Task Queue Connection
On the Task Queue Connection page, you enter information to provide Keyfactor Command with the necessary information to communicate with your instance of RabbitMQ. This information is generally configured during your initial Keyfactor Command configuration, but it may be configured or modified here.
Important: If you make changes to the task queue configuration, a restart of the web server and Keyfactor Command services on the Keyfactor Command server is required to clear any cached data and complete the change.
Tip: The following permissions (see
Security Roles and Claims) are required to use this feature:
System Settings > Read
System Settings > Modify
To configure or modify the task queue connection information:
- In the Management Portal, browse to System Settings Icon
 > Task Queue Connection.
> Task Queue Connection.
- On the Task Queue Connection page in the Login Type dropdown, select either Basic (username and password) or OAuth. The remaining fields will vary depending on the selection you make here.
-
In the Task Queue URL, enter the amqp or amqps URL to the RabbitMQ instance. For example:
amqps://appsrvr12.keyexample.com
Keyfactor strongly recommends that if you choose the Basic option, you connect to RabbitMQ over a secure channel (amqps).
-
If you selected Basic, click Set Password, and in the Password dialog, choose from  Load from Keyfactor Secrets or
Load from Keyfactor Secrets or  Load From PAM Provider.
Load From PAM Provider.
Select the Load From Keyfactor Secrets radio button if you want Keyfactor Command to encrypt and store the password in the Keyfactor Command database as a secret. Enter and confirm password in the Secret Value field.
Important: Keyfactor highly recommends that you use strong passwords for any accounts or certificates related to Keyfactor Command and associated products, especially when these have elevated or administrative access. A strong password has at least 12 characters (more is better) and multiple character classes (lowercase letters, uppercase letters, numeral, and symbols). Ideally, each password would be randomly generated. Avoid password re-use.
Tip: A
Keyfactor secret is a user-defined password or other information that is encrypted and stored securely in the
Keyfactor Command database. Although
Keyfactor recommends using Privileged Access Management (see
Privileged Access Management (PAM)) as a more secure solution to secure information,
Keyfactor Secret has historically been an option for customers that don’t already have a relationship with a PAM provider such as CyberArk or Delinea/Thycotic. More recent versions of
Keyfactor Command offer
Keyfactor Command local PAM databases, allowing you to store secrets in the
Keyfactor Command database using PAM.
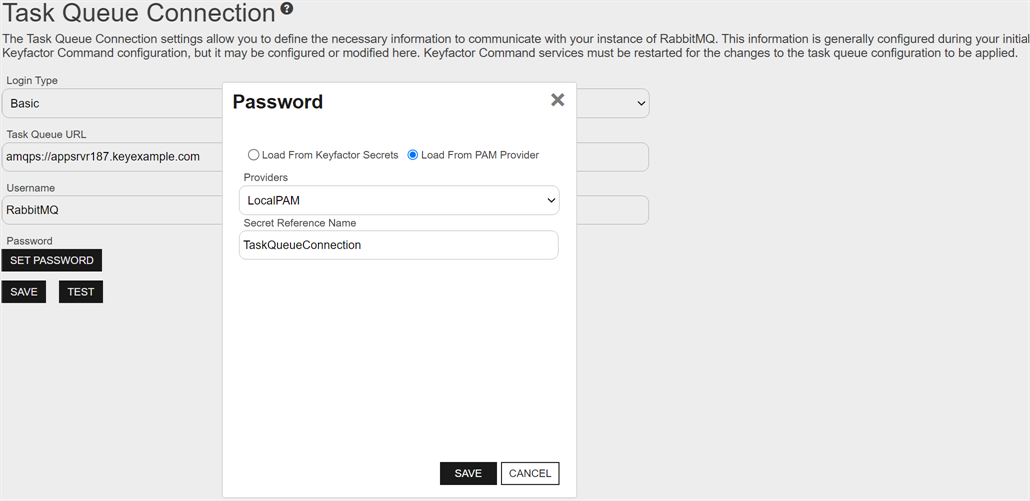
Figure 439: Task Queue Connection: Basic Authentication
Select the Load from PAM Provider radio button if you want to store the password in a Keyfactor Command local or supported third-party PAM solution (see Privileged Access Management (PAM)). The remaining fields on the dialog will vary depending on the PAM provider. For example:
 Keyfactor Command Local Database
Keyfactor Command Local Database
Select your Keyfactor Command local database provider in the Providers dropdown. The remaining field in the dialog will then be:
 CyberArk
CyberArk
Select your CyberArk provider in the Providers dropdown if your PAM provider is CyberArk (see Adding or Modifying a PAM Provider). The remaining fields in the dialog will then be:
- PrivateArk Folder Name —The path and name of the folder that stores the secret (e.g. Root or Root\MyDir).
- PrivateArk Protected Password Name —The name of the username or password to use for this instance.
 Delinea/Thycotic
Delinea/Thycotic
Select your Delinea/Thycotic provider in the Providers dropdown if your PAM provider is Delinea /Thycotic (see Adding or Modifying a PAM Provider). The remaining field in the dialog will then be:
- Thycotic Secret ID—The numeric ID of the secret to retrieve from provider server.
 Hashicorp
Hashicorp
Select your Hashicorp Vault provider in the Providers dropdown if your PAM provider is Hashicorp Vault (see Adding or Modifying a PAM Provider). The remaining fields in the dialog will then be:
- KV Secret Key—The key of the secret to retrieve from the Hashicorp Vault.
- KV Secret Name—The name of the secret to retrieve from the Hashicorp Vault.
-
If you selected OAuth, enter the following information:
-
Client Id
The client you created in your OAuth identity provider to authenticate to your RabbitMQ instance. If you’re using Keyfactor Identity Provider, see Service Accounts for help creating a client account.
