In order to allow the Keyfactor CA Connector![]() The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. to make a connection to the CA
The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. to make a connection to the CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. to read certificate records, enroll for new certificates, and perform management functions such as revocation, the service account configured for CA Connection Access (see CA Connection Access) must be granted appropriate permissions to the CA database.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. to read certificate records, enroll for new certificates, and perform management functions such as revocation, the service account configured for CA Connection Access (see CA Connection Access) must be granted appropriate permissions to the CA database.
Microsoft CAs
In the Microsoft management console (MMC) for each CA that a CA Connector Client will interact with, open the properties for the CA and grant the CA connection service account (see CA Connection Access):
-
Read permissions to allow it to synchronize certificates from the CA
-
Request Certificates to allow it to request certificates from the CA
-
Issue and Manage Certificates to allow it to perform workflow
 A workflow is a series of steps necessary to complete a process. In Keyfactor Command, it refers to the workflow builder, which allows you to automate event-driven tasks such as when a certificate is requested, revoked or found in a certificate store. tasks and revocation
A workflow is a series of steps necessary to complete a process. In Keyfactor Command, it refers to the workflow builder, which allows you to automate event-driven tasks such as when a certificate is requested, revoked or found in a certificate store. tasks and revocation
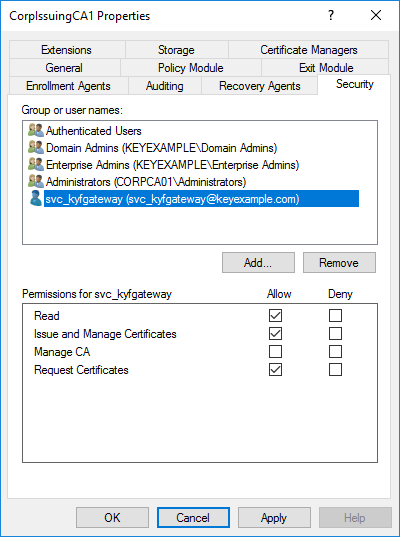
Figure 704: Grant CA Permissions for a Microsoft CA
EJBCA CAs
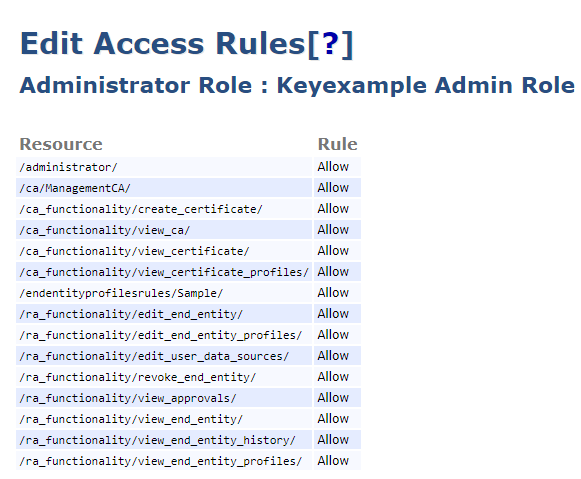
In the EJBCA administration portal for each CA that a CA Connector Client will interact with, create or select a role that the end entity associated with the certificate or OAuth provider that is used to make the connection from the CA Connector Client (see CA Connection Access) will hold and make certain that the access rules for that role include the permissions shown in Figure 705: Grant CA Permissions for an EJBCA CA. The end entity or OAuth provider must hold all the roles shown for full functionality (where Sample is the name of your end entity profile). You may wish to grant the /ra_functionality/create_end_entity/ permission to allow the end entity to create new end entities, which is useful during configuration.
Was this page helpful? Provide Feedback