On the identity providers page, you can modify existing identity providers or add new OAuth identity providers. New identity providers can also be added by re-running the Keyfactor Command configuration wizard and adding a new identity provider on the Authentication tab (see Authentication Tab). Identity providers cannot be deleted.
Permissions for identity providers can be set at either the global or identity provider level. See Identity Provider Permissions for more information about global vs identity provider permissions.
To create an identity provider or modify an existing one:
- In the Management Portal, browse to System Settings Icon
 > Identity Providers.
> Identity Providers. - On the Identity Providers page, click Add to add a new identity provider, or click Edit from the top of the grid or from the right click menu to modify an existing provider.
-
On the Add/Editing Identity Provider page, fill in each tab of the dialog with the information desired for the selected identity provider.
-
On the Details tab, select a Type in the dropdown. Most identity providers can be supported with the Generic type. For Auth0, select the Auth0 type.
Enter a short name for the provider in the Authentication Scheme and a longer name in the Display Name. The Type and Authentication Scheme cannot be modified on an edit.
Important: The value in the Authentication Scheme field must match the provider name referenced in redirect URLs.In the Permission Set dropdown, select a permission set to apply to the identity provider. For more information about permission sets, see Permission Sets.
The Enable toggle only appears when editing an existing identity provider. Newly added identity providers are always enabled. Existing identity providers may be disabled, if desired. Identity providers cannot be disabled if the provider is used as the default identity provider for login or as the Identity Provider Name selected in the Identity Provider Token Credentials section of the Authentication tab in the configuration wizard. When an identity provider is disabled, the following will not be available for that identity provider:
-
Users cannot authenticate to the Keyfactor Command Management Portal or Keyfactor API
 An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. using a disabled identity provider.
An API is a set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. using a disabled identity provider. -
Orchestrators cannot authenticate against the Orchestrators API using a disabled identity provider.
-
On the Orchestrator
 Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. Management page, the orchestrators last seen time will not update when the orchestrator is configured to use a disabled identity provider.
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. Management page, the orchestrators last seen time will not update when the orchestrator is configured to use a disabled identity provider. -
Instances of the CA Connector
 The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. Client cannot authenticate against the CA
The Keyfactor CA Connector is installed in the customer environment to provide a connection between a CA and Keyfactor Command when a direct connection is not possible. It is supported on both Windows and Linux and has versions for Microsoft (Windows only) or EJBCA CAs. Client cannot authenticate against the CA A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. Connector API using a disabled identity provider.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. Connector API using a disabled identity provider. -
On the Certificate Authority
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. CA Connector page, CA connectors will display as not connected for CA Connector Clients using a disabled identity provider.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. CA Connector page, CA connectors will display as not connected for CA Connector Clients using a disabled identity provider. -
On the Application Settings page on the Console tab, only enabled identity providers will appear in the dropdown for the Default Identity Provider application setting.
-
In the configuration wizard, only enabled identity providers will appear in the dropdowns for the Identity Provider in the Identity Provider section and the Identity Provider Name in the Identity Provider Token Credentials section of the Authentication tab.
Note: In order to view or edit an identity provider in the Keyfactor Command Management Portal or with the Keyfactor API, a user must be assigned a security role that has been granted the Identity Providers > Read and Identity Providers > Modify (for edits) permissions and that has the same permission set applied to it as has been applied to the identity provider.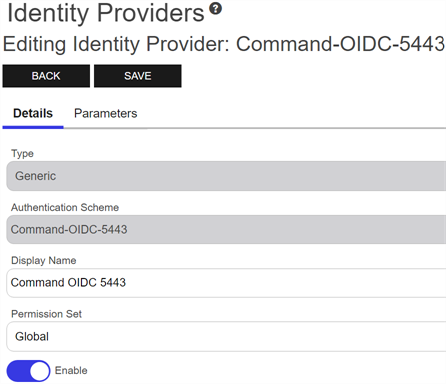
Figure 437: Details for an Identity Provider
-
-
On the Parameters tab, select each parameter
 A parameter or argument is a value that is passed into a function in an application. to configure and click Edit to open the Edit <Parameter Name> Parameter dialog, the contents of which will vary depending on the parameter selected. For information about the specific parameters, see Table 86: Identity Provider Parameters.
