Application Settings
Many of the settings that control the behavior of Keyfactor Command features are configurable from the Applications Settings on the System setting menu. Browse to System Settings Icon ![]() > Application Settings. The tables below provide a brief description of these settings.
> Application Settings. The tables below provide a brief description of these settings.
Each tab of the Applications Settings page is organized into sections—a General section and additional sections based on the functionality controlled by each tab. Click the plus ( /
/ ) next to a section to toggle expand/collapse that section.
) next to a section to toggle expand/collapse that section.
Depending on your Keyfactor Command license, not all application settings may be applicable in your environment.
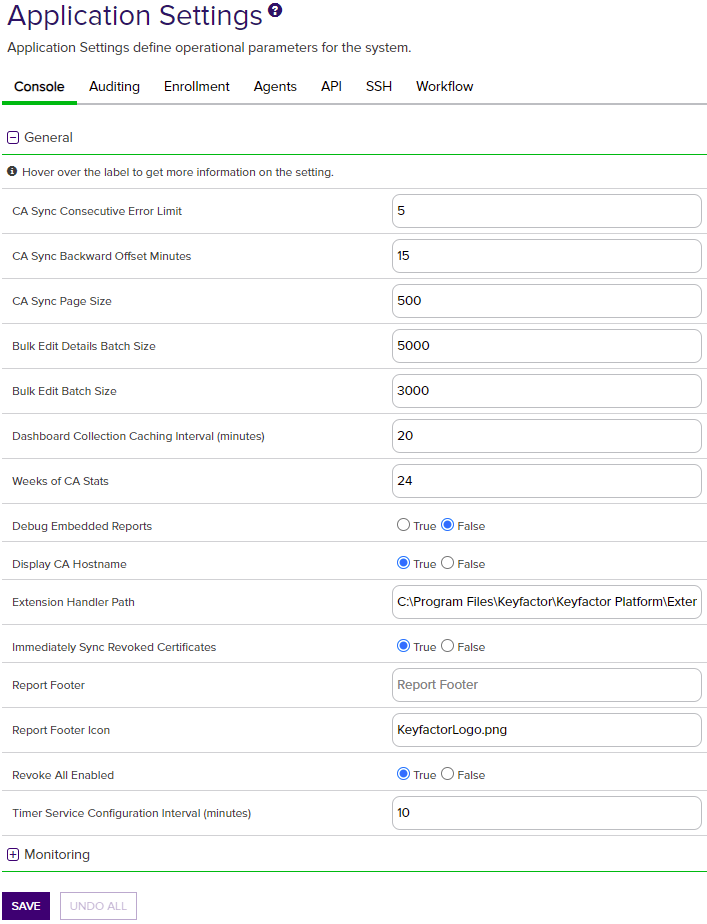
Figure 337: Console Application Settings: General
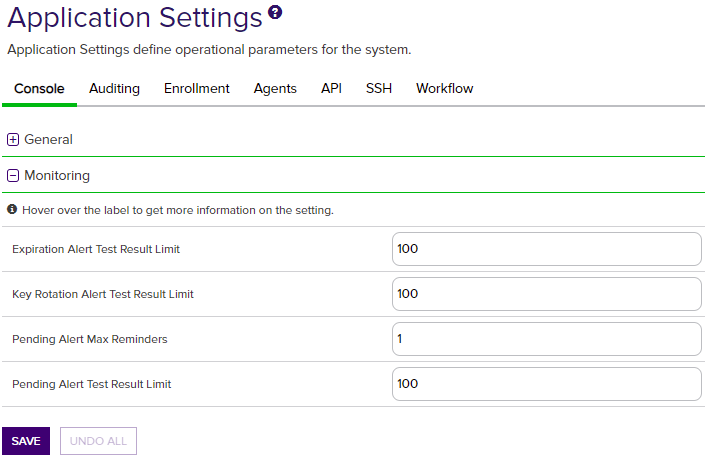
Figure 338: Console Application Settings: Monitoring
Table 22: Console Application Settings
|
Tab |
Section |
Field |
Description |
|---|---|---|---|
|
Console |
General |
Bulk Edit Details Batch Size |
The number of certificates at a time that are read from the database when using the Edit All feature to edit certificate metadata. This setting can be adjusted if there are responsiveness issues when editing large numbers of certificates at once. The default value is 5000. |
|
Console |
General |
Bulk Edit Batch Size |
The number of certificates at a time that are saved to the database when using the Edit All feature to edit certificate metadata. This setting can be adjusted if there are responsiveness issues when editing large numbers of certificates at once. The default value is 3000. |
| Console | General | CA Sync Consecutive Error Limit | The number of errors a CA synchronization can encounter before the synchronization job stops (without running to completion). |
| Console | General | CA Sync Backward Offset Minutes |
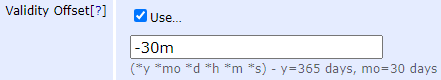
The number of minutes to offset when determining whether a certificate requested outside of Keyfactor Command should be included in an incremental synchronization. Adjusting this value can be helpful in situations of extreme clock skew or when the EJBCA Validity Offset setting is enabled. Note: For EJBCA CAs, if the certificate profile has a Validity Offset configured to a value greater than the value configured in the CA Sync Backward Offset Minutes application setting (15 minutes by default), certificates requested outside of Keyfactor Command will not be picked up on incremental scans. These certificates will only appear in Keyfactor Command on a full synchronization. The CA Sync Backward Offset Minutes application setting should be set to the same number of minutes as the Validity Offset value, if Validity Offset is configured.
