Keyfactor Command can use either a client certificate or an OAuth access token to authenticate to the EJBCA certificate authority![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. to support certificate synchronization, enrollment
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. to support certificate synchronization, enrollment![]() Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA)., and revocation. if you opt to use a certificate, you will need to obtain a client certificate. The certificate that Keyfactor Command uses for authentication needs:
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA)., and revocation. if you opt to use a certificate, you will need to obtain a client certificate. The certificate that Keyfactor Command uses for authentication needs:
-
An extended key usage (EKU) of Client Authentication
-
A key usage that includes Digital Signature
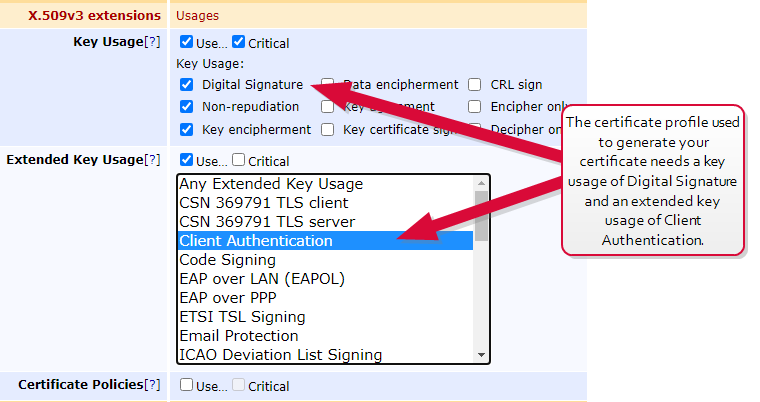
Figure 603: Certificate Profile for EJBCA Client Certificate
The certificate needs to be available as a PKCS#12![]() A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. (*.pfx) file in order to import it into Keyfactor Command.
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. (*.pfx) file in order to import it into Keyfactor Command.
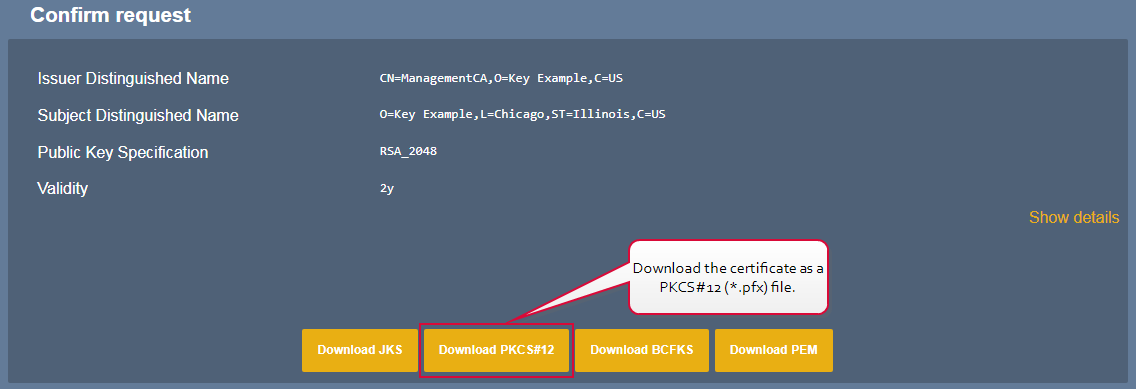
Figure 604: Certificate Download for EJBCA Client Certificate
The certificate needs to be granted appropriate access to the EJBCA CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. to allow Keyfactor Command interactions with the CA to take place (see Grant the Keyfactor Command Users and Service Account(s) Permissions on the CAs).
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. to allow Keyfactor Command interactions with the CA to take place (see Grant the Keyfactor Command Users and Service Account(s) Permissions on the CAs).
Was this page helpful? Provide Feedback