A parameter or argument is a value that is passed into a function in an application. to configure and click Edit to open the Edit <Parameter Name> Parameter dialog, the contents of which will vary depending on the parameter selected. For information about the specific parameters, see Table 86: Identity Provider Parameters.Click Import Discovery Document to enter the discovery URL for the identity provider and automatically populate the Authority, AuthorizationEndpoint, TokenEndpoint, JSONWebKeySetUri, and UserInfoEndpoint fields. Click Fetch to retrieve the information and Save to save it to the identity provider form.
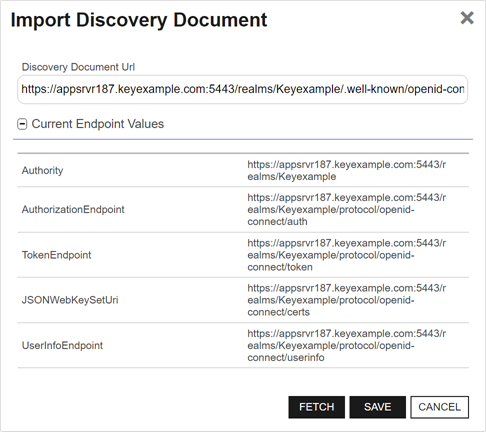
Figure 438: Import Discovery Document for an Identity Provider
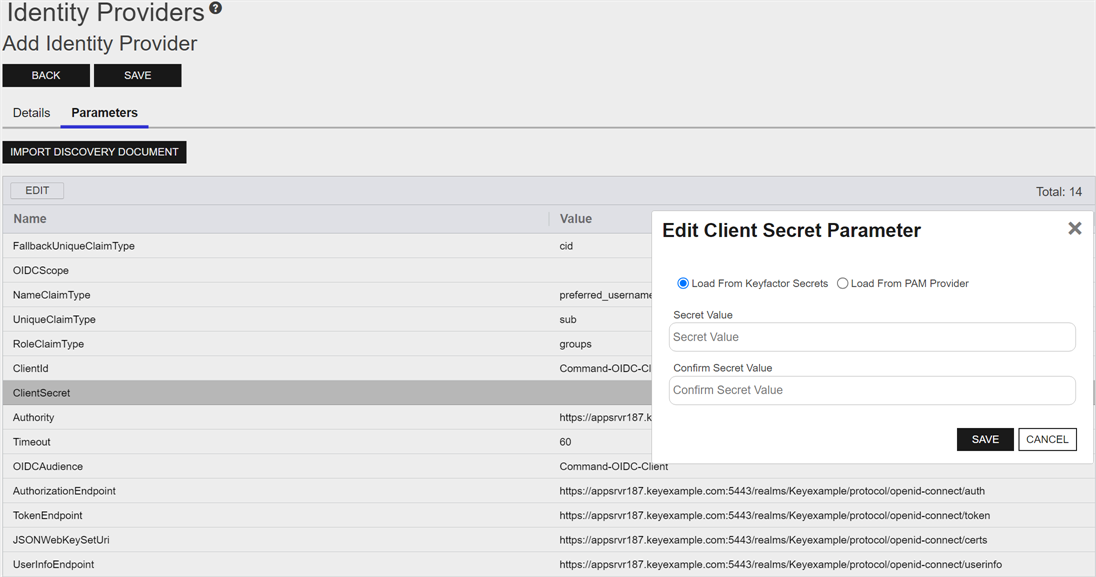
Figure 439: Edit Parameters for an Identity Provider
-
- Click Save to save the identity provider.