Figure 339: EJBCA Certificate Profile Validity Offset Greater than 15 Minutes |
| Console | General | CA Sync Page Size | The number of records at a time that are read from the CA during a CA synchronization job. The default value is 500.
Note: This setting applies only to EJBCA CAs. |
|
Console |
General |
Dashboard Collection Caching Interval (minutes) |
The number of minutes before data for the Collections dashboard panel is refreshed. The default value is 20. |
|
Console |
General |
Weeks of CA Stats |
The number of weeks of CA data to include in the dashboard graphs. The default value is 24. |
|
Console |
General |
Debug Embedded Reports |
If set to True, causes an Enable Debug tickbox to appear on the parameters page for reports you access and run from the Navigator (reports on the Reports menu dropdown of the Management Portal). This option does not appear for reports generated from the Report Manager grid. When enabled it allows the reports to output debug level information when they run. If set to False, does not display the Enable Debug option. The default value is False. Tip: When the debugging option is enabled, a small debug icon (
|
|
Console |
General |
Display CA Hostname |
If set to True, causes both the CA’s FQDN and logical name (e.g. ca2.keyexample.com\Corp Issuing CA Two) to display in the CA fields on the Certificate Authority, Certificate Requests and API Applications pages of the Management Portal. If set to False, only the CA’s logical name (e.g. Corp Issuing CA Two) displays on these pages. The default value is True. |
|
Console |
General |
Extension Handler Path |
The path to the location on the Keyfactor Command server where the event handler .dll files are stored. By default this is: C:\Program Files\Keyfactor\Keyfactor Platform\ExtensionLibrary\.
As of version 9.0 of Keyfactor Command, PowerShell scripts for alert handlers need to be in the extension path or a subdirectory of it specified by this application setting. For example, create a directory called Scripts under the ExtensionLibrary directory and then reference your PowerShell script as Scripts\MyPowerShell.ps1. Any scripts referenced by PowerShell handlers that are outside this path will fail to run. |
|
Console |
General |
Immediately Sync Revoked Certificates |
If set to True, causes certificates to immediately sync to Keyfactor Command upon revocation rather than waiting for the next scheduled synchronization cycle. The default value is True. |
| Console | General | Report Footer | A string that appears at the bottom of Logi-based reports either generated from the Management Portal or generated with the Report Manager in PDF format. The report footer appears only at the very end of the report, not at the foot of every page in the report. |
| Console | General | Report Footer Icon | The file name of an image to be used at the bottom of each page of exported and scheduled PDF reports. You can use this to replace the Keyfactor logo with a custom image on your reports. The image is auto set to a height of 30px. This image should be placed in the _SupportFiles folder under the Logi folder (located at C:\Program Files\Keyfactor\Keyfactor Platform\Logi by default). |
