SSH Users
On the Users tab of the Server Manager page you can view all the SSH![]() The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. users defined in Keyfactor Command. Both users and service accounts are included. See SSH for more information on the difference between users and service accounts. Active Directory groups may also be included if they have previously been used to create Linux logon to Keyfactor user mappings (see Editing Access to an SSH Server). Groups appear without associated keys (since keys are associated with the member users, not the groups). Users may appear here without associated keys if the user account has been used to grant ownership on a server group but the user has not requested an SSH key pair
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. users defined in Keyfactor Command. Both users and service accounts are included. See SSH for more information on the difference between users and service accounts. Active Directory groups may also be included if they have previously been used to create Linux logon to Keyfactor user mappings (see Editing Access to an SSH Server). Groups appear without associated keys (since keys are associated with the member users, not the groups). Users may appear here without associated keys if the user account has been used to grant ownership on a server group but the user has not requested an SSH key pair![]() In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key..
In asymmetric cryptography, public keys are used together in a key pair with a private key. The private key is retained by the key's creator while the public key is widely distributed to any user or target needing to interact with the holder of the private key..
On this tab you can see the keys associated with each user and create mappings between the users and Linux logons in order to allow the orchestrator![]() Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. to publish new SSH keys for those users to the SSH servers associated with the selected Linux logons (see SSH).
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. to publish new SSH keys for those users to the SSH servers associated with the selected Linux logons (see SSH).
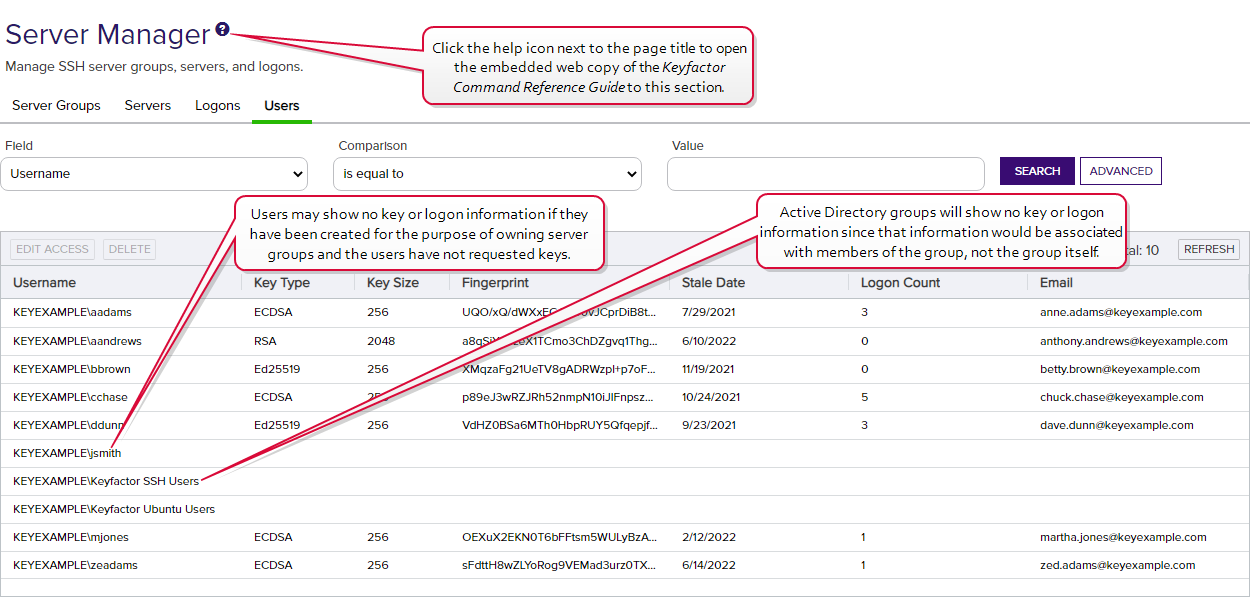
Figure 332: SSH Users Grid