Table 86: Identity Provider Parameters
| Name | Example |
Description |
|---|---|---|
|
|
Command- OIDC- Client |
The audience value for tokens issued from the identity provider. For Keyfactor Identity Provider, this should be set to the same value as the Client Id. For example: Command- OIDC- Client
This parameter is required. |
|
|
The unique identifier defined in Auth0 or a similar identity provider for the API. This parameter only appears if Auth0 is selected as the type and is required in that case. |
|
| Authority | https:// my-keyidp-server .keyexample.com /realms /Keyfactor |
The issuer/authority endpoint URL for the identity provider. This parameter is required. Tip: When you add or update an identity provider, the provider’s discovery document is validated based on this authority URL. The discovery document is also validated periodically in the background. The following are validated:
If any of these validation tests fail, any identity provider changes in process will not be saved and an error will be displayed or logged. |
|
|
https:// my-keyidp-server .keyexample.com /realms /Keyfactor /protocol /openid-connect /auth |
The authorization endpoint URL for the identity provider. This parameter is required. |
|
|
Command- OIDC- Client |
The ID of the client application created in the identity provider for primary application use. For Keyfactor Identity Provider, this should be: Command- OIDC- Client
For more information, see Configuring Keyfactor Identity Provider and Collecting Data for the Keyfactor Command Installation). This parameter is required. |
| ClientSecret |
The specific secret value This parameter is required. |
|
|
|
https:// my-keyidp-server .keyexample.com /realms /Keyfactor /.well-known /openid-configuration |
The discovery URL for the identity provider. If you opt not to populate this field or if the discovery document does not return a valid response, the remainder of the fields in this section of the configuration will need to be configured manually. This value is not stored in the database. This field does not appear in the Management Portal identity provider configuration. |
|
|
cid |
A type of user claim for the identity provider containing a backup unique name for the user. This is provided in case the primary referenced name (see cid
The cid (client ID) user claim type is also commonly used by other OAuth providers. This parameter is required. |
|
|
https:// my-keyidp-server .keyexample.com /realms /Keyfactor /protocol /openid-connect /certs |
The JWKS (JSON Web Key Set) URL for the identity provider. This parameter is required. |
| preferred_ username |
A type of user claim for the identity provider containing a friendly name for the user. Although the value for this field may not necessarily be unique within your identity provider (so might resolve to John Smith and the organization might have two users called John Smith), this can be confusing in Keyfactor Command, since the value is used as the user’s display name in areas such as the requester of a certificate, actors in audit logs, and users referenced in workflow instances. It is best to avoid duplicates. For Keyfactor Identity Provider, this should be: preferred_ username
For Okta, this might be preferred_names (e.g. john.smith@keyexample.com) or just name (e.g. John Smith). For Auth0 this might be name (e.g. johnsmith@keyexample.com). This parameter is required. Tip: The value in this field is used as the first choice to populate the username in the Keyfactor Command Management Portal header, if available. This is not the value to use when logging into Keyfactor Command. For that, see
|
|
| groups |
The value used to reference the type of group claim for the identity provider. For Keyfactor Identity Provider, this should be: groups
This parameter is required. |
|
|
|
One or more scopes that are requested during the OIDC protocol when Keyfactor Command is the relying party. Multiple scopes should be separated by spaces. This value is not used for Keyfactor Identity Provider. |
|
|
|
https:// my-auth0-instance .us.auth0.com /oidc/logout |
The signout URL for the identity provider. This parameter only appears if Auth0 is selected as the type and is required in that case. |
| Timeout | 60 | The number of seconds a request to the identity provider is allowed to process before timing out with an error. |
|
|
An audience value to be included in token requests delivered to the identity provider when making a token request where Keyfactor Command is acting as the OAuth client. This value is not used for Keyfactor Identity Provider. |
|
|
|
https:// my-keyidp-server .keyexample.com /realms /Keyfactor /protocol /openid-connect /token |
The token endpoint URL for the identity provider. This parameter is required. |
|
|
One or more scopes that should be included in token requests delivered to the identity provider when making a token request where Keyfactor Command is acting as the OAuth client. Multiple scopes should be separated by spaces. This value is not used for Keyfactor Identity Provider. |
|
|
|
sub |
A type of user claim for the identity provider containing a unique name for the user. For Keyfactor Identity Provider, this should be: sub
In Keyfactor Identity Provider, this is a GUID uniquely identifying the user. The sub (subject) user claim type is also commonly used by other OAuth providers. See also This parameter is required. Tip: The value in this field is used as the second choice to populate the username in the Keyfactor Command Management Portal header if the
The value in this field is the one to use when logging into Keyfactor Command. |
|
|
https:// my-keyidp-server .keyexample.com /realms /Keyfactor /protocol /openid-connect /certs |
The user info endpoint URL for the identity provider. |