Adding Logons
Before adding a new logon, be sure that you have switched the server to which you will add your logon (or its server group) to inventory and publish policy mode (see Server Manager) so that the new logon will be published to the server. If the server is in inventory only mode and you add a new logon for it in Keyfactor Command, the logon will appear in Keyfactor Command only and will not be published out to the server.
To add a new logon:
- In the Management Portal, browse to SSH > Server Manager.
- On the Server Manager page, select the Logons tab.
-
On the Logons tab, click Add.
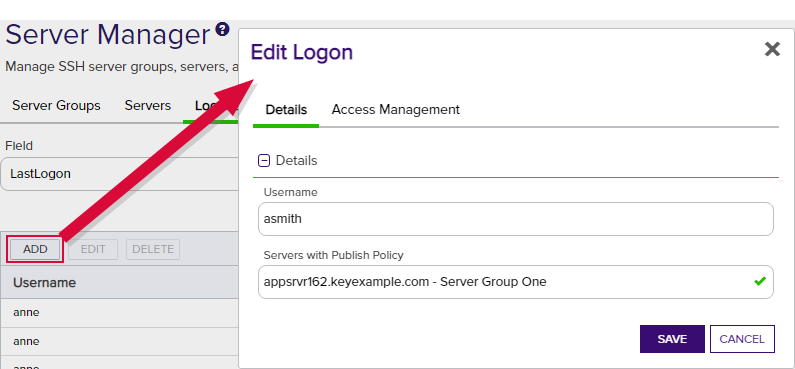
Figure 330: Add a Linux Logon—Basic Tab
-
In the Add Logon dialog on the Details tab, enter a Linux Username for the user.
Tip: If you have enabled SSSD support for your Keyfactor Bash Orchestrator The Bash Orchestrator, one of Keyfactor's suite of orchestrators, is used to discover and manage SSH keys across an enterprise. and are adding a domain user, specify the user in username@domain format. For example bbrown@keyexample.com (or, depending on SSSD configuration, such as the case-sensitivity setting; BBROWN@keyexample.com). Note that the logon may be modified by the SSSD configuration file in ways in which Keyfactor Command cannot know about. Refer to SSH-SSSD Case Sensitivity Flag for guidance on what to enter based on how the SSSD case sensitivity flag is configured.
The Bash Orchestrator, one of Keyfactor's suite of orchestrators, is used to discover and manage SSH keys across an enterprise. and are adding a domain user, specify the user in username@domain format. For example bbrown@keyexample.com (or, depending on SSSD configuration, such as the case-sensitivity setting; BBROWN@keyexample.com). Note that the logon may be modified by the SSSD configuration file in ways in which Keyfactor Command cannot know about. Refer to SSH-SSSD Case Sensitivity Flag for guidance on what to enter based on how the SSSD case sensitivity flag is configured. - In the Servers with Publish Policy dropdown on the Details tab, select an available SSH server on which to create the logon. Only servers that are configured in inventory and publish policy mode (see Server Manager) will appear in this dropdown. This field is required.
-
On the Access Management tab in the Users & Groups with Login Access dropdown, select a user or service account to associate the logon with. Only accounts that have keys stored in Keyfactor Command or that have been designated as server group owners will appear in the dropdown. If desired, you may enter an Active Directory group name in this field. This will cause the keys stored in Keyfactor Command for any Active Directory users that are members of this group to be mapped to the selected Linux logon and published to the server on which the Linux logon exists. Any Active Directory users that are members of this group but who do not have keys stored in Keyfactor Command will not be mapped to the selected Linux logon. Click Add. The Access Management tab is optional.
Tip: For keys created through the My SSH Key portal (see My SSH Key), a Keyfactor user is an Active Directory user account. For keys created through the Service Account Keys page (see Service Account Keys), a Keyfactor user is a user-generated service account name of the form servicename@hostname The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername)..
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername)..
Figure 331: Add a Linux Logon—Access Management Tab
- Click Save to save the new logon.