-
Token URL
Set this to the URL of the token for your OAuth identity provider. For example:
https://my-keyidp-server.keyexample.com/realms/Keyfactor/protocol/openid-connect/token
-
Client Secret
The secret of the client you created in your OAuth identity provider to authenticate to your RabbitMQ instance. Click the Set/Update Client Secret button and in the Client Secret dialog, choose from  Load from Keyfactor Secrets or
Load from Keyfactor Secrets or  Load From PAM Provider.
Load From PAM Provider.
Select the Load From Keyfactor Secrets radio button if you want Keyfactor Command to encrypt and store the password in the Keyfactor Command database as a secret. Enter and confirm password in the Secret Value field.
Important: Keyfactor highly recommends that you use strong passwords for any accounts or certificates related to Keyfactor Command and associated products, especially when these have elevated or administrative access. A strong password has at least 12 characters (more is better) and multiple character classes (lowercase letters, uppercase letters, numeral, and symbols). Ideally, each password would be randomly generated. Avoid password re-use.
Tip: A
Keyfactor secret is a user-defined password or other information that is encrypted and stored securely in the
Keyfactor Command database. Although
Keyfactor recommends using Privileged Access Management (see
Privileged Access Management (PAM)) as a more secure solution to secure information,
Keyfactor Secret has historically been an option for customers that don’t already have a relationship with a PAM provider such as CyberArk or Delinea/Thycotic. More recent versions of
Keyfactor Command offer
Keyfactor Command local PAM databases, allowing you to store secrets in the
Keyfactor Command database using PAM.
Select the Load from PAM Provider radio button if you want to store the password in a Keyfactor Command local or supported third-party PAM solution (see Privileged Access Management (PAM)). The remaining fields on the dialog will vary depending on the PAM provider. For example:
 Keyfactor Command Local Database
Keyfactor Command Local Database
Select your Keyfactor Command local database provider in the Providers dropdown. The remaining field in the dialog will then be:
 CyberArk
CyberArk
Select your CyberArk provider in the Providers dropdown if your PAM provider is CyberArk (see Adding or Modifying a PAM Provider). The remaining fields in the dialog will then be:
- PrivateArk Folder Name —The path and name of the folder that stores the secret (e.g. Root or Root\MyDir).
- PrivateArk Protected Password Name —The name of the username or password to use for this instance.
 Delinea/Thycotic
Delinea/Thycotic
Select your Delinea/Thycotic provider in the Providers dropdown if your PAM provider is Delinea /Thycotic (see Adding or Modifying a PAM Provider). The remaining field in the dialog will then be:
- Thycotic Secret ID—The numeric ID of the secret to retrieve from provider server.
 Hashicorp
Hashicorp
Select your Hashicorp Vault provider in the Providers dropdown if your PAM provider is Hashicorp Vault (see Adding or Modifying a PAM Provider). The remaining fields in the dialog will then be:
- KV Secret Key—The key of the secret to retrieve from the Hashicorp Vault.
- KV Secret Name—The name of the secret to retrieve from the Hashicorp Vault.
-
Scope
One or more scopes that should be included in token requests delivered to your OAuth identity provider. This is not required when using Keyfactor Identity Provider.
-
Audience
Specify an audience value to be included in token requests delivered to your OAuth identity provider. This is not required when using Keyfactor Identity Provider.
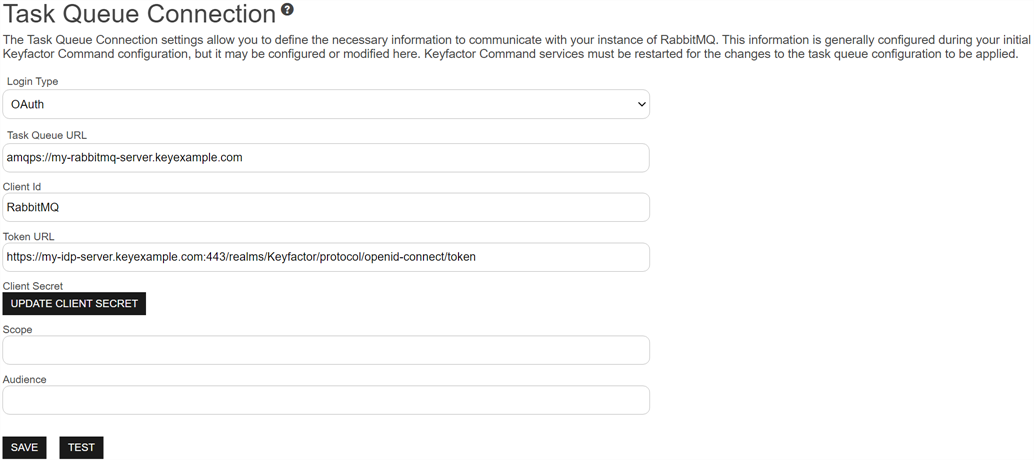
Figure 440: CA OAuth Task Queue Connection
- Click Save to save any changes. Click Test to validate that the entered information can be used to make a connection to RabbitMQ.
 > Task Queue Connection.
> Task Queue Connection. Load from Keyfactor Secrets or
Load from Keyfactor Secrets or  Load From PAM Provider.
Load From PAM Provider. An endpoint is a URL that enables the API to gain access to resources on a server. for your OAuth identity provider. For example:https://my-keyidp-server.keyexample.com/realms/Keyfactor/protocol/openid-connect/token
An endpoint is a URL that enables the API to gain access to resources on a server. for your OAuth identity provider. For example:https://my-keyidp-server.keyexample.com/realms/Keyfactor/protocol/openid-connect/token Load from Keyfactor Secrets or
Load from Keyfactor Secrets or  Load From PAM Provider.
Load From PAM Provider.
