Create Service Accounts for the Universal Orchestrator
The Keyfactor Universal Orchestrator![]() The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with Windows servers (a.k.a. IIS certificate stores) and FTP capable devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can run custom jobs to provide certificate management capabilities on a variety of platforms and devices (e.g. F5 devices, NetScaler devices, Amazon Web Services (AWS) resources) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux. makes use of up to two service accounts to allow it to communicate with the Keyfactor Command server. These two service accounts work together to transfer information from the Universal Orchestrator
The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with Windows servers (a.k.a. IIS certificate stores) and FTP capable devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can run custom jobs to provide certificate management capabilities on a variety of platforms and devices (e.g. F5 devices, NetScaler devices, Amazon Web Services (AWS) resources) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux. makes use of up to two service accounts to allow it to communicate with the Keyfactor Command server. These two service accounts work together to transfer information from the Universal Orchestrator![]() Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. to the Keyfactor Command server. The two service accounts can be thought of as players on two sides of a fence, with the service account that the Universal Orchestrator runs as lobbing information over the fence to the service account that communicates with the Keyfactor Command server side to catch and hand to the Keyfactor Command server. Below these are referred to as the Universal Orchestrator service account and the Keyfactor Command connect service account.
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. to the Keyfactor Command server. The two service accounts can be thought of as players on two sides of a fence, with the service account that the Universal Orchestrator runs as lobbing information over the fence to the service account that communicates with the Keyfactor Command server side to catch and hand to the Keyfactor Command server. Below these are referred to as the Universal Orchestrator service account and the Keyfactor Command connect service account.
The service accounts need to be created prior to installation of the Universal Orchestrator software (except as noted below for installations on Linux), and the person installing the Universal Orchestrator software needs to know the domain (if applicable), username and password of each service account.
Universal Orchestrator Service Account
Your choice of service account may vary depending on the operating system on which you are installing the orchestrator:
-
Universal Orchestrator on Windows
When the Universal Orchestrator is installed on Windows, you may use either the built-in Network Service account or a custom service account as the Universal Orchestrator service account. Keyfactor recommends using the default of Network Service unless you have a need to use a custom service account. If you choose to use a custom service account, it may be a standard Active Directory service account, an Active Directory group managed service account (gMSA), or a local machine account. Of the custom service account choices, an Active Directory account is more typically used unless the machine is not domain-joined. If you use an Active Directory service account, it needs to be a service account in the forest
 An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. in which the Universal Orchestrator is installed. This is not necessarily the same forest as the forest in which the Keyfactor Command server is installed. The Universal Orchestrator on Windows has several possible roles, and the choice of service account may vary depending on these roles:
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. in which the Universal Orchestrator is installed. This is not necessarily the same forest as the forest in which the Keyfactor Command server is installed. The Universal Orchestrator on Windows has several possible roles, and the choice of service account may vary depending on these roles: Certificate Store Management
Certificate Store Management
If your Universal Orchestrator will be managing certificate stores, you may choose to run the orchestrator as the built-in Network Service account or as an Active Directory service account. However, if you plan to use the Universal Orchestrator to manage IIS certificate stores, you must use an Active Directory service account because of the permissions that must be granted on each server where you will be managing IIS certificate stores (see Configure the Targets for IIS Management). A local account is generally not used in this role.
 SSL Management
SSL Management
If your Universal Orchestrator SSL
 TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. discovery and monitoring, you may choose to run the orchestrator as the built-in Network Service account or as a custom service account.