|
Console |
General |
Revoke All Enabled |
If set to True, causes the Revoke All button to appear at the top of certificate search and collection grids to allow users with appropriate permissions to revoke all certificates shown in the grid or included in the certificate collection. If set to False, hides the Revoke All button and disables the POST /Certificates/RevokeAll API endpoint. The default value is False for new installations of Keyfactor Command beginning with release 10.4. |
|
Console |
General |
Timer Service Configuration Interval (minutes) |
The number of minutes between checks by the master scheduling service for changes to the synchronization schedules. Any changes made to this value will not be applied until the Keyfactor Command service is restarted. The default value is 10. |
|
Console |
Monitoring |
Expiration Alert Test Result Limit |
The maximum number of expiration alert emails that will be sent when an expiration alert test is run from within the Management Portal. If the number set here is exceeded during a test, emails will not be sent, but a portion of the alerts will be visible on the expiration alerts test page (see Testing Expiration Alerts). The default value is 100. |
| Console | Monitoring | Key Rotation Alert Test Result Limit | The maximum number of key rotation alert emails that will be sent when a key rotation alert test is run from within the Management Portal. If the number set here is exceeded during a test, emails will not be sent, but a portion of the alerts will be visible on the key rotation alerts test page (see Testing Key Rotation Alerts). The default value is 100. |
|
Console |
Monitoring |
Pending Alert Test Result Limit |
The maximum number of pending alert emails that will be sent when a pending alert test is run from within the Management Portal. If the number set here is exceeded during a test, emails will not be sent, but a portion of the alerts will be visible on the pending alerts test page (see Testing Pending Request Alerts). The default value is 100. |
|
Console |
Monitoring |
Pending Alerts Max Reminders |
The maximum number of pending alert emails that will be sent for a given pending certificate. Every time a pending alert task is run, an email will be sent for a given pending certificate until the limit is reached. It is recommended that the number is kept at 5 or less. The default value is 1. |
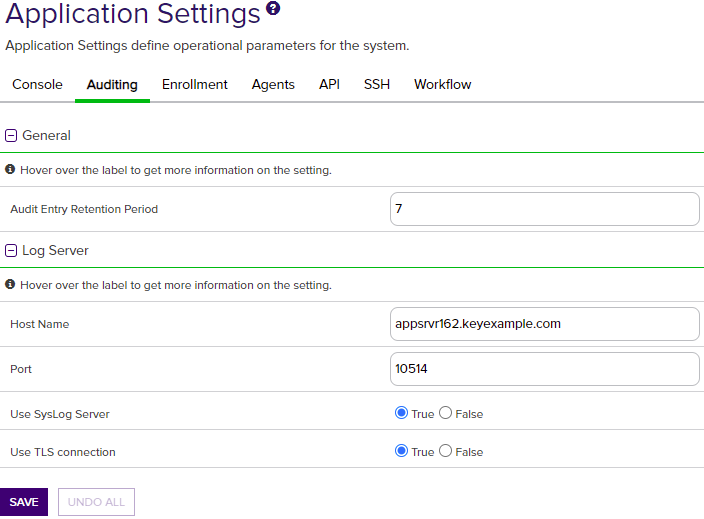
Figure 340: Audit Log Application Settings
Table 23: Audit Log Application Settings
|
Tab |
Section |
Field |
Description |
|---|---|---|---|
|
Auditing |
General |
Audit Entry Retention Period |
The number of years to retain the audit log entry details. The default value is 7. Note: The audit log cleanup job runs once daily and removes any audit log entries older than the time specified in the retention parameter except those in the following protected categories:
