The rotate key option is used to replace an existing key that is approaching the end of its life or has been compromised. If key rotation alerts have been configured in the environment (see Key Rotation Alerts), the administrator responsible for managing the service account key will receive an email when the key is approaching the end if its lifetime to instruct the him or her to rotate the service account key.
The rotate dialog defaults to all the existing settings of the service account's current key. At its simplest, the administrator may choose to accept all the defaults, enter a passphrase to encrypt the downloaded private key and click save to generate the new key pair.
To rotate a service account key pair:
- In the Management Portal, browse to SSH > Service Account Keys.
-
On the Service Account Keys page, click Rotate.
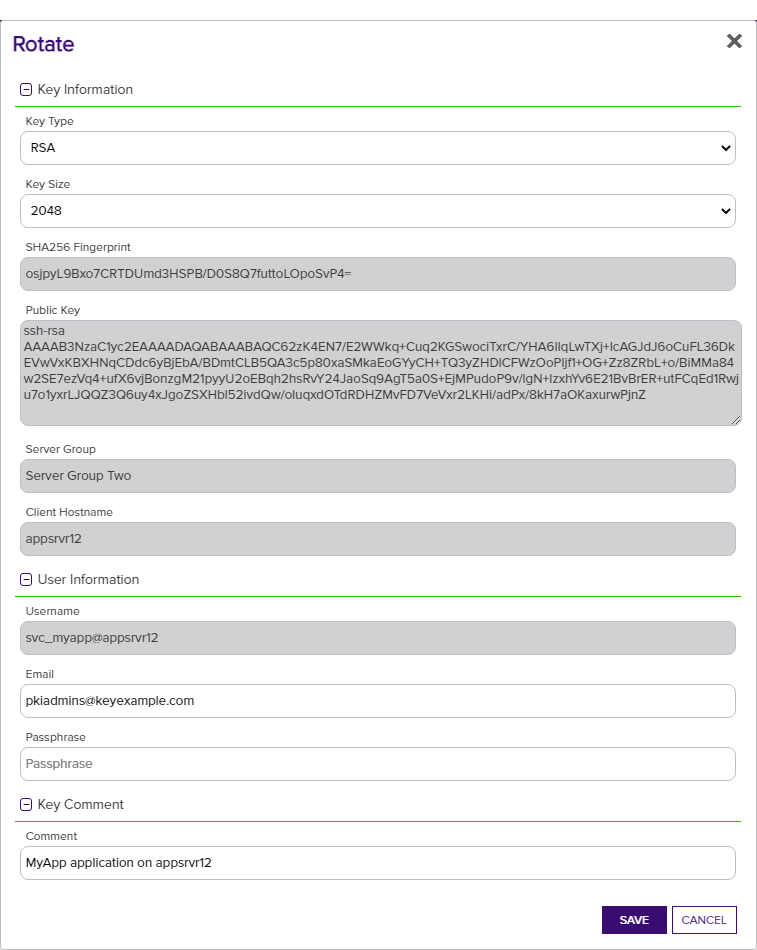
Figure 303: Rotate an SSH Key Pair
- In the Key Information section of the Rotate dialog, modify the existing Key Type in the dropdown, if desired (see Key Type).
- In the Key Information section, modify the existing Key Length in the dropdown, if desired (see Key Length). The available key lengths will vary depending upon the option select in the Key Type dropdown.
- In the User Information section, modify the existing Email address, if desired. This address is used for key rotation alerts (see Key Rotation Alerts). This field is required.
- In the User Information section, enter a Passphrase to encrypt the downloaded copy of the private key of the key pair. You will need to provide this passphrase again when you use the private key to connect via SSH. By default, the minimum password length is 12 characters (see the SSH Key Password setting in Application Settings: SSH Tab). This field is required.
-
In the Key Comment section, modify the existing Comment to include with the key, if desired. This field is optional.
Tip: Although entry of an email address in the comment field of an SSH key is traditional, this is not a required format. The comment may can contain any characters supported for string fields, including spaces and most punctuation marks. - Click Save to create the new key pair.