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. discovery and monitoring, you may choose to run the orchestrator as the built-in Network Service account or as a custom service account. CA Management
CA Management
If your Universal Orchestrator will be providing certificate synchronization from a remote CA
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA., the Universal Orchestrator service account needs to be able to read the CA(s) in the forest in which the Universal Orchestrator is installed to retrieve certificates and templates from them. When the Universal Orchestrator is used in this configuration, this is typically a forest other than the forest in which the Keyfactor Command server is installed. For domain-joined CAs, you would typically use an Active Directory service account in the remote forest (the forest where the Universal Orchestrator is installed). For a non-domain-joined CA, you may use a local account created on the CA as the Universal Orchestrator service account instead of a domain account.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA., the Universal Orchestrator service account needs to be able to read the CA(s) in the forest in which the Universal Orchestrator is installed to retrieve certificates and templates from them. When the Universal Orchestrator is used in this configuration, this is typically a forest other than the forest in which the Keyfactor Command server is installed. For domain-joined CAs, you would typically use an Active Directory service account in the remote forest (the forest where the Universal Orchestrator is installed). For a non-domain-joined CA, you may use a local account created on the CA as the Universal Orchestrator service account instead of a domain account. Custom Extensions
Custom Extensions
Keyfactor offers several publicly available custom extensions for the Universal Orchestrator in the Keyfactor GitHub. Many of these will operate correctly with a Universal Orchestrator service account of Network Service, but some may require a custom account. Check the specific documentation for each custom extension for more information:
The Keyfactor Orchestrator Service on the server on which the Universal Orchestrator is installed runs as the Universal Orchestrator service account. This service account requires local “Log on as a service” permissions; this permission is granted automatically during installation.
-
Universal Orchestrator on Linux
For the purposes of this documentation, it is assumed that Linux machines will be non-domain joined and will use a local account to run the Universal Orchestrator.
For Linux systems, Keyfactor recommends running the service as an account other than root. The default Universal Orchestrator service account of keyfactor-orchestrator will be created automatically during the install if the force option is used. If you prefer not to use the force option, you may create a local service account before running the installation script.
Keyfactor Command Connect Service Account
For the Keyfactor Command connect service account, a standard Active Directory service account in the primary Keyfactor Command server forest is used. Group managed service accounts are not supported in this role. This service account appears in the Management Portal Orchestrator Management grid as the Identity for the Universal Orchestrator.
Permissions
The user installing the orchestrator must have the SeBackupPrivilege and SeRestorePrivilege rights on the Keyfactor Command server. Normally, administrators are granted these permissions by default, but you should confirm the permissions prior to starting the install. These permissions can be set through Group Policy or Local Security Policy, and can be found under Local Policies\User Rights Assignment as Back up files and directories and Restore files and directories.
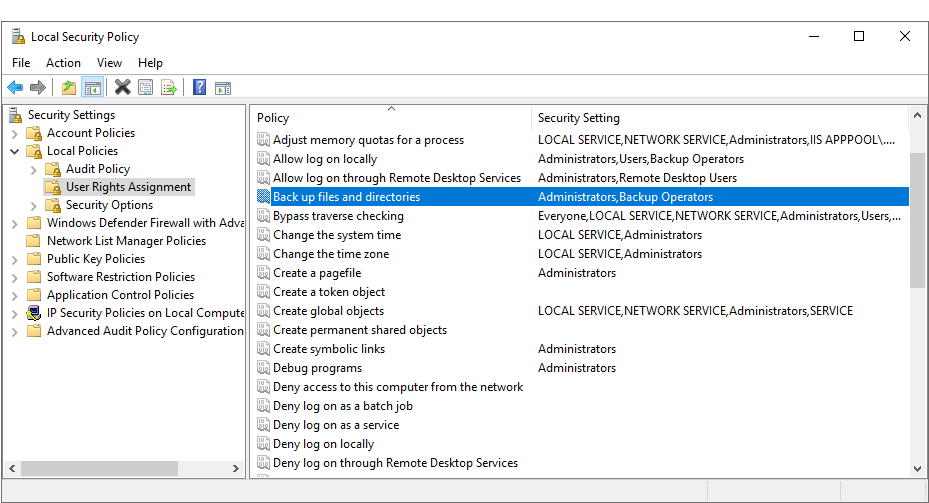
Figure 526: Local Security Policy
For more information on this from Microsoft, see: