Creating a Service Account Key
To create a new service account key:
- In the Management Portal, browse to SSH > Service Account Keys.
- On the Service Account Keys page, click Create.
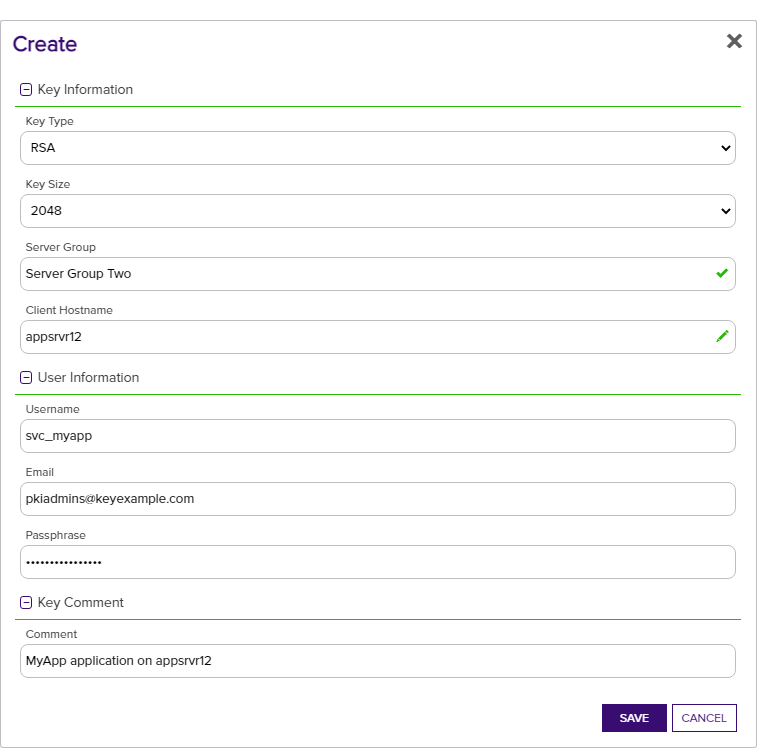
Figure 305: Add a Service Account Key
- In the Key Information section of the Create dialog, select a Key Type in the dropdown (see Key Type).
- In the Key Information section, select a Key Length in the dropdown (see Key Length). The available key lengths will vary depending upon the option select in the Key Type dropdown.
- In the Key Information section, select a Server Group in the dropdown (see SSH Server Groups). The server group is used to control who has access in the Management Portal to the service account key. It does not limit where the key can be published. This field is required.
- In the Key Information section, enter a Client Hostname reference for the service account key. This field is used for reference only and does not need to match an actual client hostname
 The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername).. It is used when building the full user name of the service account key for mapping to Linux logons for publishing to Linux servers (e.g. username@client_hostname). The naming convention is to enter the hostname of the server on which the application that will use the private key
The unique identifier that serves as name of a computer. It is sometimes presented as a fully qualified domain name (e.g. servername.keyexample.com) and sometimes just as a short name (e.g. servername).. It is used when building the full user name of the service account key for mapping to Linux logons for publishing to Linux servers (e.g. username@client_hostname). The naming convention is to enter the hostname of the server on which the application that will use the private key Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. resides (e.g. appsrvr12), but you can put anything you like in this field (e.g. cheesetoast). This field is required.
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. resides (e.g. appsrvr12), but you can put anything you like in this field (e.g. cheesetoast). This field is required. - In the User Information section of the page, enter the Username of the service account that will be using the key to connect to the target server (e.g. svc_myapp). This username will be combined with the Client Hostname to build the full user name of the service account key for mapping to Linux logons (e.g. svc_myapp@appsrvr12). You will need to know this full user name when creating the mappings to publish the public key
 In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. to the target servers (see Editing Access to an SSH Server Group, Editing Access to an SSH Server, Adding Logons, or Editing or Deleting a Logon). This field is required.
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key. to the target servers (see Editing Access to an SSH Server Group, Editing Access to an SSH Server, Adding Logons, or Editing or Deleting a Logon). This field is required. - In the User Information section of the page, enter the Email address of the administrator or group of administrators responsible for managing the key. This is the address to which key rotation alerts for this key will be directed (see Key Rotation Alerts). This field is required.
- In the User Information section, enter a Passphrase to encrypt the downloaded copy of the private key of the key pair
 In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key.. The service that uses the private key will need to be able to provide it when connecting via SSH. By default, the minimum password length is 12 characters (see the SSH Key Password setting in Application Settings: SSH Tab). This field is required.Tip: The private key downloads immediately at the conclusion of the creation process, encrypted with this passphrase. You may later download the private key again from this same page and encrypt it with a different passphrase, if desired.
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key.. The service that uses the private key will need to be able to provide it when connecting via SSH. By default, the minimum password length is 12 characters (see the SSH Key Password setting in Application Settings: SSH Tab). This field is required.Tip: The private key downloads immediately at the conclusion of the creation process, encrypted with this passphrase. You may later download the private key again from this same page and encrypt it with a different passphrase, if desired. - In the Key Comment section, enter a Comment to include with the key. This field is optional.
Tip: Although entry of an email address in the comment field of an SSH key is traditional, this is not a required format. The comment may contain any characters supported for string fields, including spaces and most punctuation marks.
- Click Save to save the new service account key.
Tip: Once the key pair is generated, an administrator needs to download the private key as an encrypted file and store it locally on the machine from which the service will make SSH connections using the private key. Additionally, an administrator needs to use Keyfactor Command to map the full user name built from the username and client hostname entered when generating the service account key pair (e.g. svc_myapp@appsrvr12) to the Linux logon account that the service account will operate as when logging in via SSH on the target server(s) where the public key needs to reside (see Editing Access to an SSH Server Group, Editing Access to an SSH Server, Adding Logons, or Editing or Deleting a Logon). After this is complete and the orchestrator
 Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. has published the public key to the target server(s), the service may connect via SSH to the target server(s) using the new private key for authentication. For more information, see SSH.
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. has published the public key to the target server(s), the service may connect via SSH to the target server(s) using the new private key for authentication. For more information, see SSH.

