Audit Log Security
Keyfactor considers the security and integrity of the audit log to be of the utmost importance and takes steps to ensure that transactions are recorded to the audit log accurately and retained without tampering until they are purged (by default, after 7 years—see Application Settings: Auditing Tab).
When Keyfactor Command is installed, a 64-byte key is generated for use in securing audit logs. This key is unique for the implementation. The key is encrypted and stored in the secrets table in SQL using either SQL-level encryption or application-level encryption, depending on the level of encryption selected during installation (see Database Tab in the Keyfactor Command Server Installation Guide). If application-level encryption is selected, use of a hardware security module (HSM) is supported. For more information, see Acquire a Public Key Certificate for the Keyfactor Command Server in the Keyfactor Command Server Installation Guide.
When an audit log record is created, the key components of it are signed using the unique 64-byte key and stored in the SQL database. The signature is retained and tracked. When the audit log is read, it is validated using the signature. If the signature does not match, the audit log is flagged as invalid (see Validate), as this could indicate that the record has been tampered with. The following data is included in the key components:
-
The date and time at which the action took place.
-
The audit message content, which will vary depending on the type of action that was audited. For example, for a modification to a template
 A certificate template defines the policies and rules that a CA uses when a request for a certificate is received., this would include:
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received., this would include:- Template common name
 A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). (short name)
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). (short name) - Template name
- Template OID
 Object identifiers or OIDs are a standardized system for identifying any object, concept, or "thing" with a globally unambiguous persistent name.
Object identifiers or OIDs are a standardized system for identifying any object, concept, or "thing" with a globally unambiguous persistent name. - Key size
 The key size or key length is the number of bits in a key used by a cryptographic algorithm.
The key size or key length is the number of bits in a key used by a cryptographic algorithm.
- Key type
 The key type identifies the type of key to create when creating a symmetric or asymmetric key. It references the signing algorithm and often key size (e.g. AES-256, RSA-2048, Ed25519).
The key type identifies the type of key to create when creating a symmetric or asymmetric key. It references the signing algorithm and often key size (e.g. AES-256, RSA-2048, Ed25519).
- Configuration tenant
 A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. (forest
A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. (forest An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers.)
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers.) - Private key
 Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. retention setting
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. retention setting - Key archival setting
- Allowed requesters setting
See also Download CSV.
- Template common name
-
The operation type (see Audit Log Operations).
-
The user who performed the auditable action.
In order to access the audit logs, users must be granted the Read role permission for the Auditing role (see Security Roles and Identities). Users with auditing Read permissions are allowed to access the audit log page and make API![]() A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. requests to obtain data from the audit log.
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. requests to obtain data from the audit log.
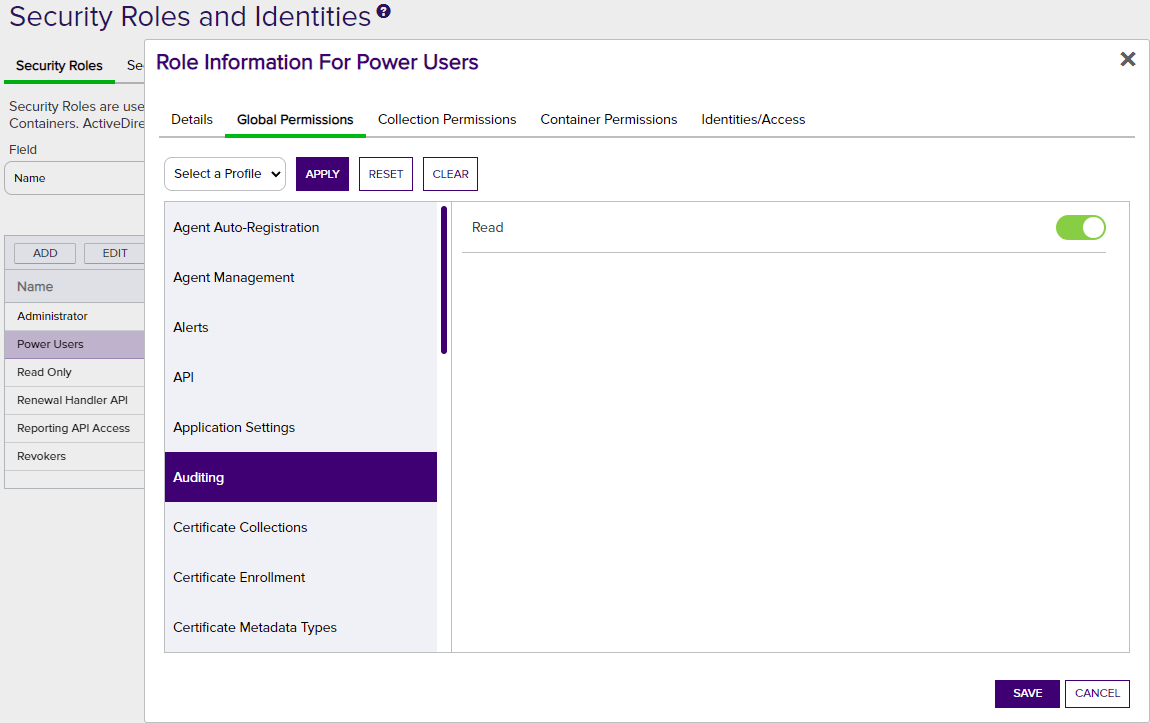
Figure 388: Security Role Showing Auditing Permissions Setting