The Keyfactor AnyCA Gateway REST is hosted using IIS by default. By default, AnyCAGateway REST is installed in the Default Web Site, in the virtual directory AnyGatewayREST, using the AnyGatewayREST application pool, in the path: C:\Program Files\Keyfactor\AnyGatewayREST\AnyGatewayREST\net8.0. If you expect to install it in any other configuration, you will need to create the IIS site, as desired, prior to installation, and reference the configuration in the install script parameters.
To configure the AnyCAGateway REST IIS site:
-
Install IIS. The AnyCAGateway REST requires only the default IIS features for operation and requires neither Windows Integrated nor Basic authentication. The correct PowerShell command to install the necessary roles and features is:
CopyInstall-WindowsFeature Web-Server, Web-Asp-Net45, Web-Default-Doc, Web-Dir-Browsing, Web-Http-Errors, Web-Static-Content, Web-Http-Logging, Web-Stat-Compression, Web-Filtering, Web-Net-Ext45, Web-ISAPI-Ext, Web-ISAPI-Filter, Web-Mgmt-Console -
Create a web site if you're not going to use the default web site.
- Set up an HTTPS Binding on the site. Use an SSL
 TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate for the machine you are on or issue one to use if you have not already done so.
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificate for the machine you are on or issue one to use if you have not already done so. - Give database permissions to the user running the application pool on the your SQL server.
Troubleshooting Tips
If you encounter any errors when trying to access the portal, check the Windows Event Log on the AnyCAGateway REST server in addition to the AnyCAGateway REST.
403.16 Error
You may receive a 403.16 error while trying to authenticate the AnyCAGateway REST using certificate authentication. On the face of it, this error indicates that the chain for the certificate you're using to authenticate is not trusted by the AnyCAGateway REST server. First, check to be sure that your certificate is trusted by the AnyCAGateway REST server. But if your certificate is fully trusted and you're still getting this error, what then?
This error can indicate that the trusted root store on the AnyCAGateway REST server contains a certificate that is not a root certificate (for example, an intermediate certificate is accidentally in the root store). To check this, open the Local Computer certificates MMC on the AnyCAGateway REST server, drill down to Certificates under the Trusted Root Certificate Authorities and scan for any certificates where the Issued To does not match the Issued By. Remove any certificates you find like this.
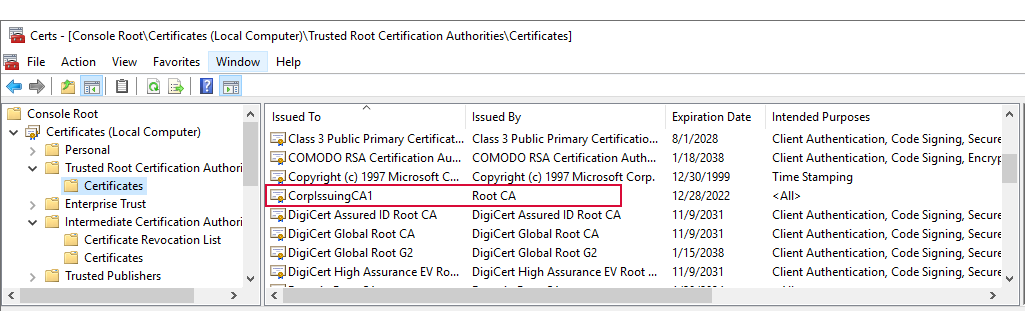
Figure 794: Certificate Incorrectly in the Trusted Root Certificate Store
Additional Setup for Windows Server 2022
If you’re on a version of Windows Server that has TLS![]() TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. 1.3, ensure it is disabled on the site that is hosting the AnyCAGateway REST application. That setting can be found here:
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. 1.3, ensure it is disabled on the site that is hosting the AnyCAGateway REST application. That setting can be found here:
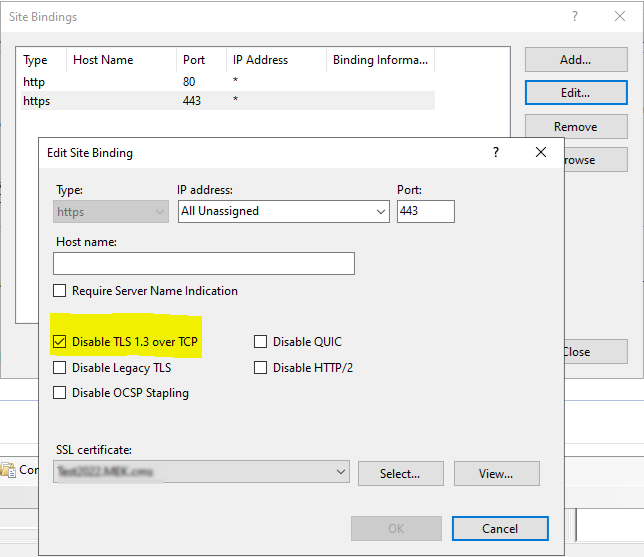
Figure 795: Disable TLS 1.3 over TCP
Was this page helpful? Provide Feedback