Bash Orchestrator
SSH![]() The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. supports a wide variety of authentication mechanisms. Often, enterprises fall back to simple username and password at least some of the time due to the complexities of key management for key-based authentication. Without key management, SSH keys tend to multiply, and you can quickly lose track of who has access to what where. The Keyfactor Bash Orchestrator
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. supports a wide variety of authentication mechanisms. Often, enterprises fall back to simple username and password at least some of the time due to the complexities of key management for key-based authentication. Without key management, SSH keys tend to multiply, and you can quickly lose track of who has access to what where. The Keyfactor Bash Orchestrator![]() The Bash Orchestrator, one of Keyfactor's suite of orchestrators, is used to discover and manage SSH keys across an enterprise. is designed to allow organizations to inventory and manage secure shell (SSH) keys across the enterprise.
The Bash Orchestrator, one of Keyfactor's suite of orchestrators, is used to discover and manage SSH keys across an enterprise. is designed to allow organizations to inventory and manage secure shell (SSH) keys across the enterprise.
The orchestrator runs on Linux servers and can be operated in two possible modes:
- The orchestrator is used in inventory only mode to perform discovery of SSH public keys and associated Linux user accounts across multiple configured targets. When used in inventory and publish policy mode, the orchestrator:
- Scans the authorized_keys files of all current users on each configured server.Note: OpenSSH maintains a file for each user that contains the public keys authorized to connect via SSH. By default, this file is named authorized_keys. In this document, we refer to this file as authorized_keys, however in your environment, this file may have a different name. The file name used in a given environment is defined in the AuthorizedKeysFile setting in the OpenSSH sshd_config file.
- Aggregates all public key
 In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. data per Linux user logon.
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. data per Linux user logon. - Reports aggregate key and logon data back to Keyfactor Command.
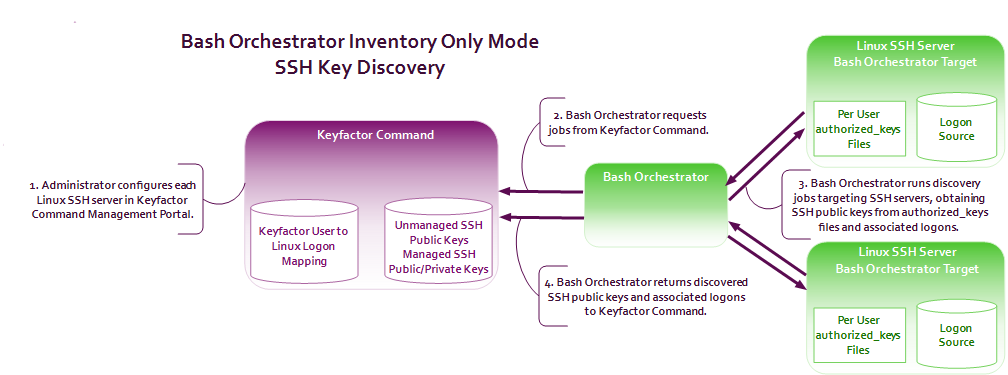
Figure 546: SSH Key Discovery Flow
- Scans the authorized_keys files of all current users on each configured server.
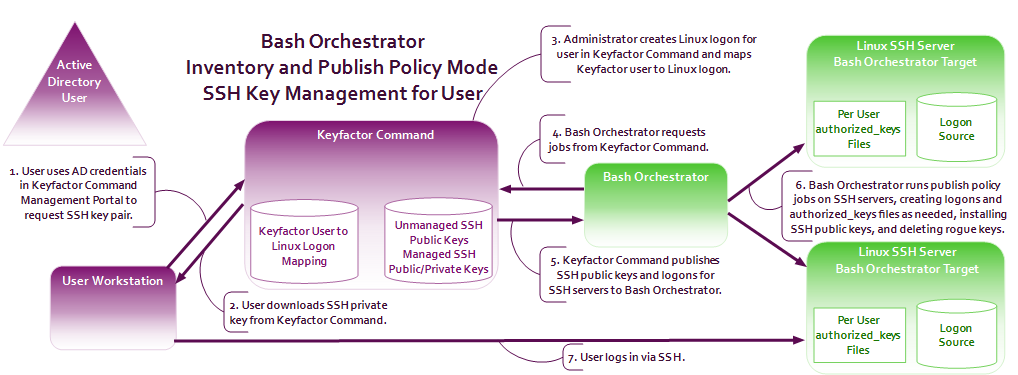
- When operated in inventory and publish policy mode, the orchestrator can be used to add SSH public keys and Linux user accounts on targets and remove rogue keys that appear without authorization. Figure 547: SSH User Key Management Flow shows the flow from a user requesting a new key pair
 In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. to the public key being placed on a target server to allow the user to connect to the server via SSH. The flow is similar for requesting a key pair for a service, though the request is made by an administrator through a different interface in the Keyfactor Command Management Portal.
When used in inventory and publish policy mode, policies are published to the orchestrator from the Keyfactor Command server following this flow:
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. to the public key being placed on a target server to allow the user to connect to the server via SSH. The flow is similar for requesting a key pair for a service, though the request is made by an administrator through a different interface in the Keyfactor Command Management Portal.
When used in inventory and publish policy mode, policies are published to the orchestrator from the Keyfactor Command server following this flow:- The Keyfactor Command server determines what content needs to go into the authorized_keys files for each logon on each target server. Content includes keys and associated comments aggregated from all servers where that key was found. For example, if a given public key exists on three different servers for the same user but in the original authorized_keys files the key is associated with a different comment on each server, when Keyfactor Command publishes the key down to the servers, it will be published with an aggregated comment string (all three comments together in each authorized_keys file).
Aggregate logon and key information pushed down to each orchestrator target.
Orchestrator determines where to place key information, builds the file, and overwrites the existing file with the new one. The process is done in this way to enforce policy and prevent rogue keys from being placed in authorized_keys files.
Orchestrator informs Keyfactor Command of the success or failure of each machine logon combination.