Audit logs belonging to protected categories are retained indefinitely and cannot be deleted. To retain all audit log entries indefinitely, disable the job in the Keyfactor Command configuration wizard. To do this, in the configuration wizard on the Service tab, uncheck the Everything box and then uncheck the Purge Audit Log History box. |
|
Auditing |
Log Server |
Host Name |
The host name of the centralized logging server to receive the Keyfactor Command audit log entries. |
|
Auditing |
Log Server |
Port |
The port to connect to the centralized logging server. The default port (configurable during install) is 514. |
|
Auditing |
Log Server |
Use SysLog Server |
If set to True, enables sending audit log details to a centralized logging server. See Audit Log Output to a Centralized Logging Solution. |
| Auditing | Log Server | Use TLS Connection | If set to True, enables sending audit log details to a centralized logging server over a TLS connection. See Audit Log Output to a Centralized Logging Solution. |
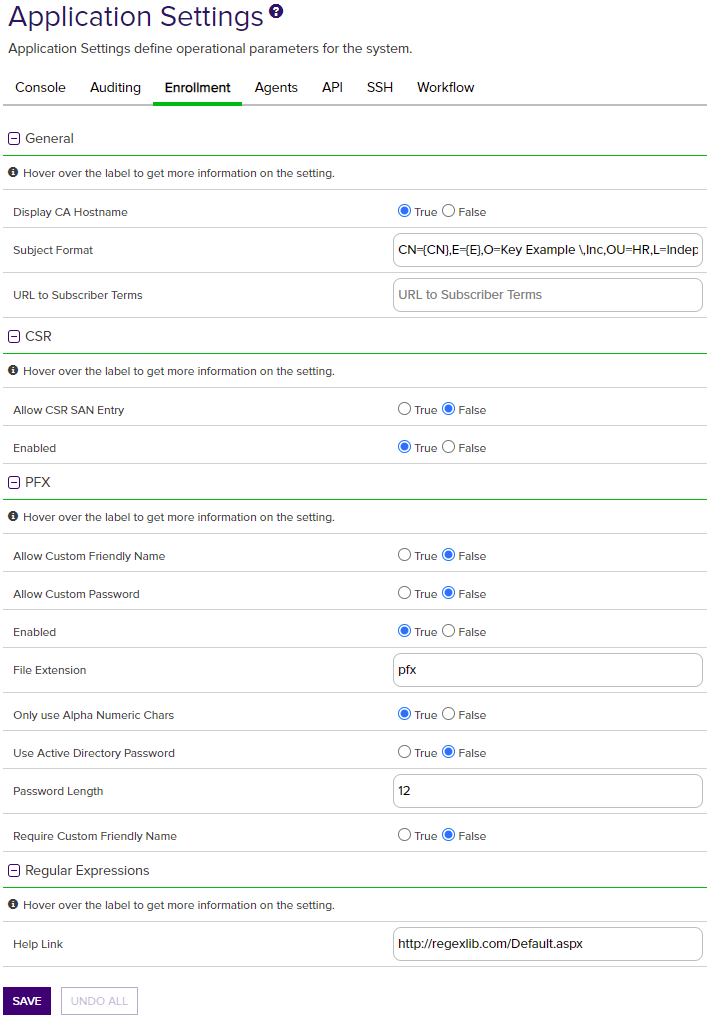
Figure 341: Enrollment Application Settings
Table 24: Enrollment Application Settings
|
Tab |
Section |
Field |
Description |
|---|---|---|---|
| Enrollment | General | Display CA Hostname | If set to True, causes both the CA’s FQDN and logical name (e.g. ca2.keyexample.com\Corp Issuing CA Two) to display in the CA dropdowns in the Keyfactor Command Management Portal interfaces. If set to False, only the CA’s logical name (e.g. Corp Issuing CA Two) displays in these dropdowns. The default value is True. |
| Enrollment | General | Subject Format |
The format of the subject field that will be created for the certificates requested through the Keyfactor Command Management Portal if the template used for enrollment is set to supply in request. For example: CN={CN},E={E},O=Key Example\, Inc.,OU={OU},L=Chicago,ST=IL,C=US
The data in the subject format takes precedence over any data entered during PFX enrollment or supplied by enrollment defaults (see Enrollment Defaults Tab). For example, with the above subject format, the organization for certificates generated through PFX enrollment will always be Key Example, Inc. regardless of what is shown on the PFX enrollment page during enrollment. This setting applies to CSRs generated using the CSR generation method in the Keyfactor Command Management Portal, CSR and PFX enrollments done in the Keyfactor Command Management Portal, and to CSR and PFX enrollments done using the Classic API. Data from the default subject does not display on the CSR or PFX enrollment page. To define defaults that will display in the PFX enrollment form (and can be modified by users), use enrollment defaults (see Enrollment Defaults Tab). Note: Backslashes are required before any commas embedded within values in the subject field (e.g. O=Key Example\, Inc.). Quotation marks should not be used in the strings in the fields except in the case where these are part of the desired subject value, as they are processed as literal values.
Tip: The default subject format does not apply to enrollments done using the Keyfactor API.
|
| Enrollment | General | URL to Subscriber Terms | The URL for a web page providing terms and conditions to which a user must agree before being allowed to enroll for a certificate if the CA setting of Require Subscriber Terms is enabled. |
| Enrollment |
CSR |
Allow CSR SAN Entry |
If set to True, enables the section of the CSR enrollment page that allows for entry of custom subject alternative names (SANs). The default value is False. |
| Enrollment | CSR | Enabled | If set to True, enables administrative CSR enrollment. The default value is True. |
|
Enrollment |
PFX |
Allow Custom Friendly Name |
If set to True, enables the section of the PFX enrollment page that allows for entry of a custom friendly name for the certificate. The default value is False. |
|
Enrollment |
PFX |
Allow Custom Password |
If set to True, enables the section of the PFX enrollment page that allows for entry of a custom password for the PFX file. The default value is False. |
|
Enrollment |
PFX |
Enabled |
If set to True, enables administrative PFX enrollment. The default value is True. |
|
Enrollment |
PFX |
File Extension |
The file extension that will be given to the certificate files. Typical extensions are PFX or P12. The default value is PFX. |
|
Enrollment |
PFX |
Only use Alpha Numeric Chars |
If set to True, the one-time password generated to encrypt the PFX file acquired through the Keyfactor Command Management Portal (if the user’s Active Directory password is not used) will contain just numbers and letters. If set to False, the password will contain numbers, letters and special characters. This setting is ignored if PFX Use Active Directory Password is set to True. The default value is True. |
|
Enrollment |
PFX |
Use Active Directory Password |
If set to True, uses the user’s Active Directory password to encrypt the PFX file containing the certificate acquired through the Keyfactor Command Management Portal and its private key. If set to False, generates a one-time password to encrypt the PFX file. The default value is False. Important: If you change this setting in the application settings you must also change the authentication method configured on the IIS virtual application KeyfactorPortal through the IIS Manager. If you set this option to True, you should configure only Basic Authentication in IIS. If you set this option to False, you may configure either only Windows Authentication or both Basic Authentication and Windows Authentication (the default) in IIS. This is because when you authenticate to the Management Portal using integrated Windows authentication (Kerberos), Keyfactor Command does not have access to your credentials to apply your password to the PFX file.
|
|
Enrollment |
PFX |
Password Length |
The number of characters in the one-time password generated to encrypt the PFX file acquired through the Keyfactor Command Management Portal. The minimum number is 8. The default value is 12. |
|
Enrollment |
PFX |
Require Custom Friendly Name |
If set to True, requires the user to enter a custom friendly name for the certificate. The default value is False. |
| Enrollment | PFX | Enable Legacy Encryption | If set to True, the historical algorithm set (3DES/SHA1/RC2) is used for PFX enrollments. If set to False, the newer algorithm set provided by Windows (AES256/SHA256/AES256) is used instead. The default value is False. |
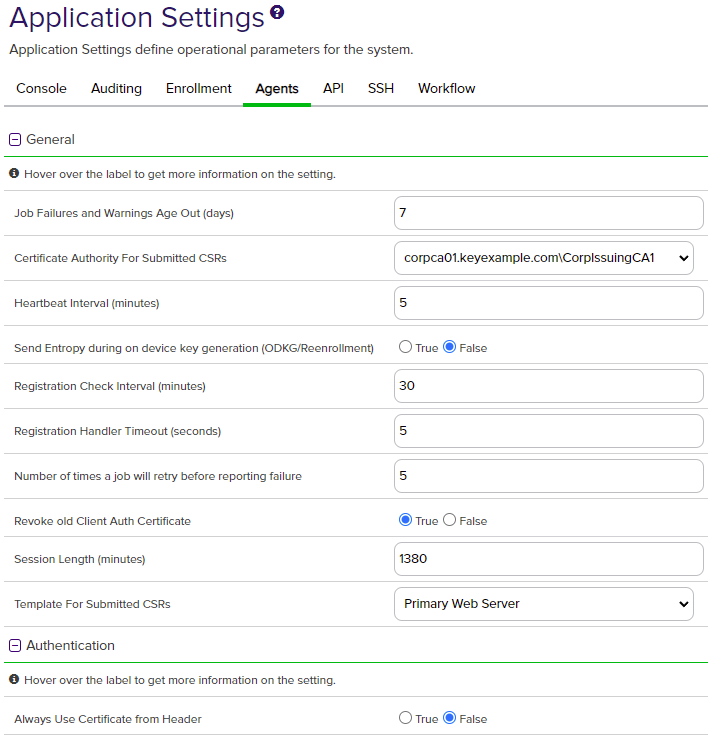
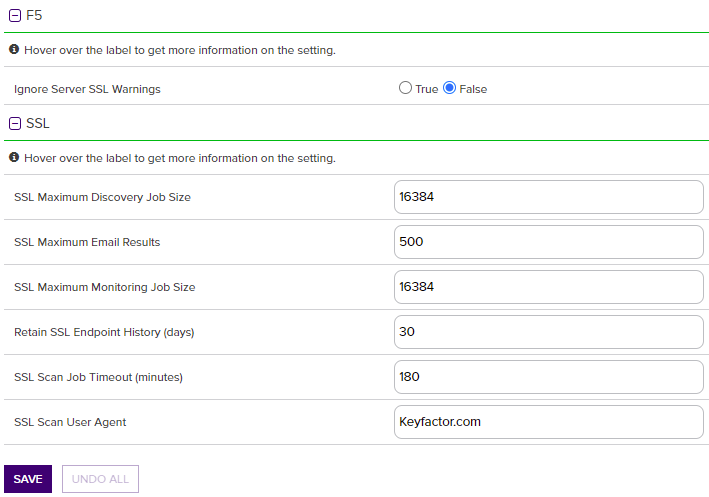
Figure 342: Agents Application Settings
Table 25: Agents Application Settings
|
Tab |
Section |
Field |
Description |
|---|---|---|---|
|
Agents |
General |
Job Failures and Warnings Age Out (days) |
The number of days orchestrator job failures and warnings should be included in the count of failures on the orchestrator job history tab. The default value is 7. |
|
Agents |
General |
Certificate Authority For Submitted CSRs |
The certificate authority used for reenrollment requests made from the Certificate Stores page. See Certificate Store Reenrollment. |
|
Agents |
General |
Heartbeat Interval (minutes) |
The frequency, in minutes, with which an orchestrator (e.g. Keyfactor Universal Orchestrator, Keyfactor Java Agent or Keyfactor Mac Auto-Enrollment Agent) should query the Keyfactor Command orchestrator server for a status on the accuracy of its jobs list. The default value is 5. |
|
Agents |
General |
Send Entropy during on device key generation (ODKG/Reenrollment) |
Whether the configure call returns the property Entropy containing 2048 bytes. This property is optional via this app setting. The default is false on upgrades and new installs. |
|
Agents |
General |
Registration Check Interval (minutes) |
The frequency, in minutes, with which an orchestrator should check with the Keyfactor Command server to see if it has been approved as an orchestrator. The default value is 30. |
|
Agents |
General |
Registration Handler Timeout (seconds) |
The maximum number of seconds an auto-registration handler is allowed to attempt to run before being halted and declared to be deferred. The default value is 90 for more recently installed systems. Keyfactor recommends using a value of at least 60 seconds. |
| Agents | General | Number of times a job will retry before reporting failure | The number of times an orchestrator job will attempt to retry running if it encounters an error before failing. The default value is 5. |
| Agents | General | Revoke old Client Auth Certificate | If set to True, revokes the previous certificate used for orchestrator client certificate authentication after the certificate has successfully been renewed using the client certificate authentication renewal extension. The default value is True. |
|
Agents |
General |
Session Length (minutes) |
The frequency, in minutes, with which an orchestrator renews its session with the Keyfactor Command server and obtains a new session token in the absence of any other reason for the orchestrator to renew the session token. The session token is also renewed when an orchestrator job changes (e.g. an inventory schedule changes, a certificate is scheduled for addition to a certificate store, or a certificate is scheduled for removal from a store) or the orchestrator is restarted. The default value is 1380. |
|
Agents |
General |
Template For Submitted CSRs |
The template used for reenrollment requests made from the Certificate Stores page. See Certificate Store Reenrollment. The template selected for this value must be available for enrollment against the CA listed in the Certificate Authority For Submitted CSRs setting. |
| Agents | Authentication | Always Use Certificate from Header | If set to True, the orchestrator will be authenticated using the client certificate provided in the header from the orchestrator rather than client certificate used to make the connection to Keyfactor Command. This is useful in configurations where one certificate is used to authenticate the orchestrator to a proxy and a second certificate is used to authenticate the proxy to Keyfactor Command. The original certificate from the orchestrator can be preserved in the header to present to Keyfactor Command for authentication. The default value is False. |
|
Agents |
F5 |
Ignore Server SSL Warnings |
If set to True, the orchestrator will connect to the F5 device using SSL even if it detects a problem with the certificate on the F5 device (e.g. it doesn’t trust the issuer of the certificate because the certificate is self-signed). This option applies only to the F5 methods based on the F5 SOAP API (see Certificate Stores). The F5 methods based on the F5 iControl REST API automatically ignore SSL warnings without the need to set this option. The default value is False. |
|
Agents |
SSL |
SSL Maximum Discovery Job Size |
The maximum number of endpoints for scanning that will be assigned to any one orchestrator for a given discovery scan job part. Together with the SSL Scan Job Timeout setting, this can be used to fine tune the running of SSL discovery scan jobs. The default value is 16,384. Note: A change made to this setting takes effect with the next discovery scan job. It does not affect currently running jobs.
