Key Rotation alert operations include: creating, editing or deleting a key rotation alert, configuring an alert schedule, copying alerts to create similar alerts for different recipients or collections, and testing alerts.
- In the Management Portal, browse to Alerts > Key Rotation.
- On the Key Rotation Alerts page, click Add from the top menu to create a new alert, or Edit ,from either the top or right click menu, to modify an existing one.
-
In the Key Rotation Alert Settings dialog, select a Timeframe for the alert by choosing the number of days, weeks, or months to define the alert period.
Note: When the alert is stored in the database, weeks are converted to 7 days and months are converted to 30 days. -
In the Key Rotation Alert Settings dialog, enter a Display Name for the alert. This name appears in the list of key rotation alerts in the Management Portal.
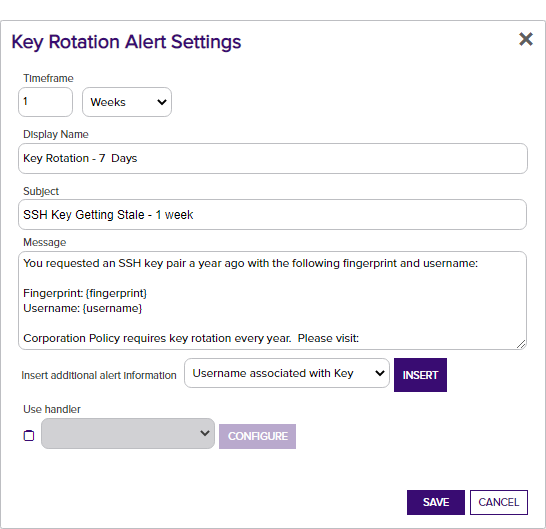
Figure 140: Key Rotation Alerts Recipients
-
In the Subject field, enter a subject line for the email message that will be delivered when the alert is triggered. You can use substitutable special text in the subject line. Substitutable special text uses a variable in the alert definition that is replaced by data from the key record at processing time. For example, you can enter {fingerprint} in the alert definition and each alert generated at processing time will contain the specific fingerprint of the given key instead of the variable {fingerprint}. To add substitutable special text to the subject line, type the special text variable enclosed in curly braces (e.g. {fingerprint}).
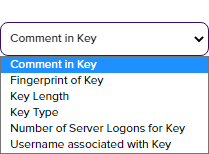
Figure 141: Substitutable Special Text for Key Rotation Alerts
-
In the Message box, enter the body of the email message that will be delivered when the alert is triggered. You can use the Insert special text dropdown below the message window to add substitutable special text to the message. Place your cursor where you would like the text to appear, select the appropriate variable from the dropdown, and click Insert. Alternately, you can type the special text variable enclosed in curly braces directly. If desired, you can format the message body using HTML. For example, you could place the key detail information into a table by replacing this text:
Fingerprint: {fingerprint}Username: {username}Comment: {comment}With this HTML code:
<table><tr><td>Fingerprint:</td><td>{fingerprint}</td></tr><tr><td>Username:</td><td>{username}</td></tr><tr><td>Comment:</td><td>{comment}</td></tr></table> -
Check the Use handler box if you would like the alert to trigger an event handler at processing time, select the appropriate handler in the dropdown, and click the Configure button to configure the event handler. See Event Handler Registration for more information on using event handlers, and Adding PowerShell Handlers to Alerts for more information about using PowerShell Handlers.
- Click Save to save your key rotation alert.
You may use the copy operation to create multiple similar alerts—for example, one for a warning a month in advance of the stale date of keys and another shortly before the keys become stale.
- In the Management Portal, browse to Alerts > Key Rotation.
- On the Key Rotation Alerts page, highlight the row in the alerts grid and click Copy at the top of the grid, or from the right click menu.
- The Key Rotation Alert Settings dialog will pop-up with the details from the selected alert. The display name field will have - Copy tagged to the end of it to indicate it is a new alert. You may modify the alert as needed and click Save to add the new alert, or Cancel to cancel the operation.
- In the Management Portal, browse to Alerts > Key Rotation.
- On the Key Rotation Alerts page, highlight the row in the alerts grid and click Delete at the top of the grid, or from the right click menu.
- On the Confirm Operation alert, click OK to confirm or Cancel to cancel the operation.
After adding your desired key rotation alerts, you may configure a schedule to send the alerts.
- In the Management Portal, browse to Alerts > Key Rotation.
- On the Key Rotation Alerts page, click the Configure button at the top of the Key Rotation Alerts page to configure an alert execution schedule. This defines the frequency with which key rotation alerts are sent. This type of alert is scheduled for daily delivery at a specified time.
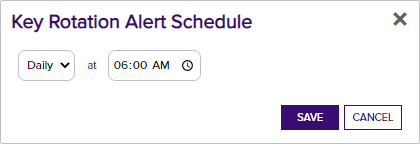
Figure 142: Key Rotation Alert Schedule
Once the alerts are configured, you may run a test of all or selected alerts to see if they are configured correctly.
- In the Management Portal, browse to Alerts > Key Rotation.
- On the Key Rotation Alerts page, either highlight one row in the expiration alert grid and click the Test button at the top of the grid or click the Test All button at the top of the grid to test all the alerts.
- In the Key Rotation Alert Viewer dialog in the Alert Parameters section, select a Start Date and End Date for testing. You can use this option to simulate running the alerts a month from now instead of today, for example, or put in a broad date range to be sure you pick up some expiring certificates for testing purposes.
- In the Key Rotation Alert Viewer dialog in the Alert Parameters section, click the toggle button for Send Alerts if you would like to deliver email messages as part of the test.
- Click the Generate button to begin generating alerts. Depending on the number of keys to process, this may take a few seconds.
- In the Key Rotation Alert Viewer dialog in the Alert Data and Alert Message sections, you can review the keys found to confirm that the expected keys are appearing and that the substitutable special text is being replaced as expected. Scroll through the alerts using the First, Previous, Next and Last buttons at the bottom of the dialog. The number of alerts generated will display between the navigation buttons.
By default, a maximum of 100 alerts will be generated during a test. The maximum value is configurable with the Key Rotation Alert Test Result Limit setting in Keyfactor Command application settings (see Application Settings: Console Tab in the Keyfactor Command Reference Guide). If more than 100 alerts are generated, no email messages will be sent and you'll have the opportunity to view the first 100 alerts generated.
If you're using an event handler, the event handler is run and the handler actions taken (PowerShell script run, event log message written) when the test is run. This is true whether or not you click the Send Alerts toggle.
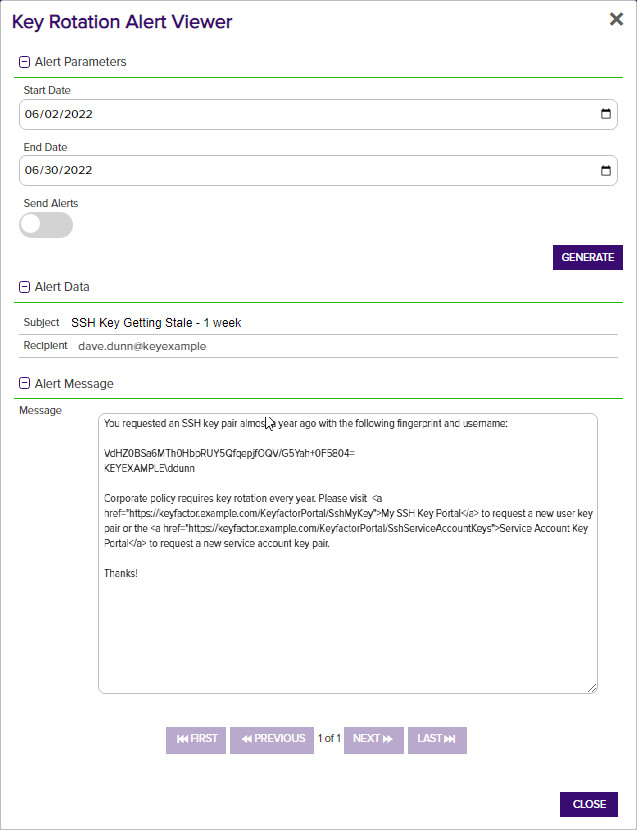
Figure 143: Key Rotation Alert Viewer
Refer to the following table for a complete list of the substitutable special text that can be used to customize alert messages.
Table 10: Substitutable Special Text for Key Rotation Alerts
|
Variable |
Name |
Description |
|---|---|---|
|
{comment} |
Comment in Key |
The user-defined descriptive comment, if any, on the key. Although entry of an email address in the comment field of an SSH key is traditional, this is not a required format. The comment may can contain any characters supported for string fields, including spaces and most punctuation marks. |
|
{fingerprint} |
Fingerprint of Key |
The fingerprint of the public key. Each SSH public key has a single cryptographic fingerprint that can be used to uniquely identify the key. |
|
{keylength} |
Key Length |
The key length for the key. The key length depends on the key type selected. Keyfactor Command supports 256 bits for Ed25519 and ECDSA and 2048 or 4096 bits for RSA. |
|
{keytype} |
Key Type |
A number of cryptographic algorithms can be used to generate SSH keys. Keyfactor Command supports RSA, Ed25519, and ECDSA. RSA keys are more universally supported, and this is the default key type when generating a new key. |
|
{serverlogons} |
Number of Server Logons for Key |
The number of Linux logons associated with the key, if any, granting the holder of the private key pair logon access on the server where the Linux logon resides. |
|
{username} |
Username associated with Key |
The username of the user or service account associated with the key. For a user, the username is in the form of an Active Directory account (e.g. DOMAIN\username). For a service account, the username is made up of the username and client hostname entered when the service account key was created (e.g. myapp@appsrvr75). |