reference (e.g. CertStores.MyStore.Inventory).
Custom jobs (beginning Custom) correspond to custom job types created with the Keyfactor API POST /JobTypes/Custom method. For example, a custom job type with a JobTypeName of MyJob would appear in the file as Custom.MyJob.
Certificate store jobs (beginning CertStores) correspond to certificate store types created with the Keyfactor API POST /CertifiateStoreType method (see POST Certificate Store Types) or in the Keyfactor Command Management Portal (see Adding or Editing a Certificate Store Type). For example, a certificate store type with a Capability of MyStore configured to do inventory, management and discovery, would have three separate sections in the file as CertStores.MyStore.Inventory, CertStores.MyStore.Management, and CertStores.MyStore.Discovery. An inventory section is required.
-
The assemblypath referenced in each section points to the DLL in the extensions directory that corresponds to that job function. A single manifest file may include many different capabilities if the extension performs more than one type of job (e.g. inventory and management of certificates), such as is shown in the below example.
-
The TypeFullName referenced in each section corresponds to the name of the type that resides inside of the DLL listed for the assembly path. A single manifest file may include many different capabilities if the extension performs more than one type of job (e.g. inventory and management of certificates), such as is shown in the below example.
-
Each section may optionally have a PreScript reference, which points to a script file on the orchestrator machine that will run before the main job for the section executes.
 Show scripting details.Note: The prescript and postscript functionality of the Keyfactor Universal Orchestrator has been replaced by other functionality in Keyfactor Command such as that provided by Keyfactor Command workflows (see Workflow Definitions). As a result, prescript and postscript functionality has been deprecated and will be removed from a future release.
Show scripting details.Note: The prescript and postscript functionality of the Keyfactor Universal Orchestrator has been replaced by other functionality in Keyfactor Command such as that provided by Keyfactor Command workflows (see Workflow Definitions). As a result, prescript and postscript functionality has been deprecated and will be removed from a future release. -
Each section may optionally have a PostScript reference, which points to a script file on the orchestrator machine that will run after the main job for the section executes. See the notes for script use under PreScript.
-
User-defined certificate store jobs support up to four job types—Inventory, Management, Discovery, and Reenrollment. Each one of these job types should have a separate section in the file.
Copy{
"extensions": {
"Keyfactor.Orchestrators.Extensions.IOrchestratorJobExtension": {
"CertStores.MyStore.Inventory": {
"assemblypath": "Keyfactor.Orchestrators.MyStore.dll",
"TypeFullName": "Keyfactor.Orchestrators.MyStore.MyStoreInventoryJobExtension"
},
"CertStores.MyStore.Management": {
"assemblypath": "Keyfactor.Orchestrators.MyStore.dll",
"TypeFullName": "Keyfactor.Orchestrators.MyStore.MyStoreManagementJobExtension",
"PreScript": "C:\\Program Files\\Keyfactor\\Keyfactor Orchestrator\\extensions\\MyStoreManagementPreScript.ps1",
"PostScript": "C:\\Program Files\\Keyfactor\\Keyfactor Orchestrator\\extensions\\MyStoreManagementPostScript.ps1"
},
"CertStores.MyStore.Discovery": {
"assemblypath": "Keyfactor.Orchestrators.MyStore.dll",
"TypeFullName": "Keyfactor.Orchestrators.MyStore.MyStoreDiscoveryJobExtension"
}
}
}
}
-
- Restart the Universal Orchestrator service (see Start the Universal Orchestrator Service).
- In the Keyfactor Command Management Portal, re-approve the orchestrator. The orchestrator will update to a status of new (if it had been approved previously) upon receiving updated capabilities. See Orchestrator Management for information on approving orchestrators.
Contact your Keyfactor representative for more information about custom-built solutions or to obtain access to the NuGet packages required for development of Universal Orchestrator extensions.