|
|
Agents |
SSL |
SSL Maximum Email Results |
The maximum number of results to display in an SSL monitoring results email message table of certificates that have expired or are expiring shortly. The default value is 500. |
|
Agents |
SSL |
SSL Maximum Monitoring Job Size |
The maximum number of endpoints for scanning that will be assigned to any one orchestrator for a given monitoring scan job part. Together with the SSL Scan Job Timeout setting, this can be used to fine tune the running of SSL monitoring scan jobs. The default value is 16,384. Note: A change made to this setting takes effect with the next monitoring scan job. It does not affect currently running jobs.
|
|
Agents |
SSL |
Retain SSL Endpoint History (days) |
The number of days old an endpoint history record must be before it is available for deletion by the endpoint history cleanup process. Endpoint history records older than this will be retained if they are the last records for the given endpoint. Both the last discovery and last monitoring records will be retained regardless of age. The default value is 30. |
|
Agents |
SSL |
SSL Scan Job Timeout (minutes) |
The maximum number of minutes any one orchestrator is allowed to attempt to run an SSL scan job before the job for that orchestrator is abandoned and given to the next orchestrator in the orchestrator pool to run (if applicable). The default value is 180. Note: A change made to this setting takes effect immediately. It applies to currently running jobs as well as future jobs.
|
|
Agents |
SSL |
SSL Scan User Agent |
Defines what is sent to endpoints when Request Robots.txt is enabled on a SSL Network. |
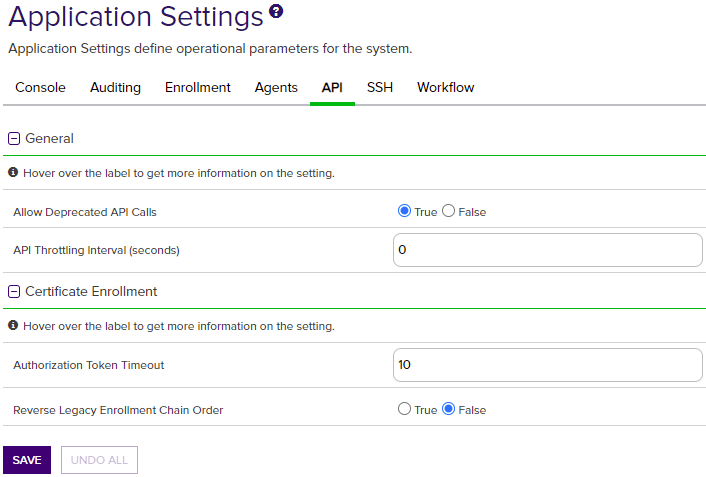
Figure 343: API Application Settings
Table 26: API Application Settings
|
Tab |
Section |
Field |
Description |
|---|---|---|---|
|
API |
General |
Allow Deprecated API Calls |
If set to False, API applications will not be able to access earlier versions of API methods or other legacy API methods that have been replaced or updated. Many of the updated methods offer additional security measures, so this setting can reduce the risk of unauthorized API access, but may cause API applications written against these earlier versions to stop functioning correctly. If you do not have any such applications, this should be set to False. The default is True. For more information, see Versioning in theKeyfactor Web APIs Reference Guide. |
|
API |
General |
API Throttling Interval (seconds) |
The maximum rate at which API applications can make requests to the API. A larger value will mitigate risks from certain denial of service and brute-force/dictionary attacks, but will limit the performance of applications needing to make multiple API calls. This can be set to zero to disable throttling. |
|
API |
Certificate Enrollment |
Authorization Token Timeout |
The number of minutes for which a token (from a GET token request such as GET /CertEnroll/1/Token) is valid as an HTTP request header for authentication. This setting also controls the number of minutes in the past a /CertEnroll/3 request timestamp can be and still be accepted. |
| API | Certificate Enrollment | Reverse Legacy Enrollment Chain Order | If set to True, switches the order of the certificates returned in the certificate chain from an enrollment request with the Classic API (such as a POST /CertEnroll/3/Pkcs10 request). For example, if the certificates are being returned with the CA's root certificate as the first certificate in the list and the end entity certificate as the last certificate in the list while this value is False, changing this value to True will cause the certificates to be returned with the end entity certificate first in the list and the CA's root certificate last in the list. The default value is False. |
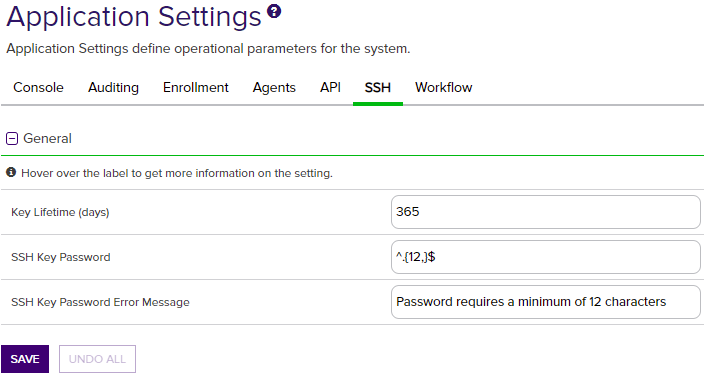
Figure 344: SSH Settings
Table 27: SSH Application Settings
|
Tab |
Section |
Field |
Description |
|---|---|---|---|
|
SSH |
General |
Key Lifetime (days) |
The number of days for which an SSH key generated through My SSH Key (see Generating a New Key) or Service Account Keys (see Creating a Service Account Key) is considered valid. The default is 365 days. |
| SSH | General | SSH Key Password |
The regular expression against which the password entered when creating, rotating or downloading keys for both user SSH keys (My SSH Key) and service account SSH keys (Service Account Keys) will be validated. The default is a minimum of 12 characters configured as: ^.{12,}$
|
| SSH | General | SSH Key Password Error Message | The error message displayed to the user in the relevant SSH pages of the Keyfactor Command Management Portal when the password referenced does not match the regular expression defined for the password using the SSH Key Password setting. |
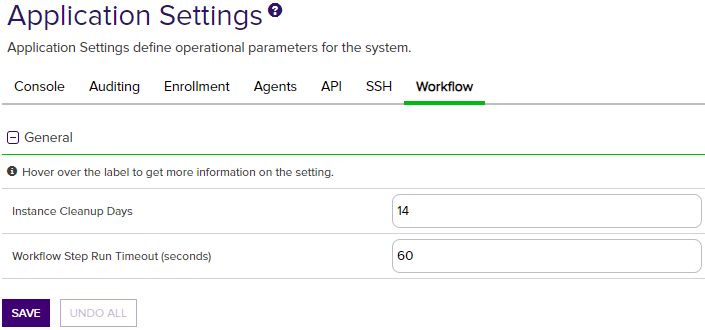
Figure 345: Workflow Settings
Table 28: Workflow Application Settings
|
Tab |
Section |
Field |
Description |
|---|---|---|---|
|
Workflow |
General |
Workflow Step Run Timeout (seconds) |
The number of seconds a workflow instance step will be allowed to run before timing out and setting the instance to a status of Failed. The default is 60 seconds. |
| Workflow | General | Instance Cleanup Days | The number of days to retain completed workflow instances (successful or failed) before they are purged. The cleanup job runs daily at midnight. The default value is 14. |
You can also find the help icon at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Command Documentation Suite at the home page or the Keyfactor API Endpoint Utility.